NIST Releases Lightweight Cryptography Standard for IoT Security
The National Institute of Standards and Technology (NIST) has formally published Special Publication 800-232, “Ascon-Based…
Hackers Exploit SendGrid to Steal User Login Credentials in Latest Attack
Cybersecurity researchers at the Cofense Phishing Defense Center (PDC) have uncovered a fresh surge in…
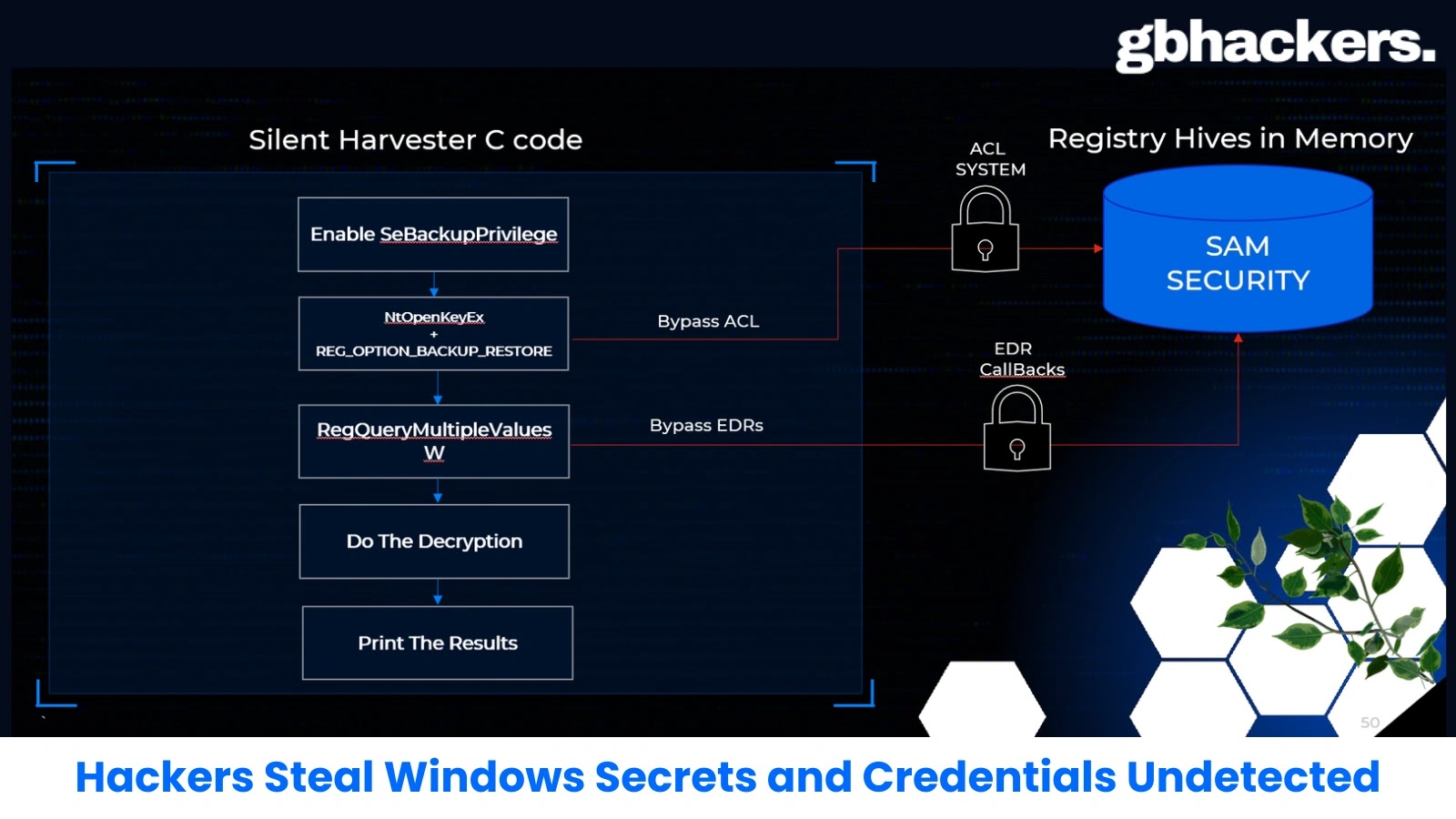
Hackers Steal Windows Secrets and Credentials Undetected by EDR Detection
A cybersecurity researcher has unveiled a sophisticated new method for extracting Windows credentials and secrets…
Happy Birthday Linux! 34 Years of Open-Source Power
August 25, 2025, marks the 34th anniversary of Linux, a project that began as a…
PoC Exploit and Technical Analysis Published for Apple 0-Day RCE Vulnerability
A critical zero-click remote code execution vulnerability in Apple’s iOS has been disclosed with a…
Critical Tableau Server Flaws Allows Malicious File Uploads
Salesforce has addressed multiple critical security vulnerabilities in Tableau Server and Desktop that could enable…
10 Best EDR Companies (Endpoint Detection And Response) in 2025
In 2025, the endpoint remains the primary battleground for cyber attackers, making the implementation of…
10 Best Web Content Filtering Solutions 2025
In the modern digital landscape, web content filtering is a fundamental component of cybersecurity and…
Top 10 Best Incident Response Companies in 2025
Data breaches, encompassing everything from unauthorized access and data exfiltration to ransomware-induced data destruction, pose…
10 Best Endpoint Protection Solutions for MSP/MSSPs in 2025
Managed Service Providers (MSPs) and Managed Security Service Providers (MSSPs) are the guardians of cybersecurity…