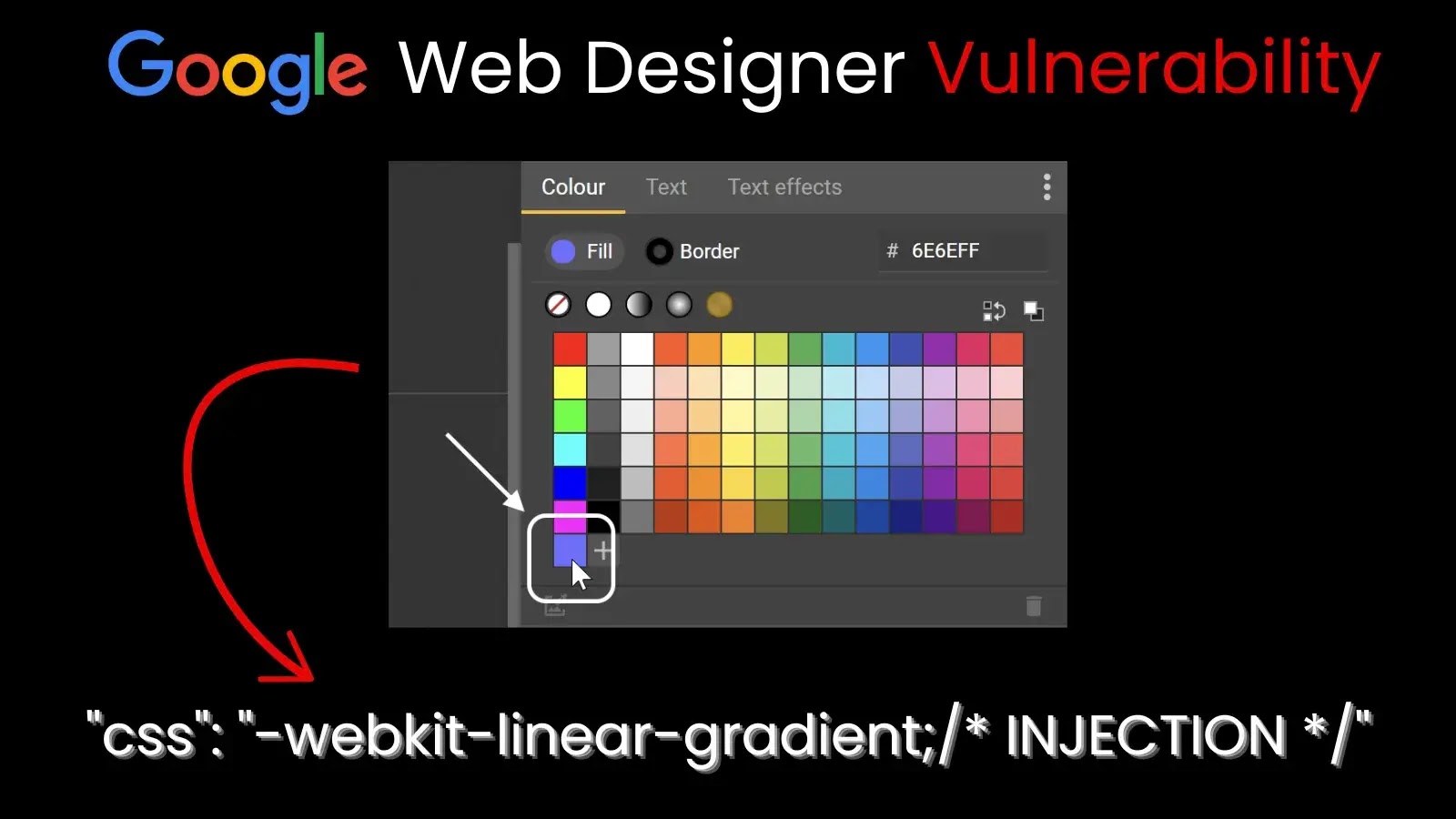
Google Web Designer Vulnerability Lets Hackers Take Over Client Systems
A critical client-side remote code execution (RCE) vulnerability in Google Web Designer exposed Windows users…
Plain Text Storage of Vulnerability Exploit Helm Values
A high-severity vulnerability in SUSE’s Fleet, a GitOps management tool for Kubernetes clusters, has been…
Apple May Drop Physical SIM Card in iPhone 17
Apple appears poised to remove the physical SIM card slot from its upcoming iPhone 17…
Microsoft Enforces MFA for Logging into Azure Portal
In a significant security move, Microsoft announced on August 26, 2025, that it will require…
Food Delivery Robots Vulnerable to Hacks That Redirect Orders
A startling vulnerability in Pudu Robotics’ management APIs that allowed anyone with minimal technical skill…
Critical Next.js Flaw Lets Attackers Bypass Authorization Controls
A newly disclosed critical vulnerability in the Next.js framework, tracked as CVE-2025-29927, allows unauthenticated attackers…
Hackers Exploit Email Marketing Platforms to Deliver Hidden Malware
In recent months, Trustwave SpiderLabs—a LevelBlue company renowned for its threat intelligence and incident response…
Phishing Campaign Exploits Ads to Breach Hotel Property Management Systems
A sophisticated malvertising campaign has emerged that specifically targets hoteliers and vacation rental operators by…
Hackers Register Domains to Target 2026 FIFA World Cup in Cyberattack
A concerning surge in malicious domain registrations designed to exploit the upcoming 2026 FIFA World…
MediaTek Issues Security Update to Patch Multiple Chipset Flaws
MediaTek today published its September 2025 Product Security Bulletin, disclosing and remediating a series of…