Android Under Siege as Hackers Harvest Credentials and Track Keystrokes
The Zscaler ThreatLabz team has uncovered significant advancements in the Anatsa malware, also known as…
AI Systems Capable of Generating Working Exploits for CVEs in Just 10–15 Minutes
Cybersecurity researchers have developed an artificial intelligence system capable of automatically generating working exploits for…
Microsoft to Restrict Use of OnMicrosoft Domains for Email Sending
Microsoft has announced significant restrictions on the use of default onmicrosoft.com domains for email communication,…
Colt Confirms Ransomware Attack Resulted in Customer Data Theft
Industrial technology company Colt has confirmed that a recent ransomware attack on its business support…
Azure Default API Connection Flaw Enables Full Cross-Tenant Compromise
A critical security vulnerability in Microsoft Azure’s API Connection architecture has been discovered that could…
Weaponized RAR Files Deliver VShell Backdoor on Linux Systems
Trellix Advanced Research Center has exposed an infection chain that weaponises nothing more than a…
UAC-0057 Leveraging Invitations to Trigger Shell Script Attacks
The Belarusian-affiliated threat actor UAC-0057, also known as UNC1151, FrostyNeighbor, or Ghostwriter, has been using…
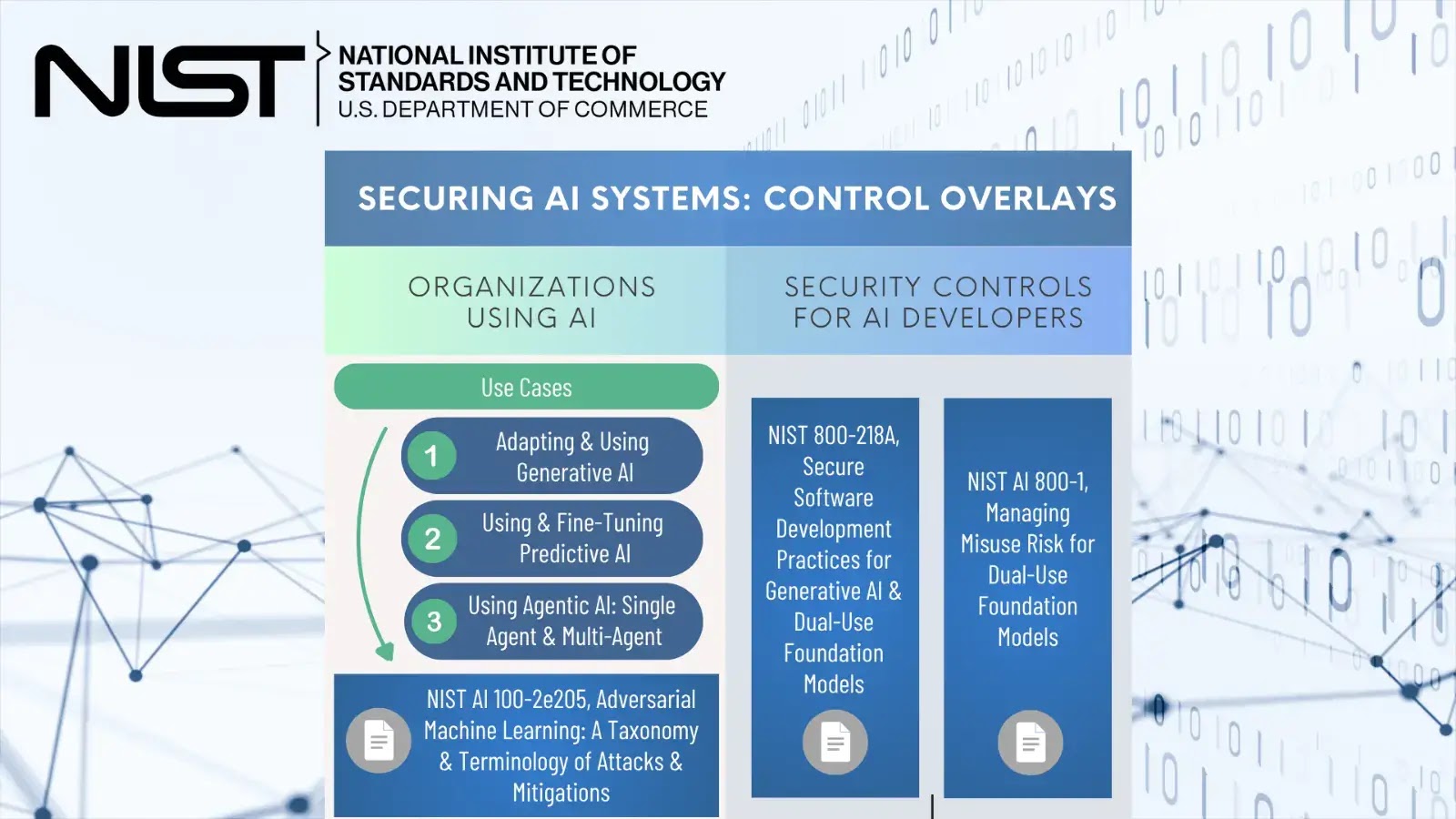
NIST Releases New Control Overlays to Manage Cybersecurity Risks in AI Systems
The National Institute of Standards and Technology (NIST) has unveiled a comprehensive initiative to address…
New HTTP Smuggling Technique Allows Hackers to Inject Malicious Requests
Cybersecurity researchers have uncovered a sophisticated HTTP request smuggling attack that exploits inconsistent parsing behaviors…
14 Million-Download SHA JavaScript Library Exposes Users to Hash Manipulation Attacks
A critical security vulnerability has been discovered in the widely-used sha.js npm package, exposing millions…