LangChainGo Vulnerability Allows Malicious Prompt Injection to Access Sensitive Data
A recently discovered flaw in LangChainGo, the Go implementation of the LangChain framework for large…
BlackNevas Ransomware Encrypts Files, Exfiltrates Corporate Data
Countries with most cyberattacks stopped highlighting global cyber defense efforts, including key regions in Asia-Pacific…
DarkCloud Stealer Targets Financial Firms via Weaponized RAR Files
August 2025 saw a dramatic surge in targeted attacks by the DarkCloud Stealer against financial…
Microsoft Warns Windows 11 23H2 Support Ending in 60 Days
Microsoft has issued an urgent reminder to enterprise and educational institutions worldwide about the impending…
AppSuite-PDF, PDF Editor Operators Exploited 26 Code-Signing Certificates to Fake Legitimacy
Analysis reveals that the developers behind the AppSuite-PDF and PDF Editor campaigns have abused at…
Top 10 Best Ransomware Protection Companies in 2025
As per a recent Sophos report from July 2025, 53% of Indian organizations impacted by…
Linux CUPS Flaw Allows Remote Denial of Service and Authentication Bypass
Two critical security vulnerabilities have been discovered in the Common Unix Printing System (CUPS), a…
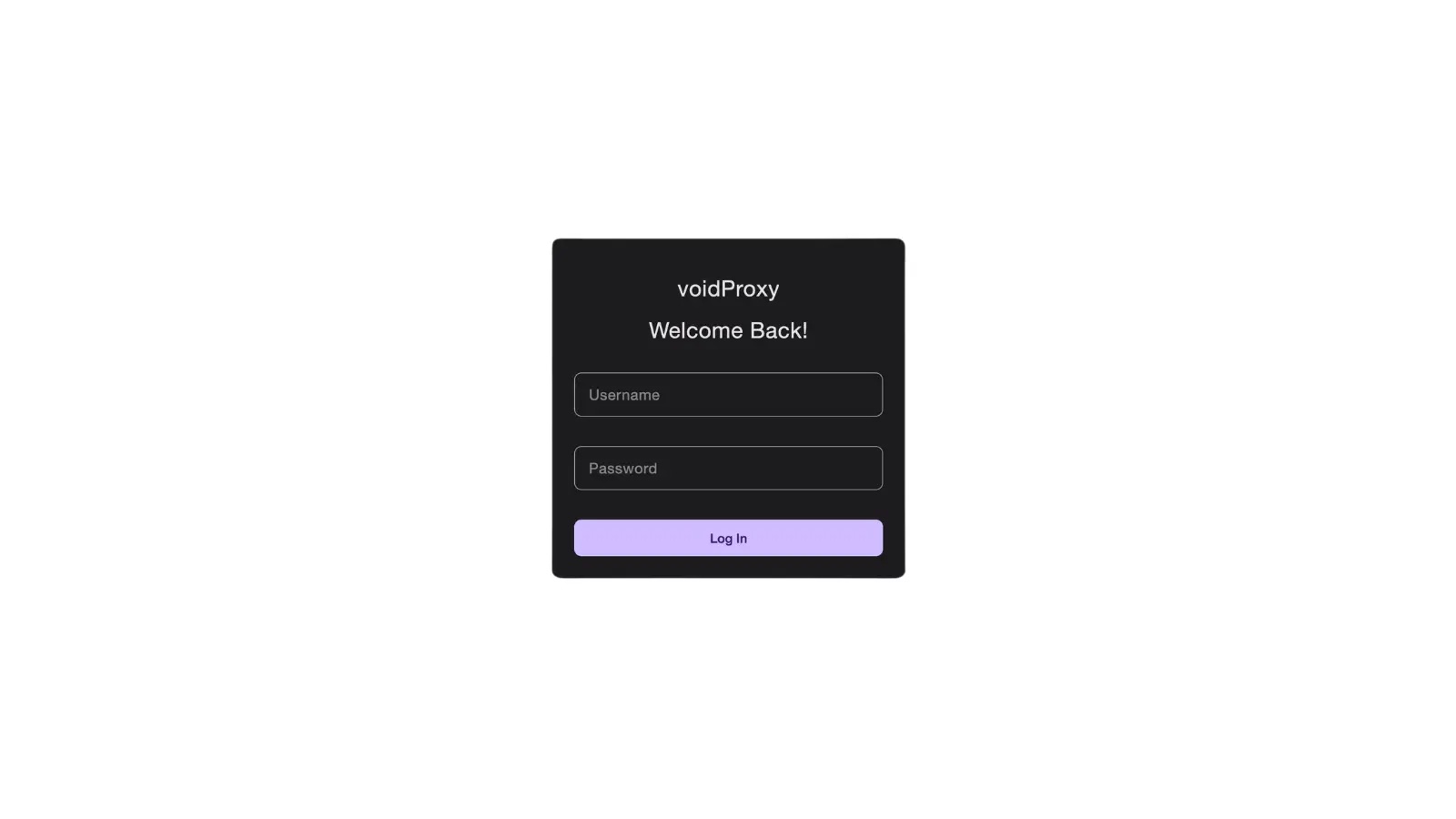
VoidProxy PhaaS Targets Microsoft 365 and Google Accounts in New Campaign
Phishing-as-a-Service operation called VoidProxy that uses advanced adversary-in-the-middle techniques to bypass traditional multi-factor authentication and…
Top 10 Best Web Application Firewall (WAF) Solutions In 2025
Best Web Application Firewall In 2025, web applications are no longer just static websites; they…
FlowiseAI Password Reset Token Vulnerability Enables Account Takeover
A critical vulnerability in FlowiseAI has been discovered that allows attackers to take over user accounts with…