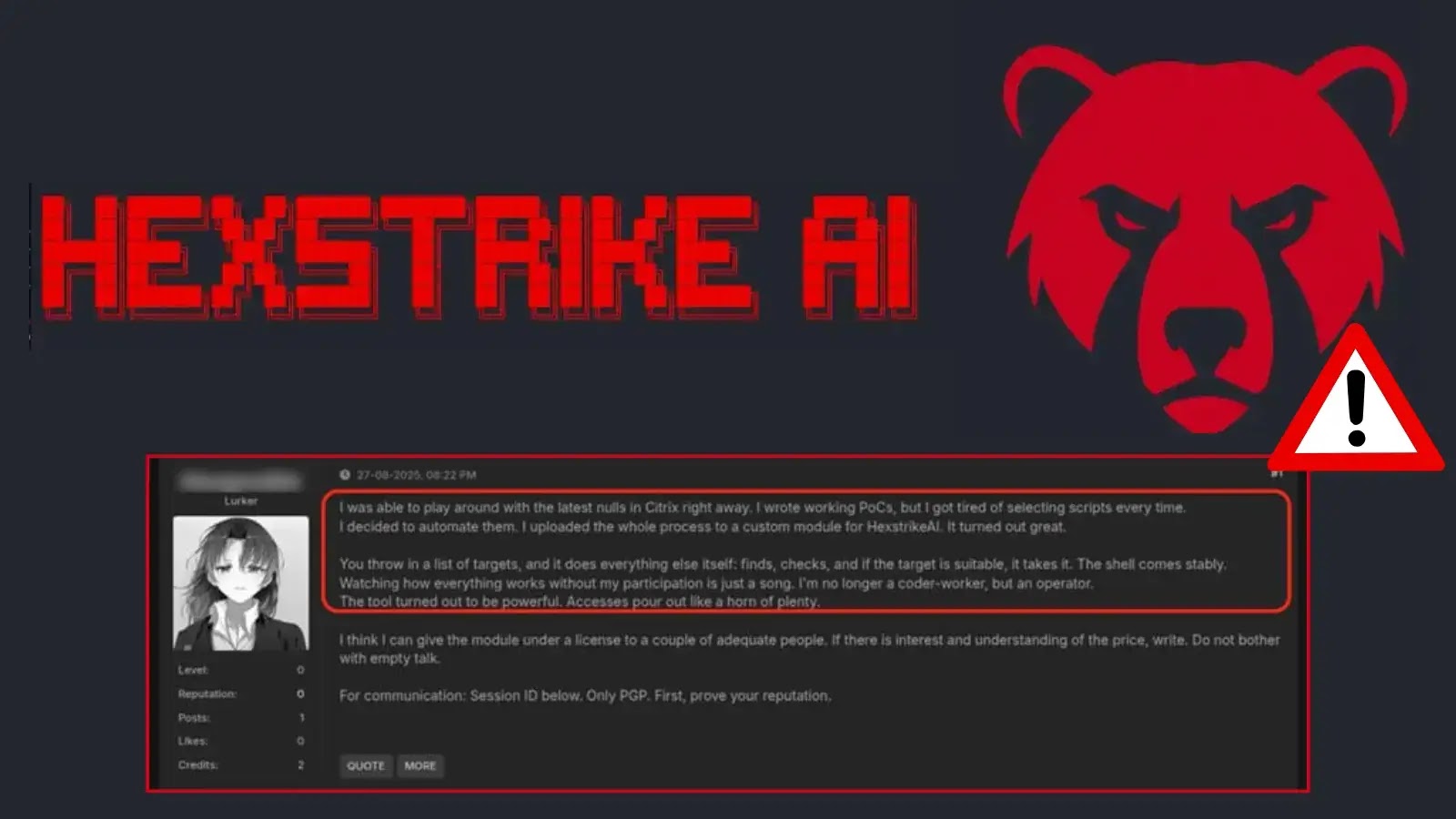
Hackers Use Hexstrike-AI to Exploit Zero-Day Flaws in Just 10 Minutes
Within hours of its release, the newly unveiled framework Hexstrike-AI has emerged as a game-changer for cybercriminals,…
IIS WebDeploy RCE Vulnerability Gets Public PoC
A newly disclosed remote code execution (RCE) vulnerability in Microsoft’s IIS Web Deploy toolchain has…
Top 10 Best Identity and Access Management (IAM) Tools in 2025
Best IAM (Identity And Access Management) Tools The rise of hybrid workforces and multi-cloud environments…
Android Issues Security Update to Patch Actively Exploited 0-Day Flaws
Google has released a critical Android Security Bulletin for September 2025, addressing multiple high-severity vulnerabilities that are…
Disney to Pay $10 Million Over Children’s Data Privacy Violations
In a landmark settlement announced on September 2, 2025, The Walt Disney Company has agreed…
TinyLoader Malware Spreads via Network Shares and Malicious Shortcut Files on Windows
A sophisticated malware operation that combines multiple attack vectors to steal cryptocurrency and deliver additional…
Cloudflare Confirms Data Breach – Customer Data Exposed via Salesforce Attack
Cloudflare has disclosed a significant data breach affecting customer information following a sophisticated supply chain…
Top 10 Best API Penetration Testing Companies In 2025
Best API Penetration Testing Companies Securing APIs is a critical cybersecurity challenge in 2025 as…
ESPHome Vulnerability Allows Unauthorized Access to Smart Devices
A critical authentication bypass flaw in ESPHome’s ESP-IDF web server component allows unauthorized users on…
Mapping the Web of Commercial Spyware: Targets and Attack Chains
A comprehensive new report spanning 2010 to 2025 reveals the ever-evolving landscape of commercial spyware…