Colombian Malware Exploits SWF and SVG to Evade Detection
A sophisticated malware campaign targeting Colombian institutions through an unexpected vector: weaponized SWF and SVG…
Windows Heap Buffer Overflow Vulnerability Allows Attackers to Gain Elevated Privileges
A critical security vulnerability has been discovered in Microsoft Windows systems that allows attackers to…
NightshadeC2 Botnet Exploits ‘UAC Prompt Bombing’ to Evade Windows Defender
A sophisticated new botnet called NightshadeC2 that employs an innovative “UAC Prompt Bombing” technique to…
Hackers Exploit Raw Disk Reads to Evade EDR and Steal Sensitive Files
Attackers can bypass Endpoint Detection and Response (EDR) tools and file locks by reading raw…
Chess.com Confirms Data Breach After Hackers Exploit External System
Chess.com, the world’s leading online chess platform, has confirmed a significant data breach that compromised…
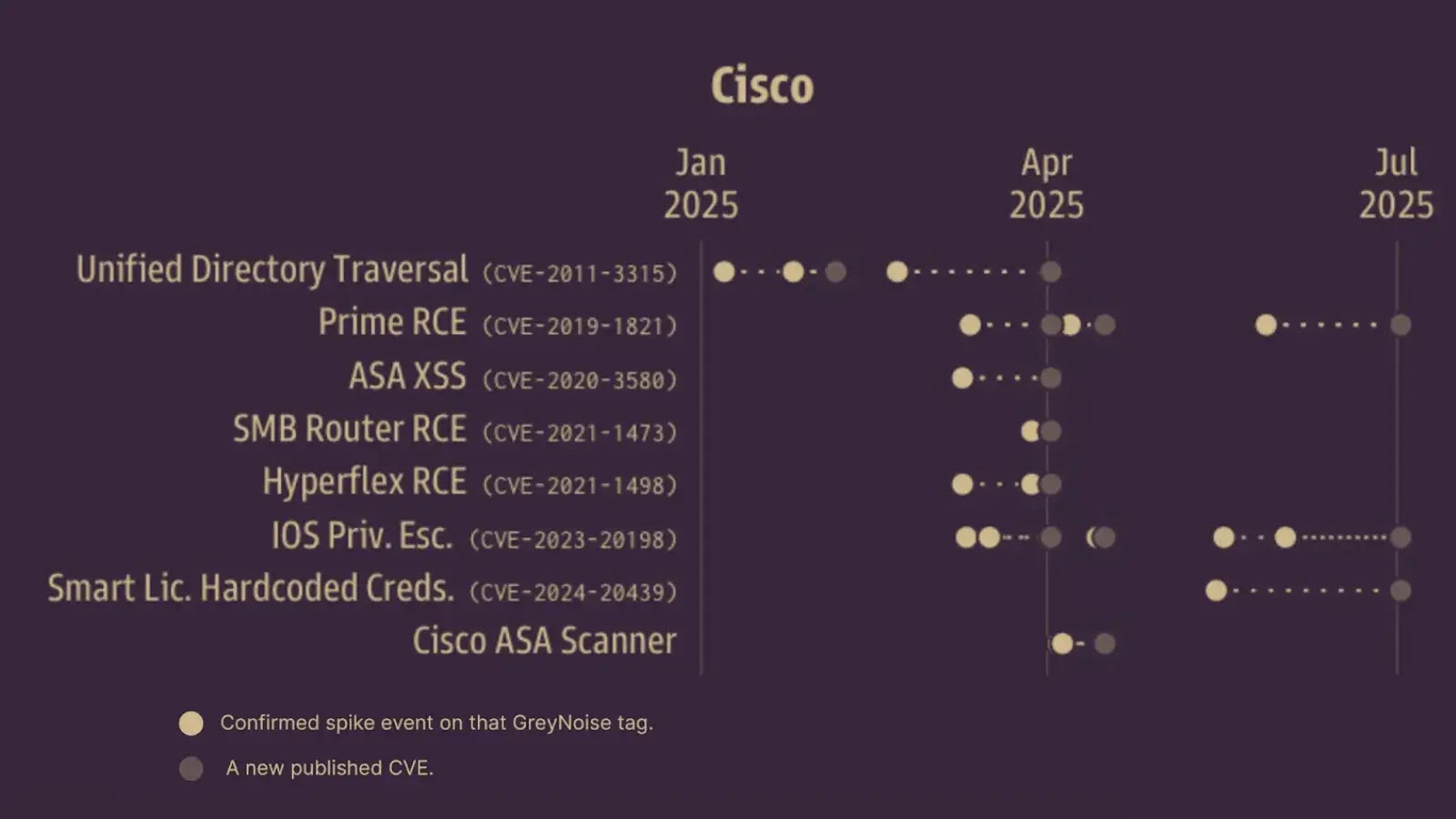
Hackers Target Cisco ASA Devices in Massive Scan Across 25,000 IPs
Security researchers have detected massive scanning campaigns targeting Cisco Adaptive Security Appliance (ASA) devices, with…
Iran-Nexus Hackers Impersonate Omani MFA to Target Governments Entities
Cybersecurity researchers uncovered a sophisticated, Iran-linked spear-phishing operation that exploited a compromised Ministry of Foreign…
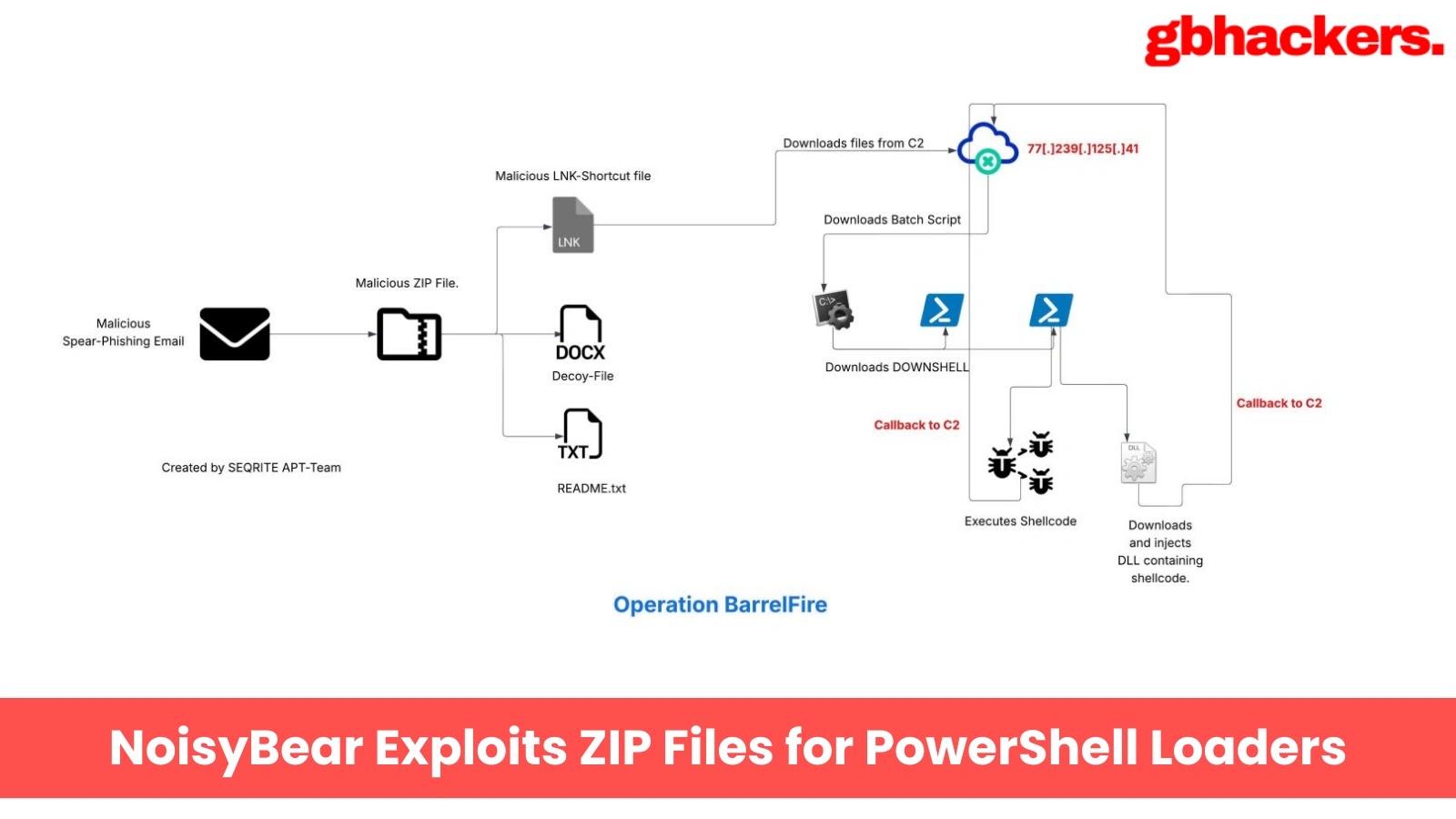
NoisyBear Exploits ZIP Files for PowerShell Loaders and Data Exfiltration
The threat actor known as NoisyBear has launched a sophisticated cyber-espionage effort called Operation BarrelFire,…
Bridgestone Confirms Cyberattack Impacts Manufacturing Facilities Across North America
Tire manufacturer launches a comprehensive investigation after a limited cyber incident affects operations at multiple…
Microsoft Confirms UAC Bug Disrupts App Installation on Windows 10 & 11
Microsoft has officially acknowledged a significant User Account Control (UAC) bug that is causing widespread…