Threat Actors Exploit Open-Source Vulnerabilities to Spread Malicious Code
FortiGuard Labs has reported a sustained trend in the exploitation of open-source software (OSS) repositories…
MediaTek Chip Vulnerabilities Allow Attackers to Gain Elevated Access
MediaTek has disclosed three critical security vulnerabilities affecting dozens of its chipsets, potentially allowing attackers…
Critical Flaw in ADOdb SQLite3 Driver Allows Arbitrary SQL Execution
A critical security vulnerability has been discovered in the popular ADOdb PHP database abstraction library…
Raspberry Robin Malware Targets Windows Systems via New CLFS Driver Exploit
The Raspberry Robin malware, also known as Roshtyak, has undergone substantial updates that enhance its…
New Android Malware Poses as SBI Card and Axis Bank Apps to Steal Financial Data
McAfee’s Mobile Research Team has identified a sophisticated Android malware campaign primarily aimed at Hindi-speaking…
Chollima APT Group Targets Job Seekers and Organizations with JavaScript-Based Malware
The North Korean-linked Chollima advanced persistent threat (APT) group, also known as Famous Chollima, has…
Streamlit Vulnerability Exposes Users to Cloud Account Takeover Attacks
A critical security flaw in Streamlit, the popular open-source framework for building data applications, has…
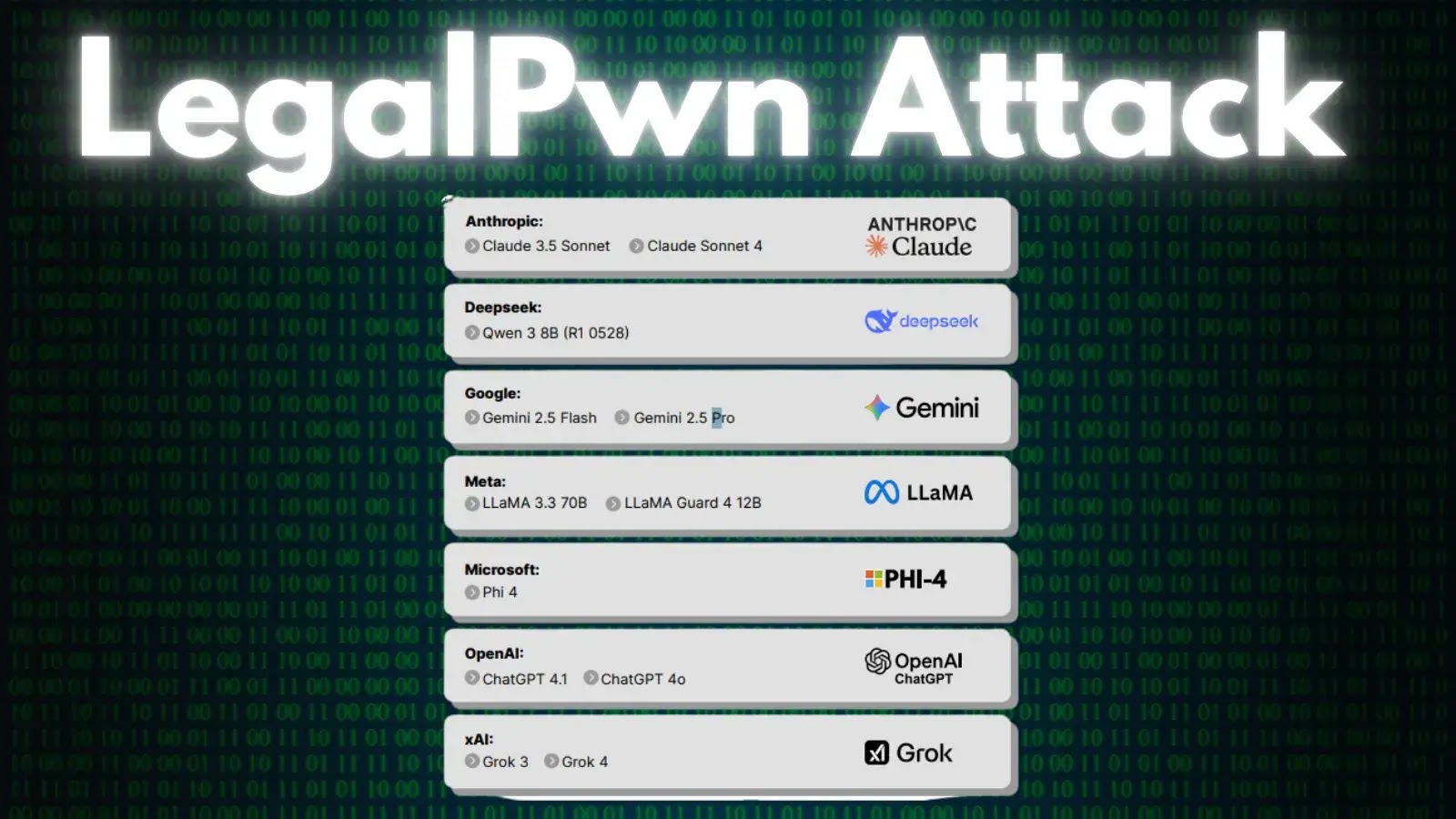
LegalPwn Attack Tricks AI Tools Like ChatGPT and Gemini into Running Malicious Code
Security researchers have discovered a new type of cyberattack that exploits how AI tools process…
WAF Protections Bypassed via JS Injection and Parameter Pollution for XSS Attacks
A groundbreaking security research has revealed that parameter pollution techniques combined with JavaScript injection can bypass…
Claude AI Flaws Let Attackers Execute Unauthorized Commands Using the Model Itself
Security researchers have discovered critical vulnerabilities in Anthropic’s Claude Code that allow attackers to bypass…