Google Introduces Enhanced Developer Verification for Play Store App Distribution
Google has announced that all Android apps installed on approved devices will soon need to…
New Hook Android Banking Malware Emerges with Advanced Features and 107 Remote Commands
Zimperium’s zLabs research team has identified a sophisticated new variant of the Hook Android banking…
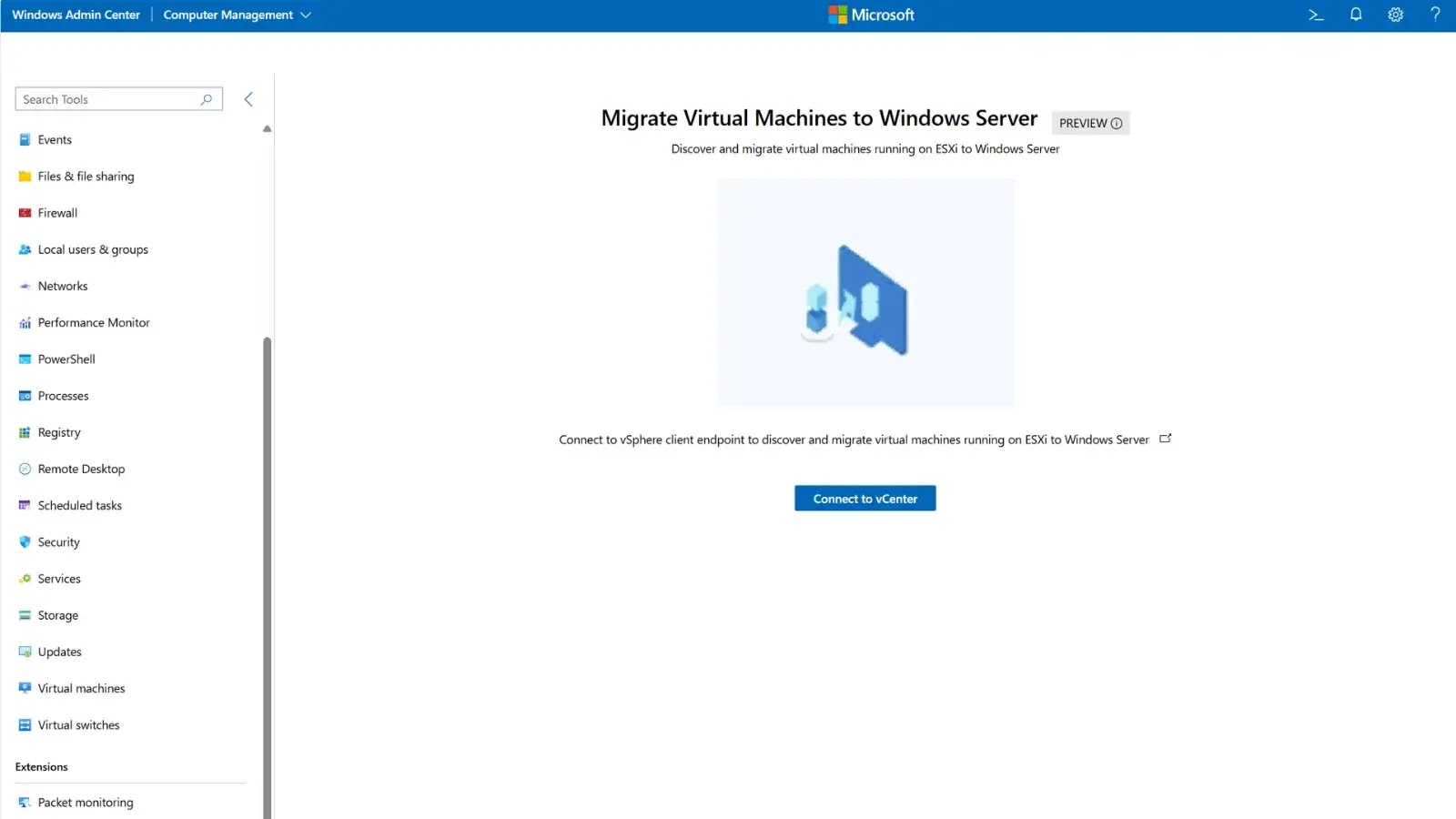
Microsoft Launches Tool to Migrate VMware VMs From vCenter to Hyper-V
Microsoft today announced the public preview of a new VM Conversion extension for Windows Admin Center, enabling…
Weaponized PuTTY Delivered via Malicious Bing Ads Targets Kerberos and Active Directory services
Cybersecurity incidents increasingly exploit human vulnerabilities, including those of privileged users, as demonstrated in recent…
Users of WhatsApp Desktop on Windows Face Code Execution Risk Via Python
A critical security risk has emerged for Windows users of WhatsApp Desktop who also have…
PhpSpreadsheet Library Vulnerability Lets Attackers Inject Malicious HTML Input
A critical Server-Side Request Forgery (SSRF) vulnerability has been discovered in the popular PhpSpreadsheet library, allowing attackers…
CISA Alerts on Git Arbitrary File Write Flaw Actively Exploited
The Cybersecurity and Infrastructure Security Agency (CISA) has issued an urgent alert regarding a critical…
Threat Actors Update Android Droppers to Remain Effective with Even Simple Malware
Threat actors are increasingly refining Android droppers to circumvent enhanced security measures, extending their utility…
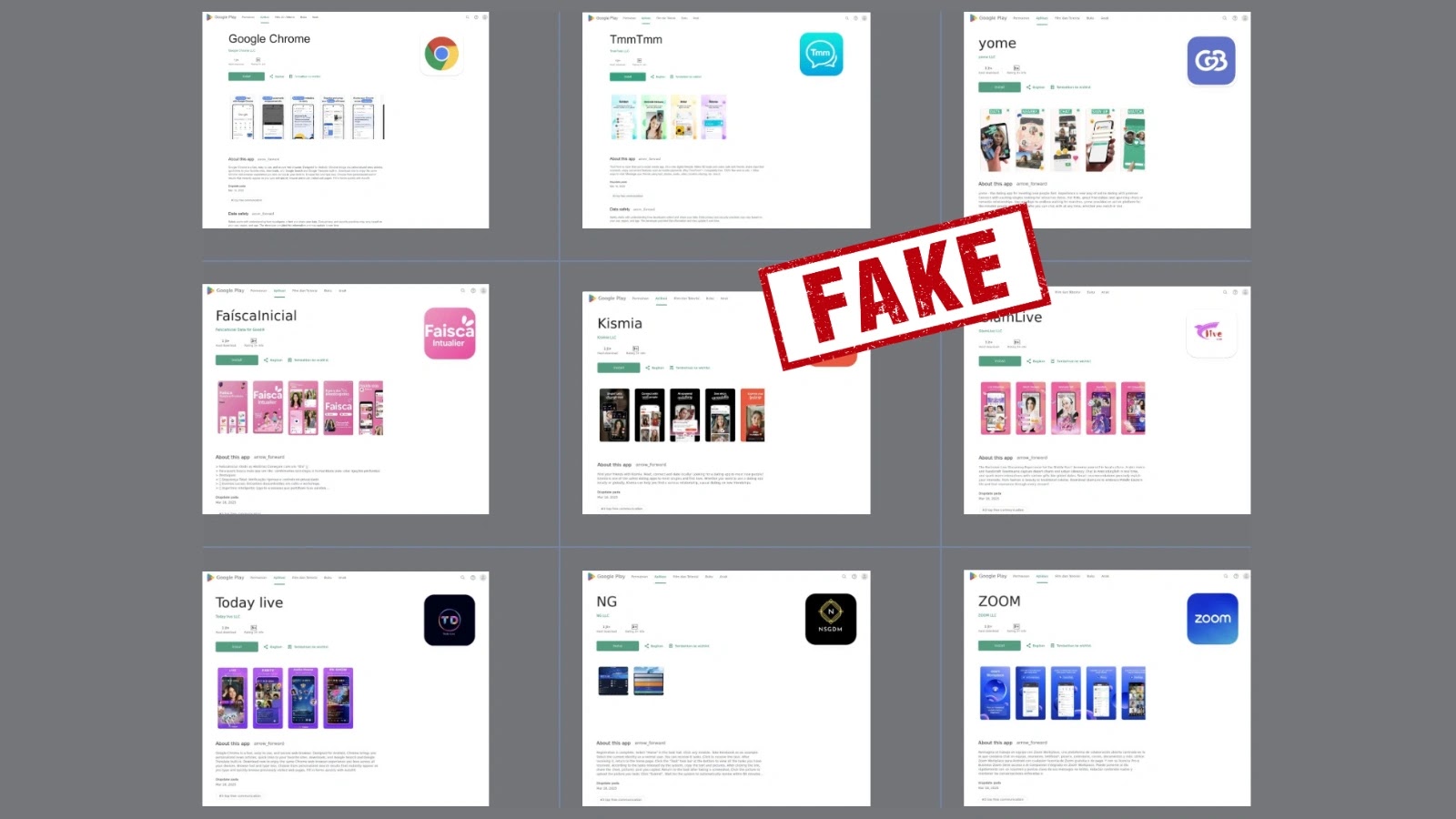
Beware! Fake Google Play Store Sites Used to Spread Android Malware
Cybersecurity researchers have identified a resurgence of SpyNote malware campaigns targeting Android users through sophisticated…
PoC Exploit Published for Chrome 0-Day Already Under Active Attack
A proof-of-concept exploit for a high-severity Google Chrome zero-day vulnerability has been published publicly, less…