Link11 Reports 225% more DDoS attacks in H1 2025 with new tactics against infrastructure
Frankfurt am Main, Germany, September 9th, 2025, CyberNewsWire The threat landscape surrounding distributed denial-of-service (DDoS)…
Zoom Security Update Fixes Vulnerabilities in Windows Client and Workplace Platform
Zoom has released an urgent security update for its Windows client and Workplace platform to…
Ivanti Endpoint Manager Vulnerabilities Allow Remote Code Execution by Attackers
Ivanti released Security Advisory for Endpoint Manager versions 2024 SU3 and 2022 SU8, detailing two…
Multiple Vulnerabilities Discovered in Ivanti Connect Secure, Policy Secure, and ZTA Gateways
Ivanti on September 9 released a security advisory detailing six medium and five high severity vulnerabilities impacting Ivanti Connect…
FortiDDoS Vulnerability Lets Hackers Execute Unauthorized OS Commands
Fortinet has disclosed a significant OS command injection vulnerability in its FortiDDoS-F appliances that could…
RatOn Hijacks Bank Account to Launch Automated Money Transfers
Dubbed RatOn, that combines traditional overlay attacks with NFC relay tactics to hijack bank accounts…
Data from Police Body Camera Apps Routed to Chinese Cloud Servers Over TLS Port 9091
The security and integrity of police body camera footage underpin the validity of evidence presented…
Aembit Named to Fast Company’s Seventh-Annual List of the 100 Best Workplaces for Innovators
Silver Spring, USA, September 9th, 2025, CyberNewsWire Fast Company today announced its seventh-annual Best Workplaces for Innovators list,…
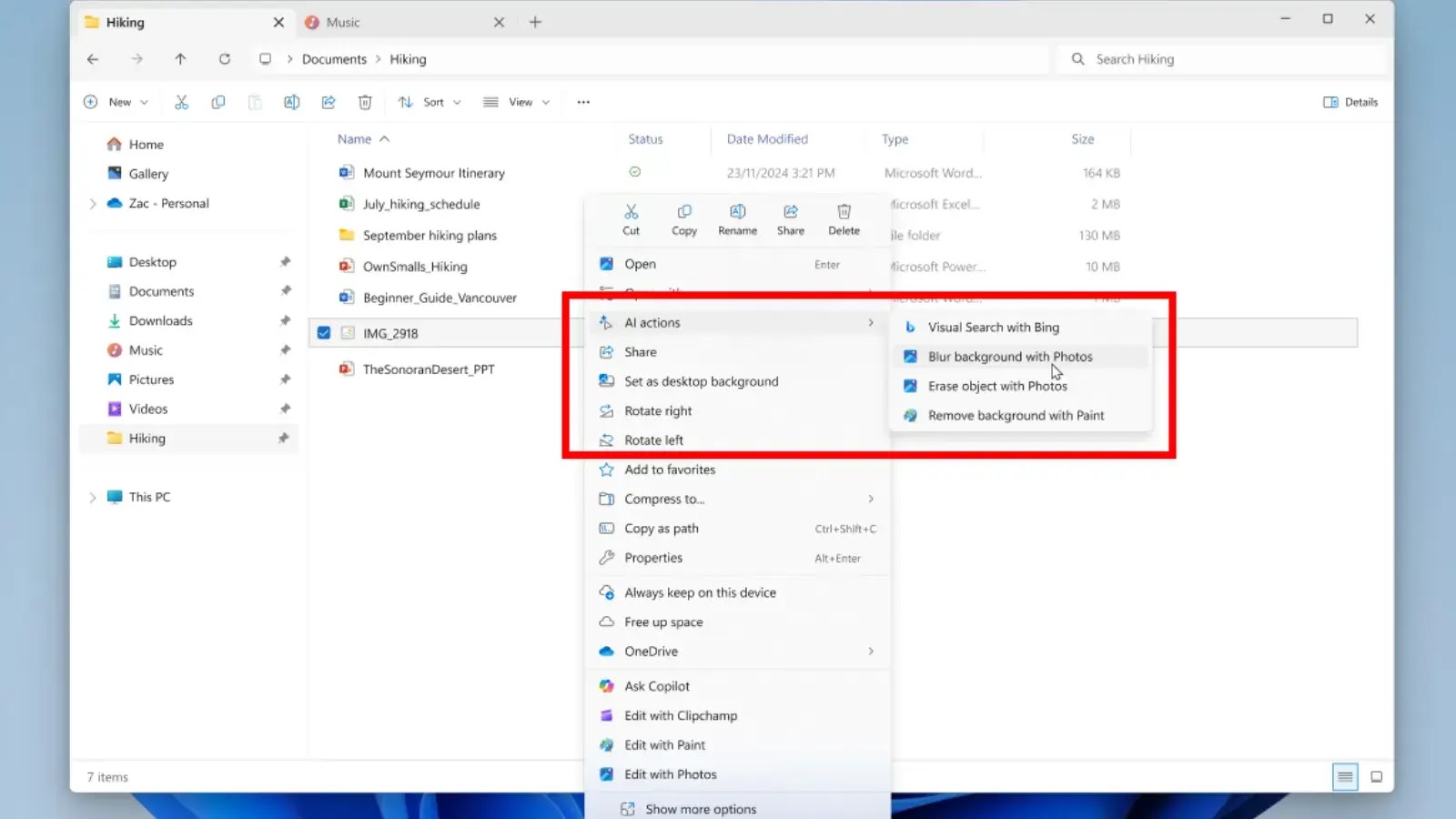
Microsoft to Add New AI-Powered Actions in File Explorer
Microsoft is rolling out AI-powered actions in File Explorer, allowing users to interact with files more…
Kimusky Hackers Masquerade as Tax Authority with ‘September Tax Return Due Date’ Email
South Korean internet users are being targeted by a sophisticated phishing campaign attributed to the…