Top 10 Best Cybersecurity Compliance Management Software in 2025
Best Cybersecurity Compliance Management Software Cybersecurity compliance has become a mission-critical part of modern business…
Threat Actors Exploit Oracle Database Scheduler to Infiltrate Corporate Networks
Threat actors have begun exploiting the Oracle Database Scheduler’s External Jobs feature to execute arbitrary…
Stellantis Confirms Data Breach Affecting Citroën, Fiat, Jeep, and More
Automotive giant Stellantis has confirmed a significant data breach affecting its North American customer service…
BlockBlasters Steam Game Disguises Malware as Patch for Computer Download
BlockBlasters, a vibrant 2D platformer/shooter from Genesis Interactive, launched on July 31, 2025 to wide…
God Mode Vulnerability Lets Attackers Access Any Resource in Microsoft Cloud Tenants
A recently disclosed flaw, tracked as CVE-2025-55241, allowed any attacker in possession of a single…
BlackLock Ransomware Targets Windows, Linux, and VMware ESXi Systems
BlackLock, a rebranded ransomware group formerly known as El Dorado, has emerged as a formidable…
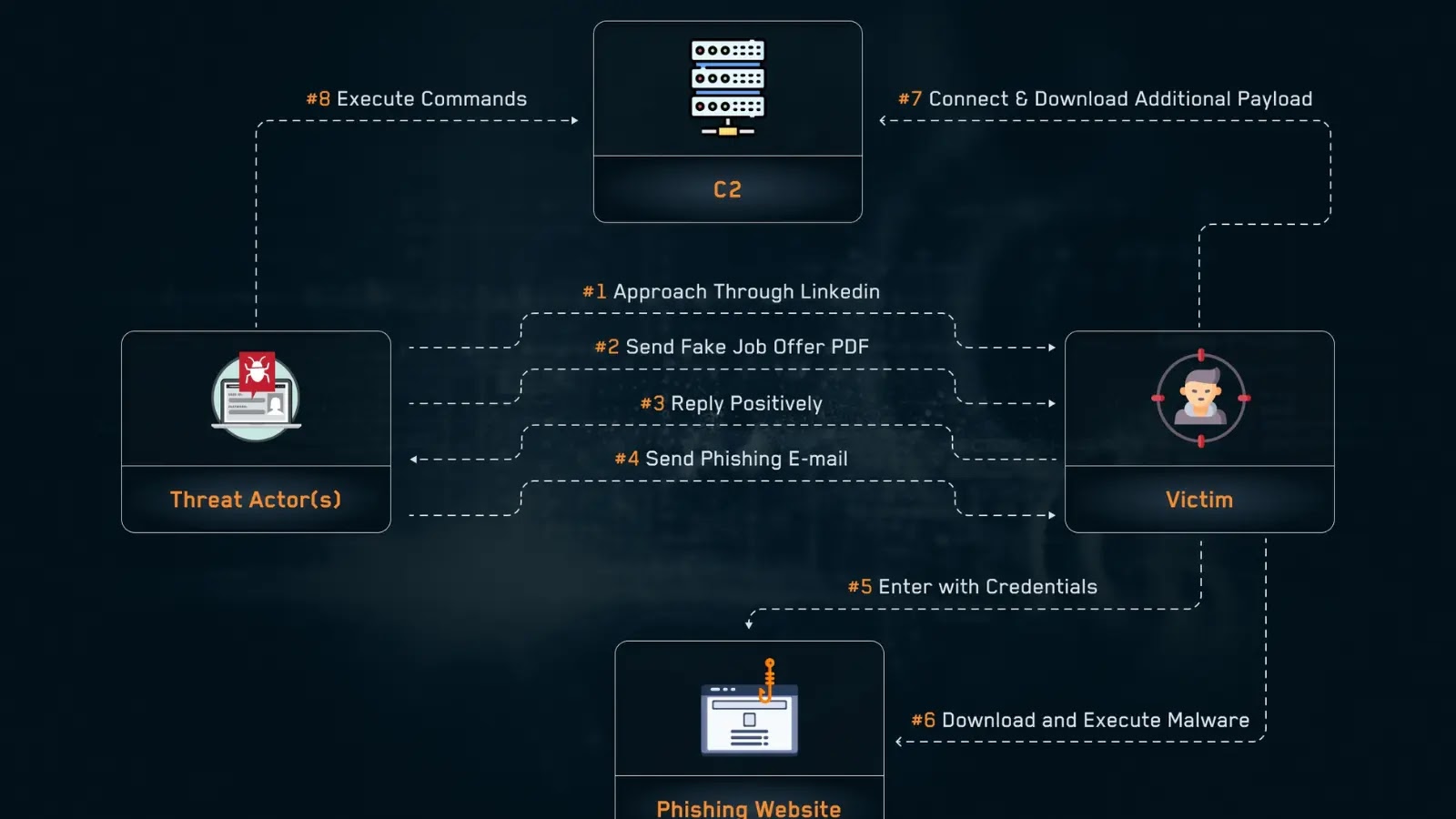
How HR Representatives Can Engage Employees to Steal Login Credentials
Subtle Snail, an Iran-linked espionage group also tracked as UNC1549 under the Unyielding Wasp (Tortoiseshell)…
Code Analysis Published for Chrome Type Confusion 0-Day Vulnerability
Google Chrome’s V8 JavaScript engine has long balanced speed and security for billions of users…
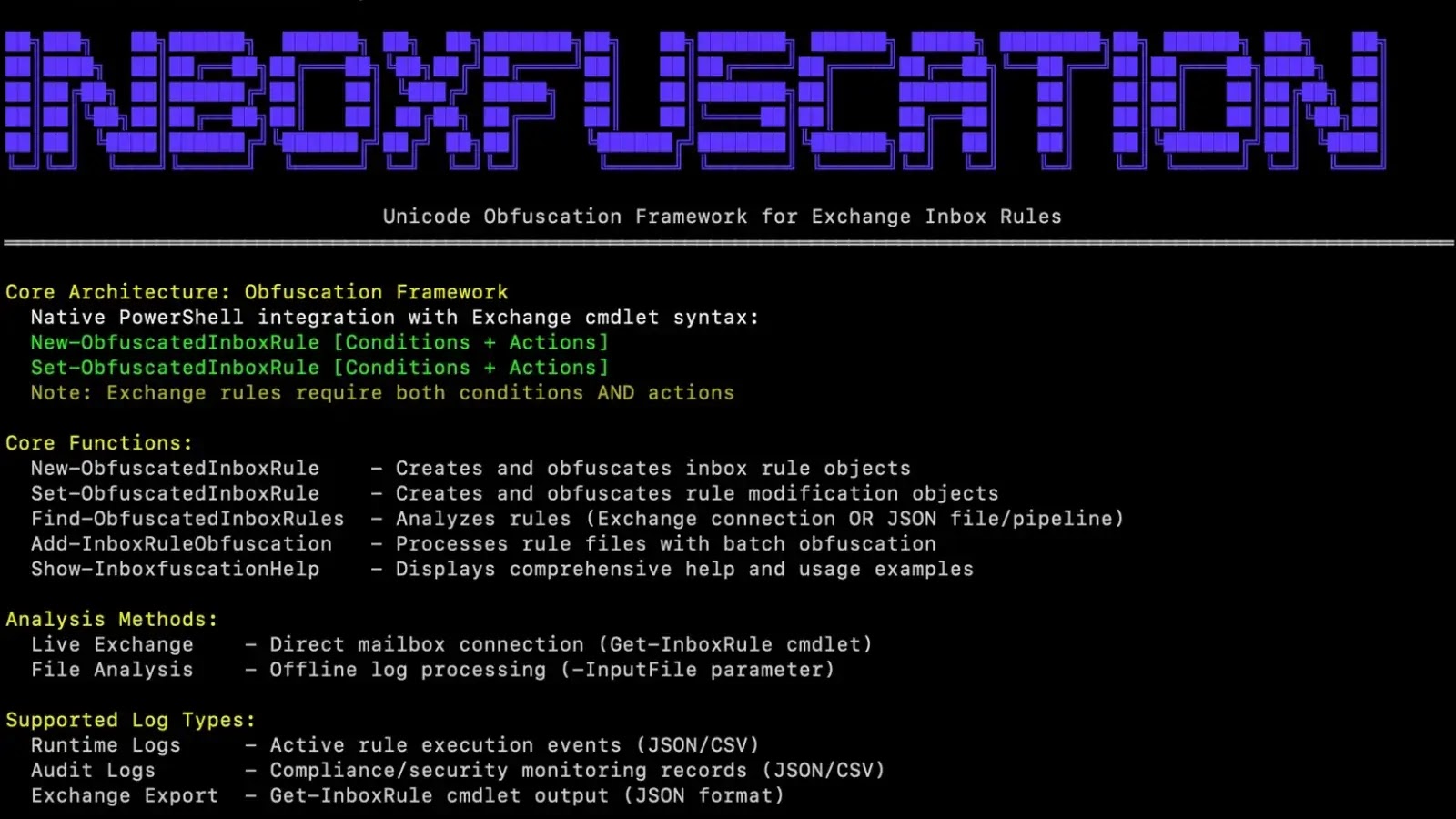
Inboxfuscation Tool Bypasses Exchange Inbox Rules and Evades Detection
Advanced persistent threat actors increasingly target Microsoft Exchange inbox rules to maintain persistence and siphon…
Canada Police Shuts Down TradeOgre After $56M Crypto Theft
Montréal, Quebec, September 18, 2025 – In an unprecedented operation, the Royal Canadian Mounted Police…