Critical CodeIgniter Flaw Exposes Millions of Web Apps to File Upload Attacks
A critical security vulnerability in CodeIgniter4’s ImageMagick handler has been discovered that could allow attackers…
Gemini CLI Vulnerability Allows Silent Execution of Malicious Commands on Developer Systems
Security researchers at Tracebit have discovered a critical vulnerability in Google’s Gemini CLI that enables…
PyPI Alerts Developers to New Phishing Attack Using Fake PyPI Site
Python developers are being warned about a sophisticated phishing campaign targeting users of the Python…
Researchers Reveal Technical Details of SonicWall SMA100 Series N-Day Vulnerabilities
Security researchers have disclosed technical details of three previously patched vulnerabilities affecting SonicWall’s SMA100 series…
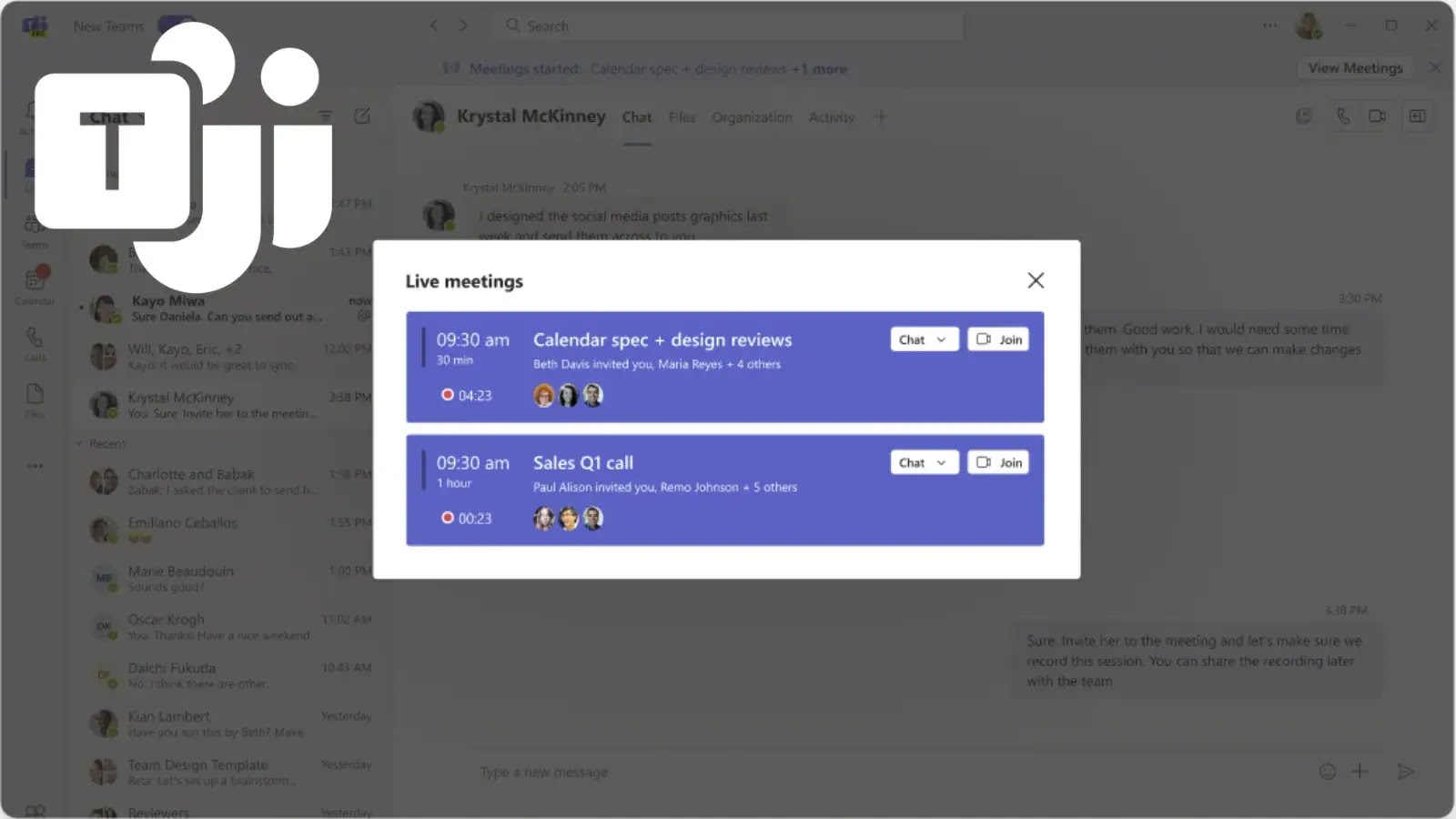
Microsoft Teams Introduces New Join Bar to Help Users Join Meetings on Time
Microsoft Teams is rolling out a new meeting join banner designed to streamline the meeting…
Apple Introduces Containerization Feature for Seamless Kali Linux Integration on macOS
Apple has unveiled a groundbreaking containerization feature that enables seamless integration of Kali Linux on…
PoC Exploit Published for Actively Exploited Cisco Identity Services Engine Flaw
Security researchers have published a detailed proof-of-concept exploit for a critical vulnerability in Cisco Identity…
New macOS Vulnerability Allows Attackers to Steal Private Files by Bypassing TCC
Microsoft Threat Intelligence has uncovered a critical macOS vulnerability that enables attackers to bypass Apple’s…
Linux 6.16 Released with Performance and Networking Enhancements
Linux creator Linus Torvalds announced the release of Linux kernel version 6.16 on July 27,…
Lionishackers Exfiltrate Sensitive Corporate Databases for Sale on the Dark Web
Outpost24’s threat intelligence researchers have uncovered the operations of Lionishackers, a financially motivated cyber threat…