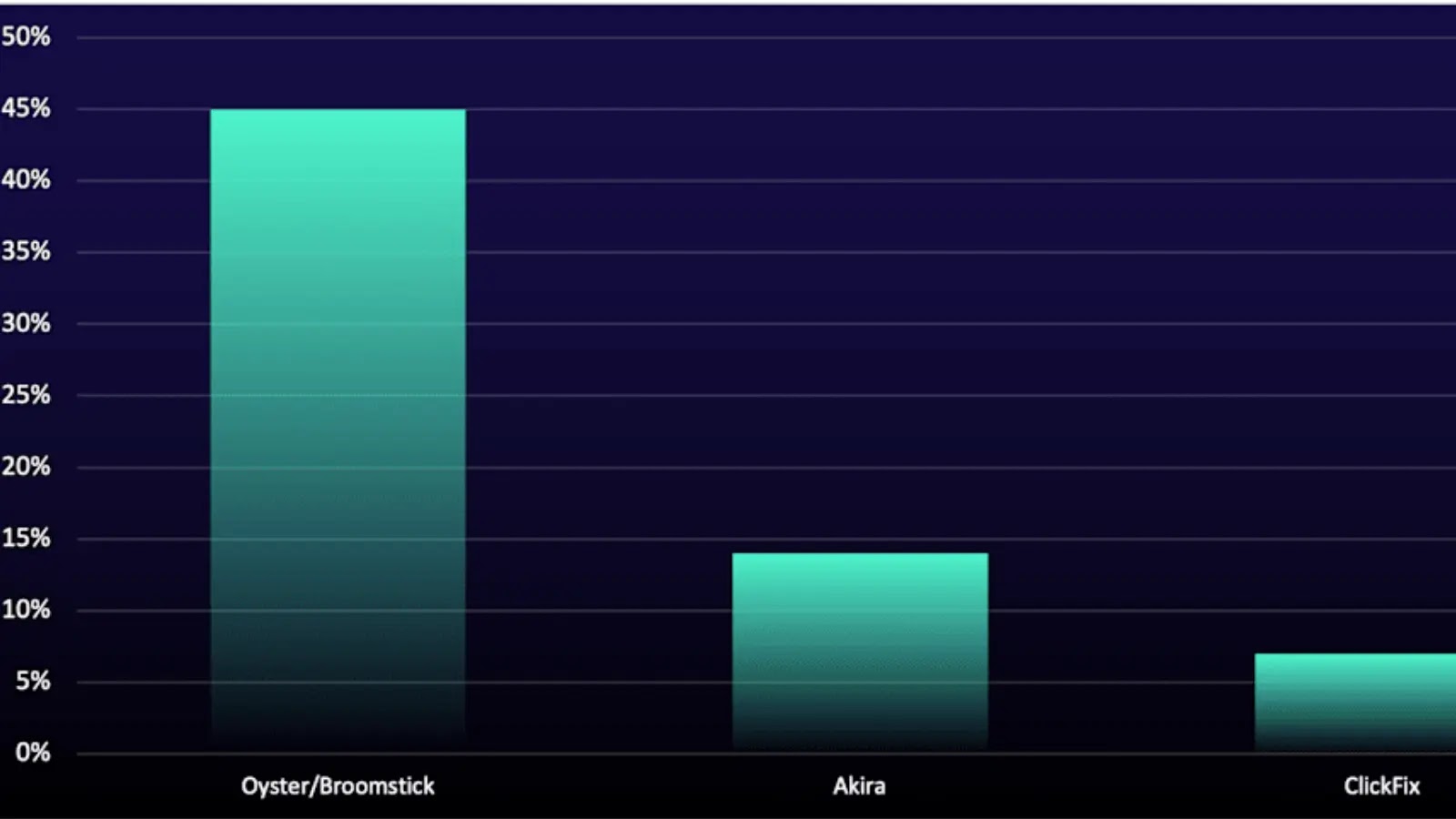
Threat Actors Breach Enterprise Infrastructure Within 18 Minutes of Initial Access
Attackers are accelerating their foothold in corporate networks: over the past three months (June 1…
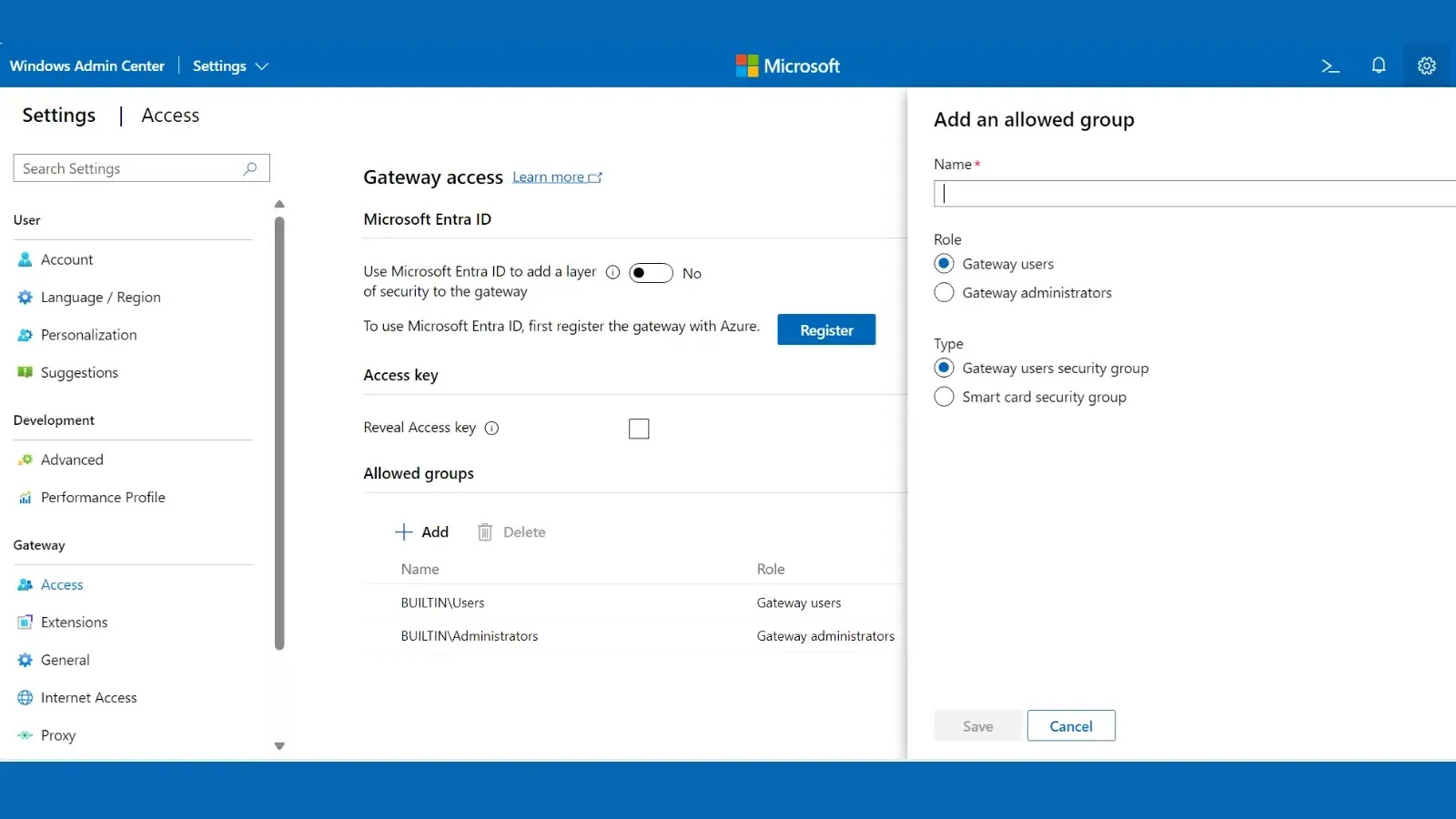
Microsoft Publishes Guide for Certificate-Based Authentication in Windows Admin Center
Microsoft has released comprehensive guidance for implementing certificate-based authentication in Windows Admin Center (WAC), providing…
Hackers Hijacking IIS Servers Using Malicious BadIIS Module to Serve Malicious Content
Leveraging a native IIS module named BadIIS, attackers manipulated search engine crawler traffic to poison…
2/3 of Organizations Fear Identity Attacks, But Blind Spots Remain
Austin, Texas, USA, September 23rd, 2025, CyberNewsWire New SpyCloud 2025 Identity Threat Report reveals dangerous…
Hackers Abuse IMDS Service for Cloud Initial Access
Cloud environments rely on the Instance Metadata Service (IMDS) to provide virtual machines with temporary…
SolarWinds Web Help Desk Vulnerability Enables Privilege Escalation
A critical vulnerability in SolarWinds Web Help Desk (WHD) could allow attackers to escalate privileges…
Beware of Fake Online Speedtest Apps with Hidden JavaScript Code
These fake online speedtest applications prey on users seeking to measure their internet performance, yet…
Zloader Malware Used as Gateway for Ransomware Deployment in Corporate Networks
Zloader, a sophisticated Zeus-based modular trojan that first emerged in 2015, has undergone a significant…
New npm Malware Steals Browser Passwords via Steganographic QR Code
A novel npm package named fezbox has been uncovered by the Socket Threat Research Team…
Lectora Desktop and Online XSS Vulnerability Enables JavaScript Injection
A critical cross-site scripting (XSS) vulnerability affecting both Lectora Desktop and Lectora Online has been…