CISA Reveals Hackers Breached U.S. Federal Agency via GeoServer RCE Flaw
Federal cybersecurity agency CISA has disclosed that attackers exploited a remote code execution vulnerability in…
Banking Trojans Targeting Android Users Disguise as Government and Trusted Payment Apps
Since August 2024, a financially motivated threat group has been targeting Android users in Indonesia…
Salesforce CLI Installer Flaw Lets Attackers Run Code and Gain SYSTEM-Level Access
A serious security flaw in the Salesforce CLI installer (sf-x64.exe) has been assigned CVE-2025-9844. This…
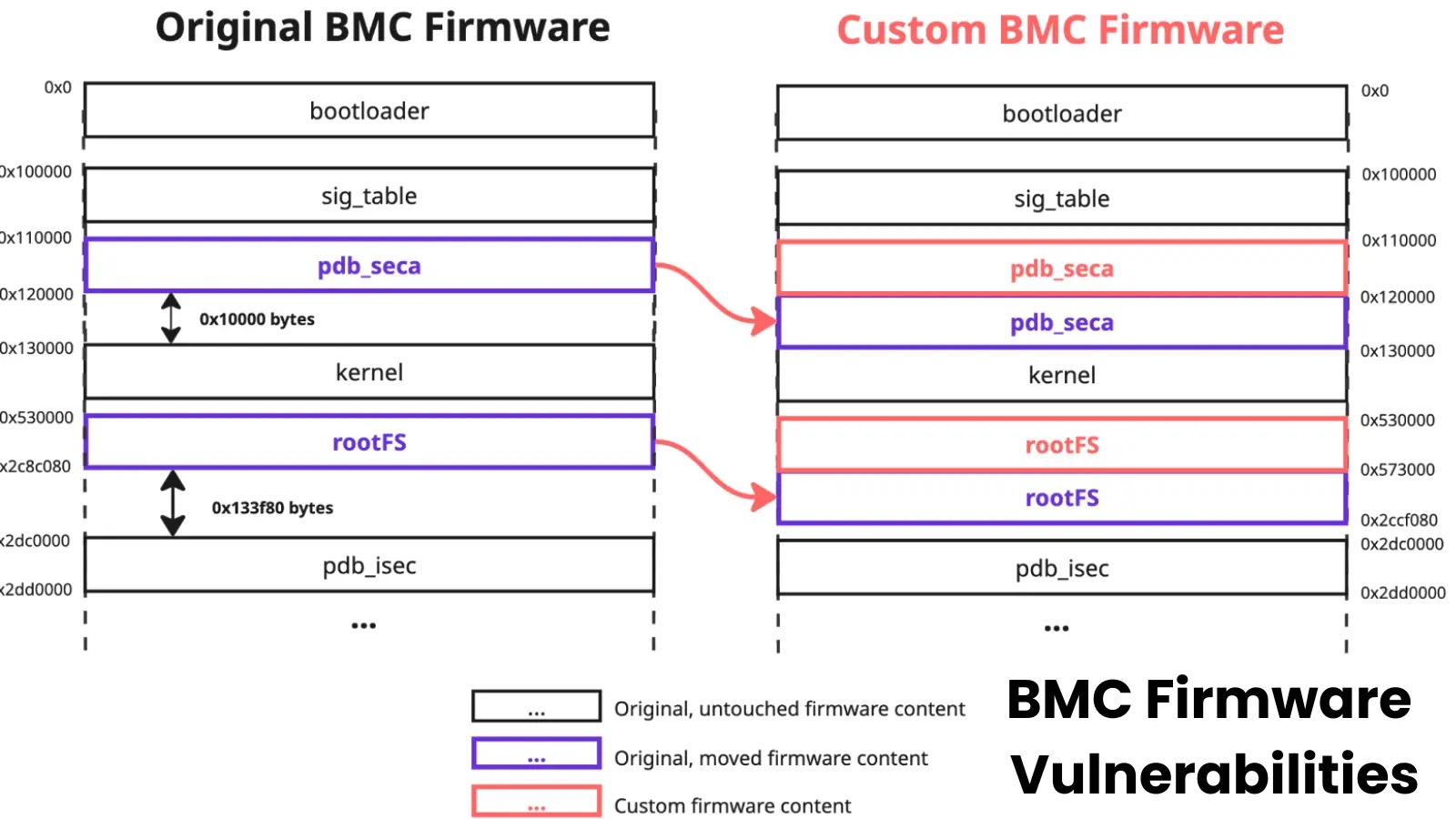
Attackers Exploit BMC Firmware Vulnerabilities to Bypass Signature Verification
In January 2025, Supermicro released patches addressing critical vulnerabilities in its Baseboard Management Controller (BMC)…
OnePlus OxygenOS Vulnerability Lets Apps Access SMS Data Without User Permission
A newly disclosed flaw in OnePlus OxygenOS lets any app on a device read SMS…
Chromium-Based Browsers in Windows Domains Vulnerable to Arbitrary Extension Loads
A new study has uncovered a method for silently installing custom extensions on Chromium-based browsers…
Russian Disinformation Campaign Targets Moldova’s Upcoming Elections
A sophisticated effort by Russian-linked actors is seeking to sway public opinion ahead of Moldova’s…
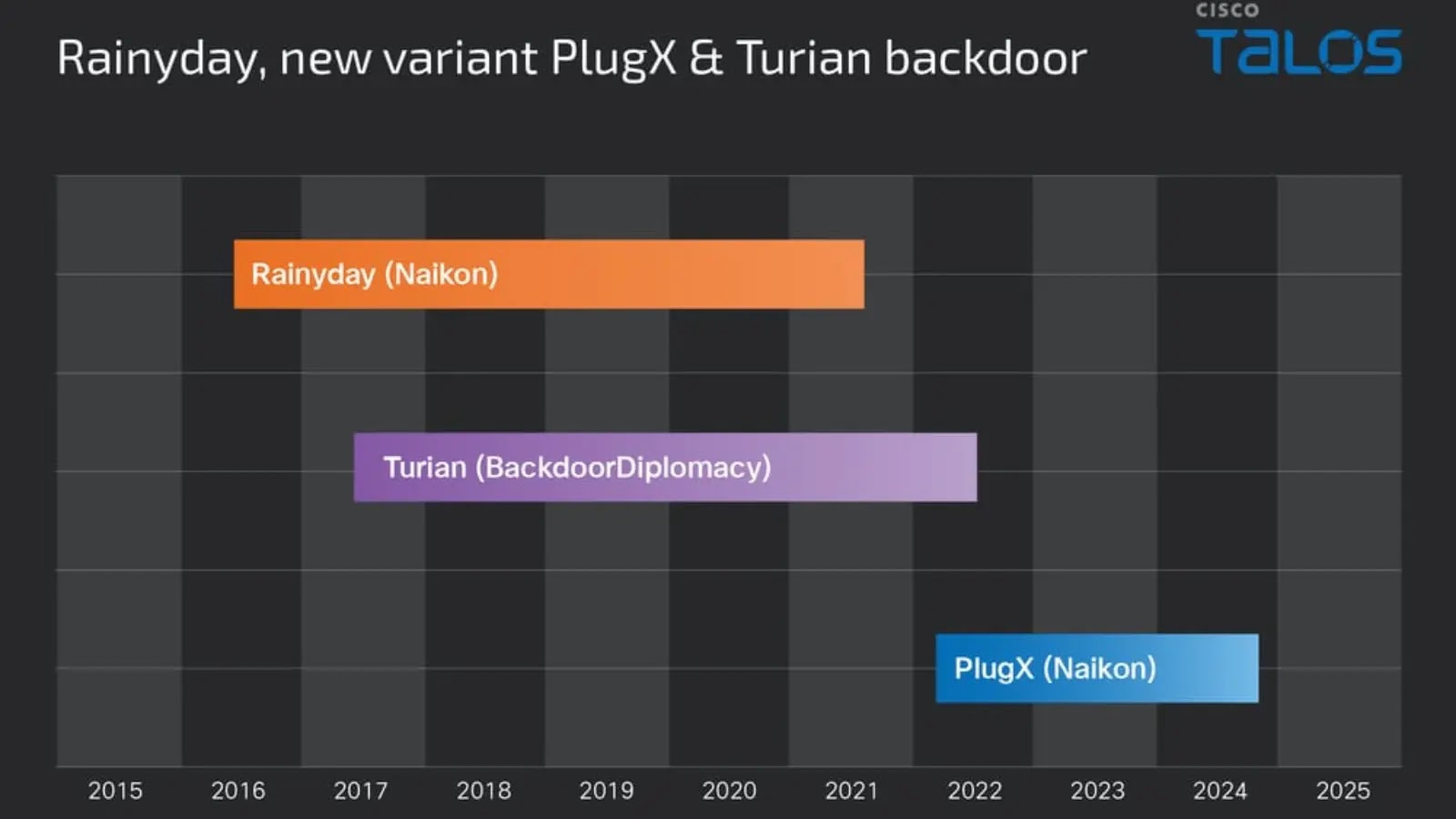
RainyDay, Turian and Naikon Malwares Abuse DLL Search Order to Execute Malicious Loaders
Cisco Talos has uncovered a sophisticated, long-running campaign active since 2022 that leverages DLL search…
Critical DNN Platform Vulnerability Let Attackers Execute Malicious Scripts
A severe Stored Cross-Site Scripting (XSS) vulnerability in the Prompt module of the DNN Platform…
North Korean IT Worker Gains Access to Organization’s Network Through Innocent Job Application
In today’s complex threat landscape, adversaries increasingly favor “malware-less” intrusion methods that slip past traditional…