Threat Actors Impersonate Microsoft OAuth Apps to Steal Login Credentials
Threat actors are leveraging sophisticated phishing campaigns by creating fake Microsoft OAuth applications to impersonate legitimate enterprises, enabling credential theft while bypassing multifactor authentication (MFA).
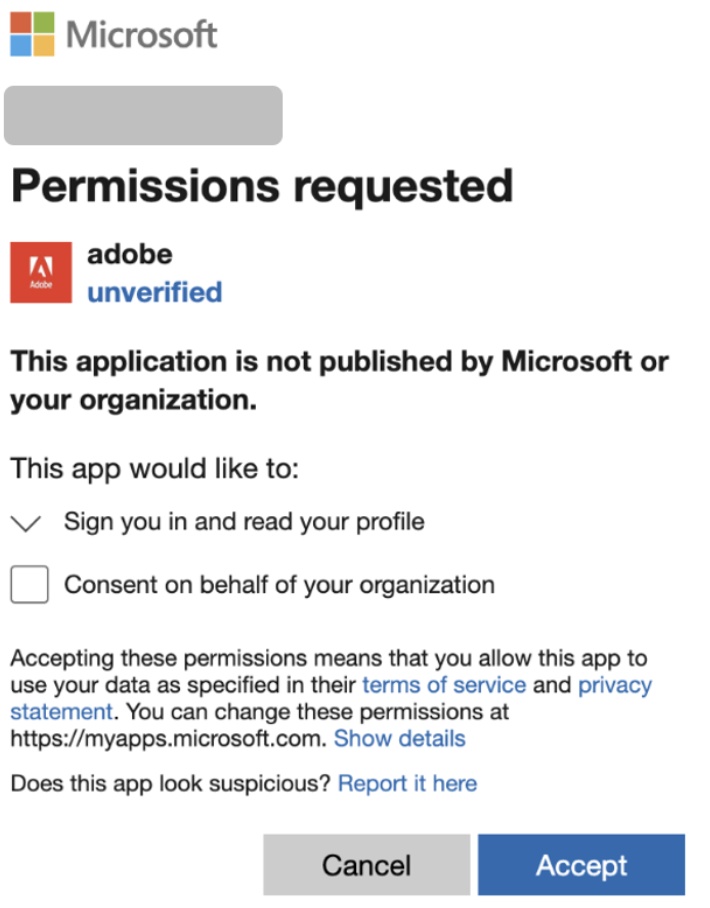
Proofpoint researchers have tracked this activity since early 2025, identifying over 50 impersonated applications, including those mimicking RingCentral, SharePoint, Adobe, and DocuSign.
These malicious OAuth apps serve as initial lures, redirecting users to attacker-in-the-middle (AiTM) phishing kits like Tycoon and ODx, which capture credentials and session cookies in real time.

The campaigns exploit OAuth consent flows, requesting benign scopes such as viewing basic profiles or maintaining data access, but regardless of user consent, victims are funneled to counterfeit Microsoft login pages branded with their organization’s Entra ID details.
This AiTM approach proxies authentication requests, intercepting MFA tokens and enabling account takeovers (ATOs) for purposes like information gathering, lateral movement, or further phishing from compromised accounts.
Campaign Overview and Techniques
Proofpoint has reported these apps to Microsoft, and upcoming changes in Microsoft 365 such as blocking legacy authentication and requiring admin consent for third-party apps starting mid-July 2025 are expected to disrupt this tactic significantly.
Emails in these campaigns often originate from compromised accounts, using lures themed around requests for quotes or business contracts, targeting thousands of messages across hundreds of organizations.
Customization occurs based on industry, with impersonations tailored to specific software, amplifying relevance and success rates.
In cloud tenant data, Proofpoint observed over two dozen similar malicious apps, primarily requesting scopes like openid, email, and profile, with reply URLs leading to phishing infrastructure.
While most apps acted as lures without direct compromise capabilities, ATOs were confirmed in only five cases, indicating a low but targeted success rate exceeding 50% in broader Tycoon-linked operations affecting nearly 3,000 accounts across 900 environments in 2025.
Infrastructure Insights
A March 2025 campaign targeted a U.S.-based aviation firm, impersonating ILSMart an aerospace inventory service with OAuth app “iLSMART” requesting basic profile access and data maintenance permissions.
Redirects led to CAPTCHA challenges and Tycoon-powered fake Microsoft pages that harvested credentials and MFA tokens via synchronous relays.
Configuration details included reply URLs like azureapplicationregistration[.]pages[.]dev/redirectapp and scopes focused on user profile visibility.
Similarly, a June 2025 Adobe impersonation used SendGrid-delivered emails redirecting through intermediate URLs to an OAuth “Redirector App,” ultimately landing on Tycoon phishing pages with parameters like client_id 854189f9-4c71-44bb-9880-dd0c2f75922a and scopes including openid+email+profile.

Cloud impacts revealed clusters like a fake “Adobe” app affecting four users via reply URL workspacesteamworkspace[.]myclickfunnels[.]com/offices–af295, with Axios user agents (e.g., axios/1.7.9) signaling Tycoon involvement.
Another incident with “OneDrive-2025” used cleansbeauty[.]com/lost/apc.html, followed by MFA manipulations like adding security methods for persistence.
Tycoon, a phishing-as-a-service platform, employs Axios HTTP clients for exploitation, shifting infrastructure in April 2025 from Russian proxies to U.S.-based data center hosting to evade detection.
Proofpoint notes this as part of a broader trend toward identity-targeted AiTM attacks, recommending defenses like email security for BEC prevention, cloud monitoring for ATO detection, web isolation, user awareness, and FIDO keys.
Indicators of Compromise
| Indicator | Description | First Seen |
|---|---|---|
| hxxps[:]//azureapplicationregistration[.]pages[.]dev/redirectapp | Redirector to Tycoon | 18 March 2025 |
| yrqwvevbjcfv[.]es | Tycoon Landing Domain | 18 March 2025 |
| gmlygt[.]ru | Tycoon Antibot (Example) | 18 March 2025 |
| 2a00:b703:fff2:35::1 | Example of Signin Facing IP for Tycoon | 18 March 2025 |
| hxxps://chikeukohandco[.]com/saas/Index.html | Redirector to Tycoon | 12 June 2025 |
| pw5[.]haykovx[.]es | Tycoon Landing Domain | 12 June 2025 |
| 14b2864e-3cff-4d33-b5cd-7f14ca272ea4 | Malicious Microsoft OAuth Application ID | 27 January 2025 |
| 85da47ec-2977-40ab-af03-f3d45aaab169 | Malicious Microsoft OAuth Application ID | 04 February 2025 |
| 355d1228-1537-4e90-80a6-dae111bb4d70 | Malicious Microsoft OAuth Application ID | 19 February 2025 |
| 6628b5b8-55af-42b4-9797-5cd5c148313c | Malicious Microsoft OAuth Application ID | 19 February 2025 |
| b0d8ea55-bc29-436c-9f8b-f8829030261d | Malicious Microsoft OAuth Application ID | 04 March 2025 |
| 22c606e8-7d68-4a09-89d9-c3c563a453a0 | Malicious Microsoft OAuth Application ID | 11 March 2025 |
| 31c6b531-dd95-4361-93df-f5a9c906da39 | Malicious Microsoft OAuth Application ID | 11 March 2025 |
| 055399fa-29b9-46ab-994d-4ae06f40bada | Malicious Microsoft OAuth Application ID | 18 February 2025 |
| 6a77659d-dd6f-4c73-a555-aed25926a05f | Malicious Microsoft OAuth Application ID | 06 March 2025 |
| 21f81c9e-475d-4c26-9308-1de74a286f73 | Malicious Microsoft OAuth Application ID | 20 February 2025 |
| 987c259f-da29-4575-8072-96c610204830 | Malicious Microsoft OAuth Application ID | 18 March 2025 |
| db2eb385-c02f-44fc-b204-ade7d9f418b1 | Malicious Microsoft OAuth Application ID | 10 March 2025 |
| f99a0806-7650-4d78-acef-71e445dfc844 | Malicious Microsoft OAuth Application ID | 17 March 2025 |
| fdcf7337-92bf-4c70-9888-ea234b6ffb0d | Malicious Microsoft OAuth Application ID | 27 February 2025 |
| fe0e32ca-d09e-4f80-af3c-5b086d4b8e66 | Malicious Microsoft OAuth Application ID | 06 March 2025 |
| axios/1.7.9 | Axios user agent associated with Tycoon activity | 09 December 2024 |
| axios/1.8.2 | Axios user agent associated with Tycoon activity | 10 March 2025 |
Find this News Interesting! Follow us on Google News, LinkedIn, and X to Get Instant Updates!














Post Comment