ToxicPanda Android Banking Malware Compromises Over 4,500 Devices to Harvest Banking Credentials
The ToxicPanda Android banking trojan has emerged as a significant threat, compromising over 4,500 devices…
New XWorm V6 Variant with Anti-Analysis Features Targeting Windows Users in Active Attacks
Netskope Threat Labs has uncovered a new iteration of the XWorm malware, version 6.0, which…
Lazarus Subgroup ‘TraderTraitor’ Targets Cloud Platforms and Contaminates Supply Chains
The North Korean state-sponsored advanced persistent threat (APT) known as TraderTraitor, a subgroup of the…
Infection Chain and Escalation Tactics Exposed
Lumma, a sophisticated C++-based information stealer, has surged in prevalence over recent years, posing significant…
SquareX Discloses Architectural Limitations Of Browser DevTools In Debugging Malicious Extensions
Palo Alto, California, July 29th, 2025, CyberNewsWire Despite the expanding use of browser extensions, the…
Critical CodeIgniter Flaw Exposes Millions of Web Apps to File Upload Attacks
A critical security vulnerability in CodeIgniter4’s ImageMagick handler has been discovered that could allow attackers…
Gemini CLI Vulnerability Allows Silent Execution of Malicious Commands on Developer Systems
Security researchers at Tracebit have discovered a critical vulnerability in Google’s Gemini CLI that enables…
PyPI Alerts Developers to New Phishing Attack Using Fake PyPI Site
Python developers are being warned about a sophisticated phishing campaign targeting users of the Python…
Researchers Reveal Technical Details of SonicWall SMA100 Series N-Day Vulnerabilities
Security researchers have disclosed technical details of three previously patched vulnerabilities affecting SonicWall’s SMA100 series…
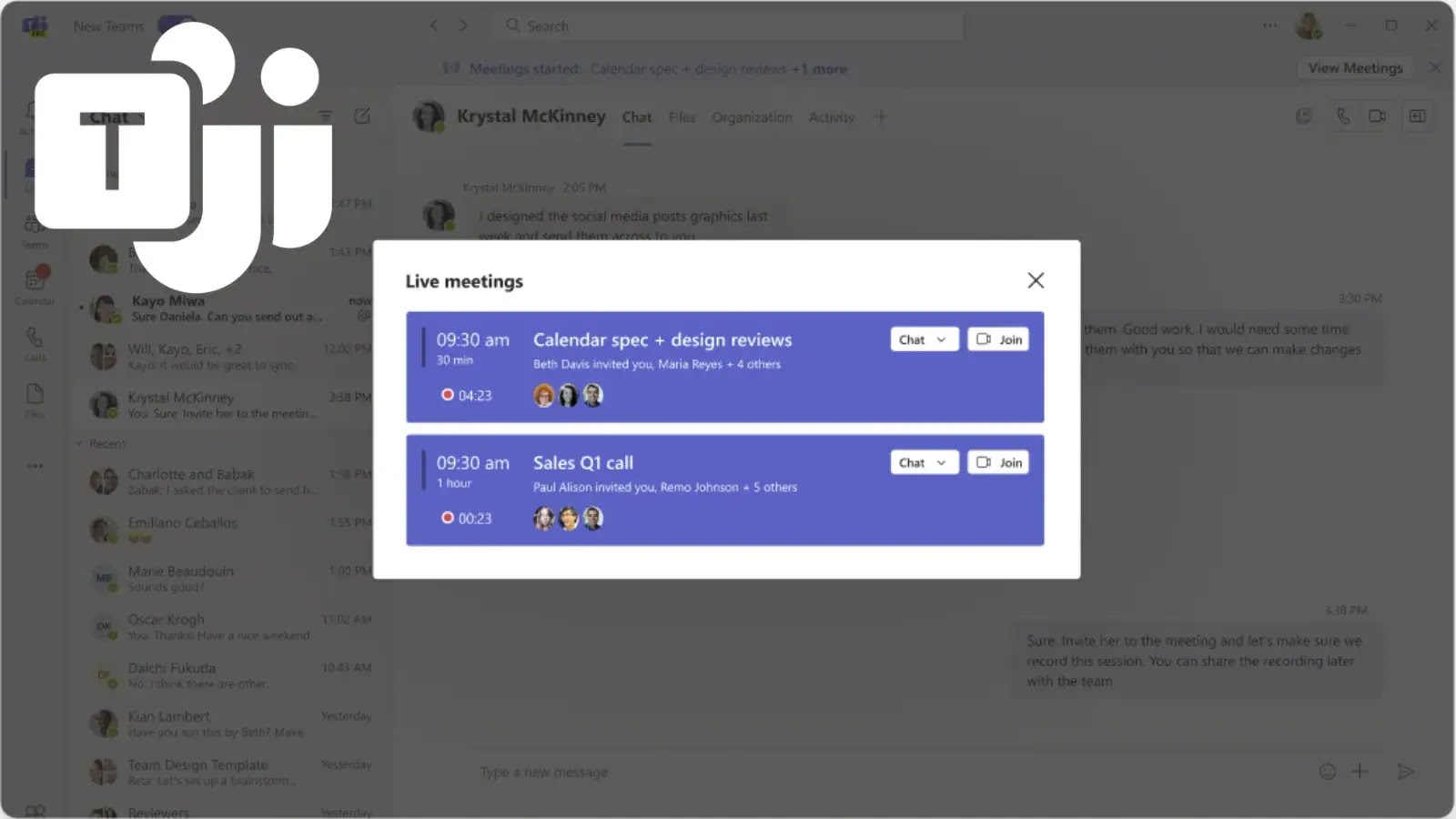
Microsoft Teams Introduces New Join Bar to Help Users Join Meetings on Time
Microsoft Teams is rolling out a new meeting join banner designed to streamline the meeting…