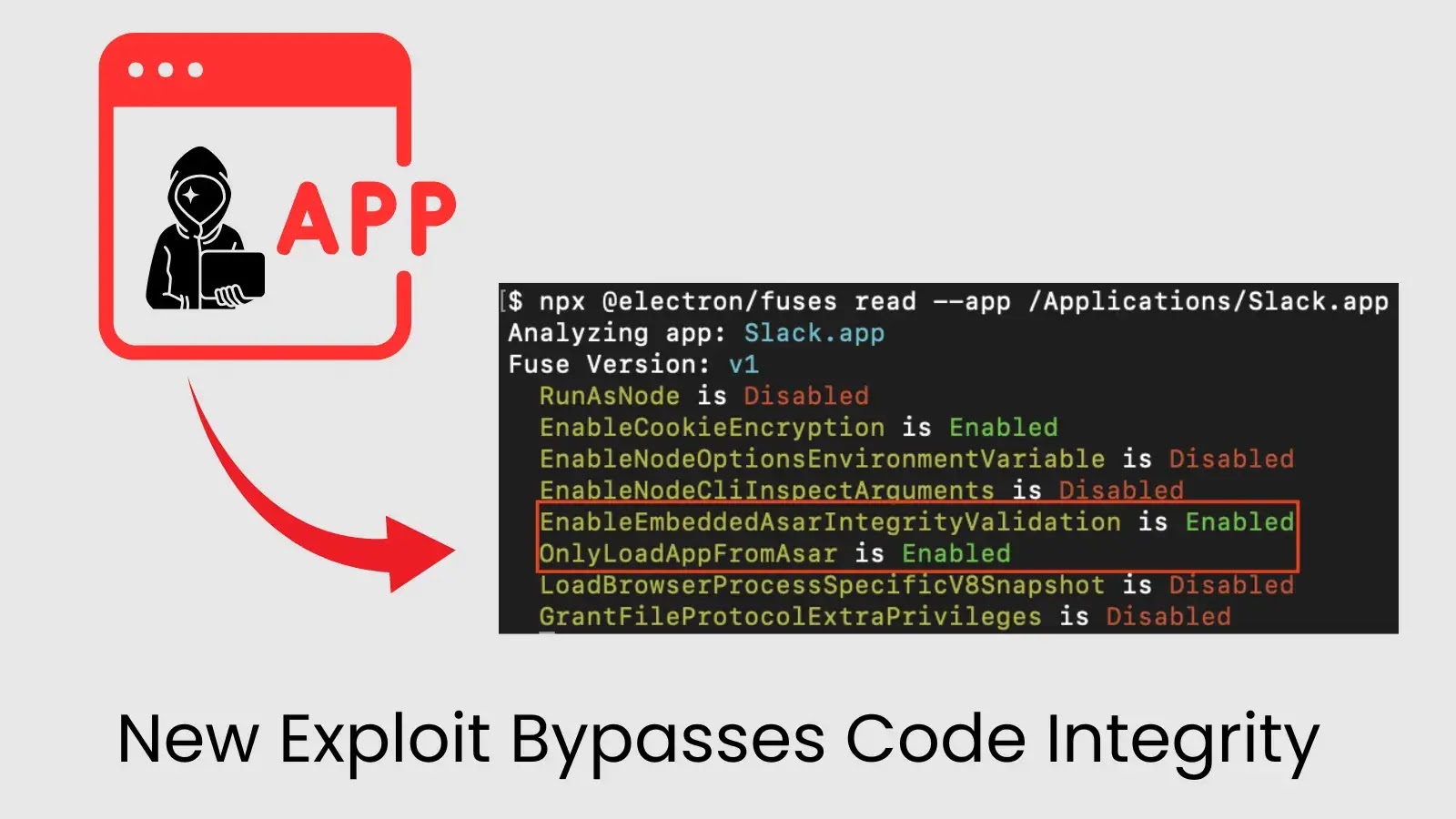
New Exploit Bypasses Code Integrity to Backdoor Signal, 1Password, Slack, and More
A new security exploit has been discovered that lets attackers slip malicious code into widely…
TP-Link Vulnerabilities Under Active Exploitation
The Cybersecurity and Infrastructure Security Agency (CISA) has issued an urgent warning regarding critical vulnerabilities…
TAG-150 Hackers Escalate Attacks with Proprietary Malware Families
A sophisticated threat actor, TAG-150, active since at least March 2025. Characterized by rapid malware…
SafePay Ransomware Hits 73 Organizations in Just One Month
SafePay, an emerging ransomware group, has rapidly ascended from obscurity to notoriety in 2025. In…
Critical SAP S/4HANA Vulnerability Actively Exploited, Allowing Full System Takeover
A critical security flaw in SAP S/4HANA, tracked as CVE-2025-42957, is being actively exploited by…
10 Best Attack Surface Management (ASM) Companies in 2025
Attack Surface Management (ASM) is a proactive cybersecurity discipline that helps organizations identify, analyze, and…
Threat Actors Exploit ScreenConnect Installers for Initial Access
A marked escalation in the abuse of ConnectWise ScreenConnect installers since March 2025, with U.S.-based…
North Korean Hackers Expose Their Playbook for Swapping Infrastructure
A sophisticated North Korean cyber operation has been exposed, revealing how state-sponsored hackers systematically monitor…
New Malware Exploits Windows Character Map to Evade Defender and Mine Crypto
A sophisticated cryptojacking campaign that hijacks Windows’ native Character Map utility (“charmap.exe”) to evade Windows…
Hackers Exploit Google Calendar API with Serverless MeetC2 Framework
A novel serverless command-and-control (C2) technique that abuses Google Calendar APIs to obscure malicious traffic…