Yurei Ransomware Uses PowerShell to Deploy ChaCha20 File Encryption
A newly discovered ransomware group called Yurei has emerged with sophisticated encryption capabilities, targeting organizations…
Over 500GB of Sensitive Great Firewall of China Data Leaked Online
A massive data breach has exposed the inner workings of China’s internet censorship system, with…
Mustang Panda Uses SnakeDisk USB Worm and Toneshell Backdoor to Target Air-Gap Systems
IBM X-Force researchers have uncovered sophisticated new malware campaigns orchestrated by the China-aligned threat actor…
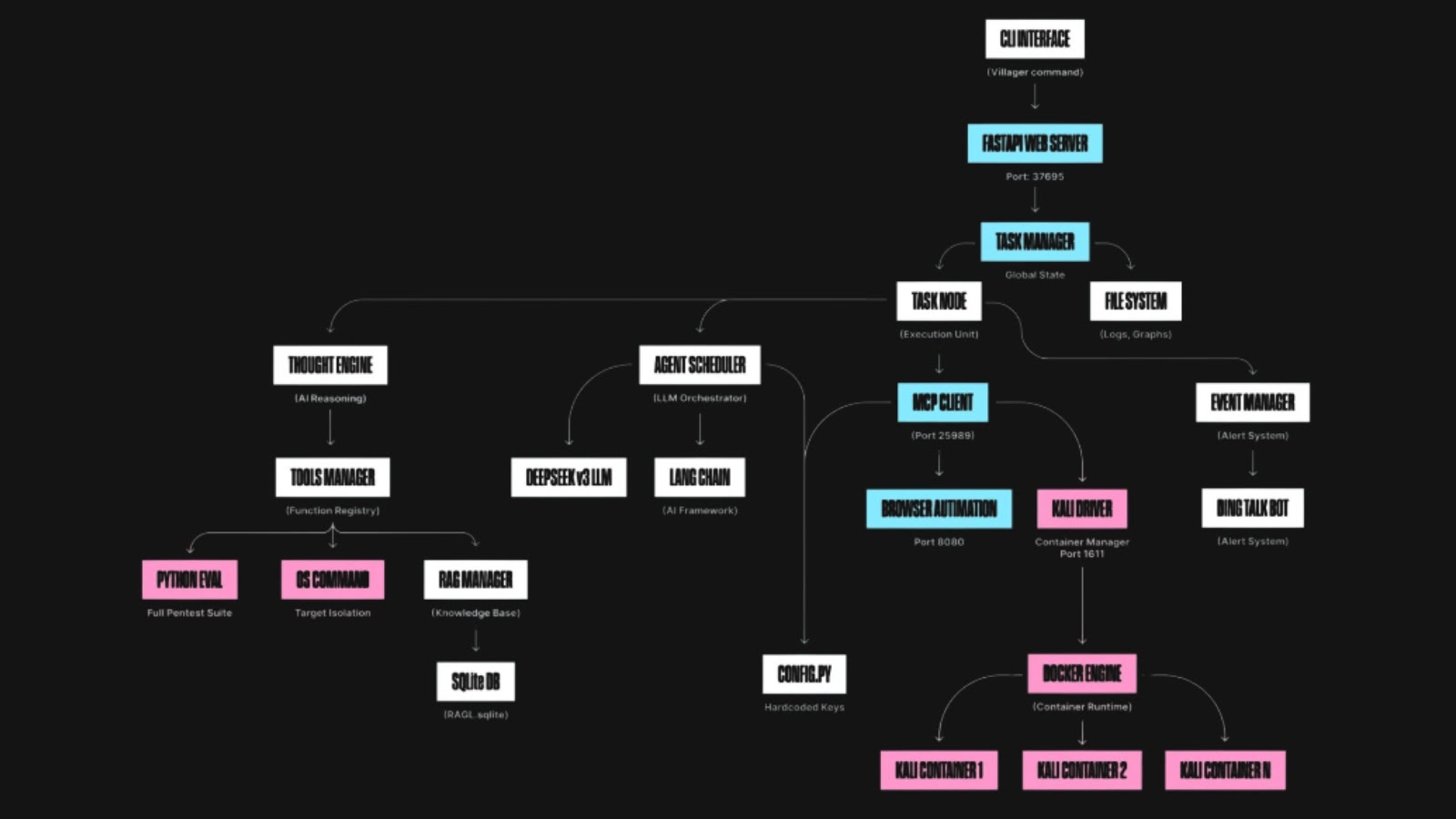
AI Pentesting Tool ‘Villager’ Merges Kali Linux with DeepSeek AI for Automated Security Attacks
Security researchers at Straiker’s AI Research (STAR) team have uncovered Villager, an AI-native penetration testing…
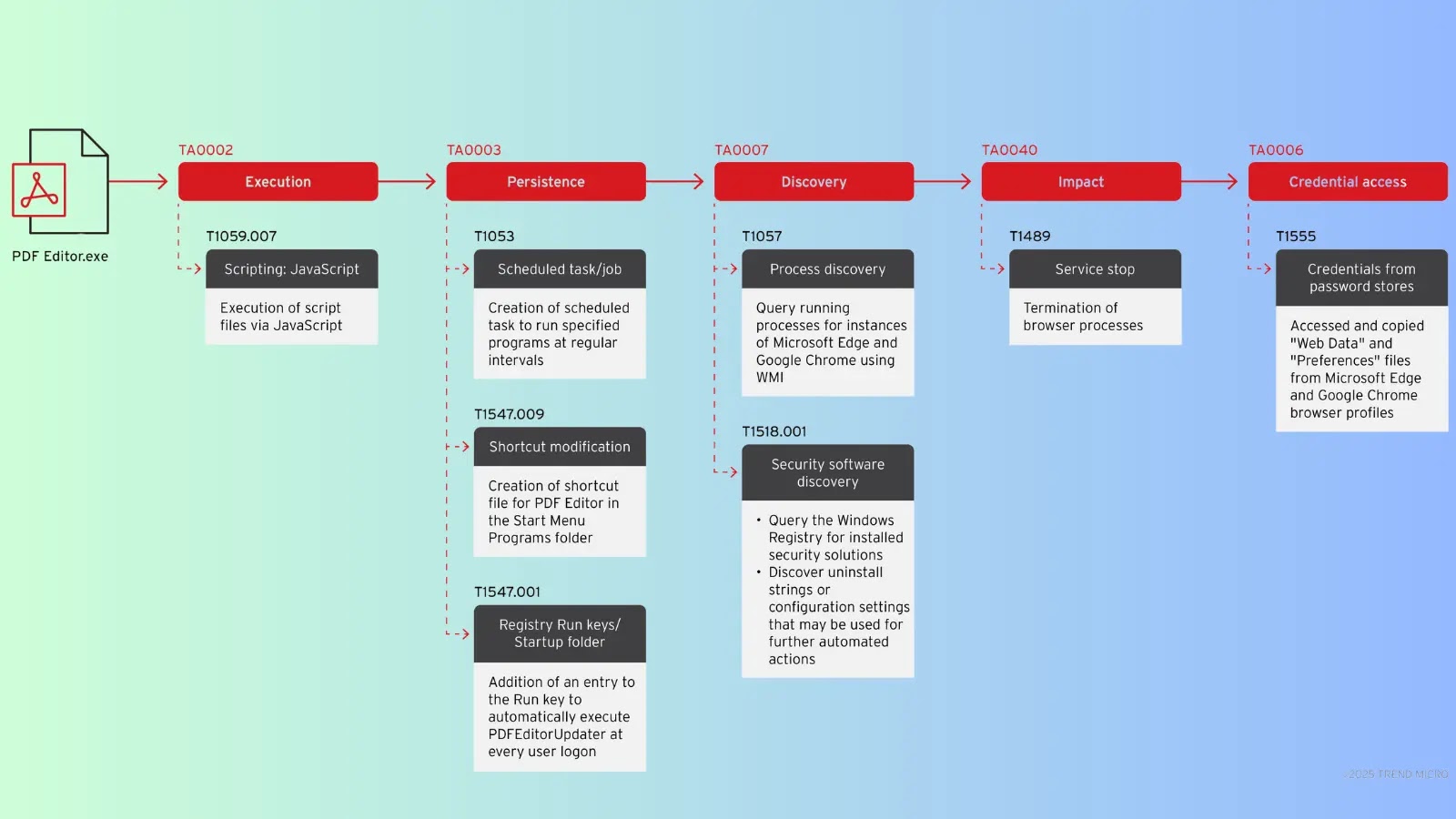
Leveraging AI to Steal Browser Data and Evade Detection
EvilAI, a new malware family tracked by Trend™ Research, has emerged in recent weeks disguised…
Microsoft Windows Defender Firewall Vulnerabilities Allow Privilege Escalation
Microsoft has released security advisories for four newly discovered vulnerabilities in its Windows Defender Firewall…
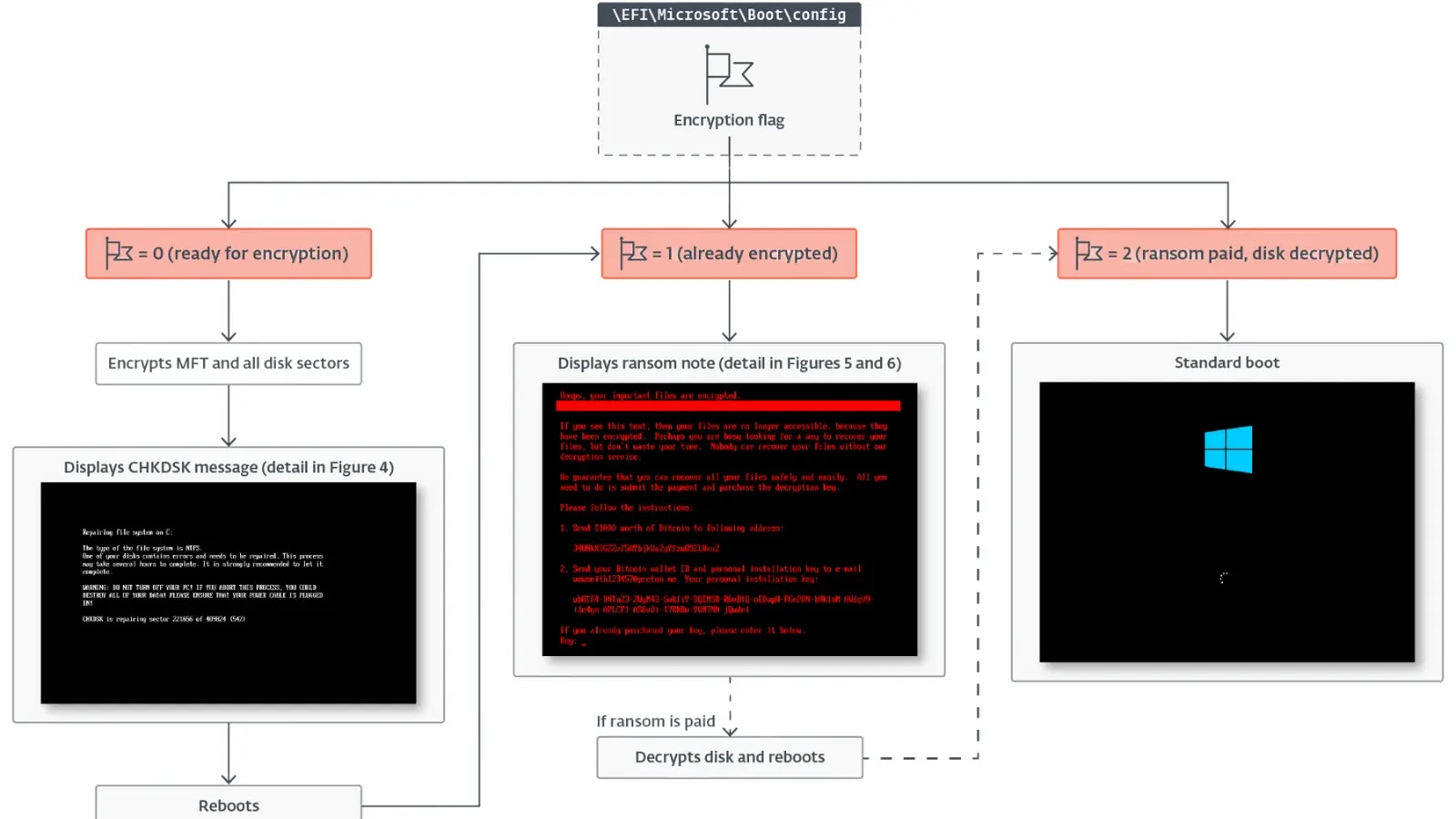
HybridPetya Exploits UEFI Vulnerability to Bypass Secure Boot on Legacy Systems
ESET Research has uncovered a sophisticated new ransomware variant called HybridPetya, discovered on the VirusTotal…
Buterat Backdoor Campaigns Targeting Enterprise Endpoint Control
Backdoor malware is a covert type of malicious software designed to bypass standard authentication mechanisms…
New Malvertising Campaign Exploits GitHub Repositories to Distribute Malware
A sophisticated malvertising campaign has been uncovered targeting unsuspecting users through “dangling commits” in a…
New Malware Abuses Azure Functions to Host Command and Control Infrastructure
A malicious ISO image named Servicenow-BNM-Verify.iso was uploaded to VirusTotal from Malaysia with almost no…