Top 10 Best Privileged Access Management (PAM) Companies in 2025
In an increasingly complex digital landscape, where cloud migrations, remote work, and a distributed workforce…
Windows Users Hit by VenomRAT in AI-Driven RevengeHotels Attack
RevengeHotels, also known as TA558, has escalated its long-standing cybercrime campaign by incorporating artificial intelligence…
APT28 Exploits Signal Messenger to Deploy eardShell and Covenant Malware
Sekoia.io’s Threat Detection and Response (TDR) team has uncovered a sophisticated campaign by APT28 that…
LG WebOS TV Vulnerability Enables Full Device Takeover by Bypassing Authentication
A security vulnerability has been discovered in LG WebOS TV systems that allows attackers to…
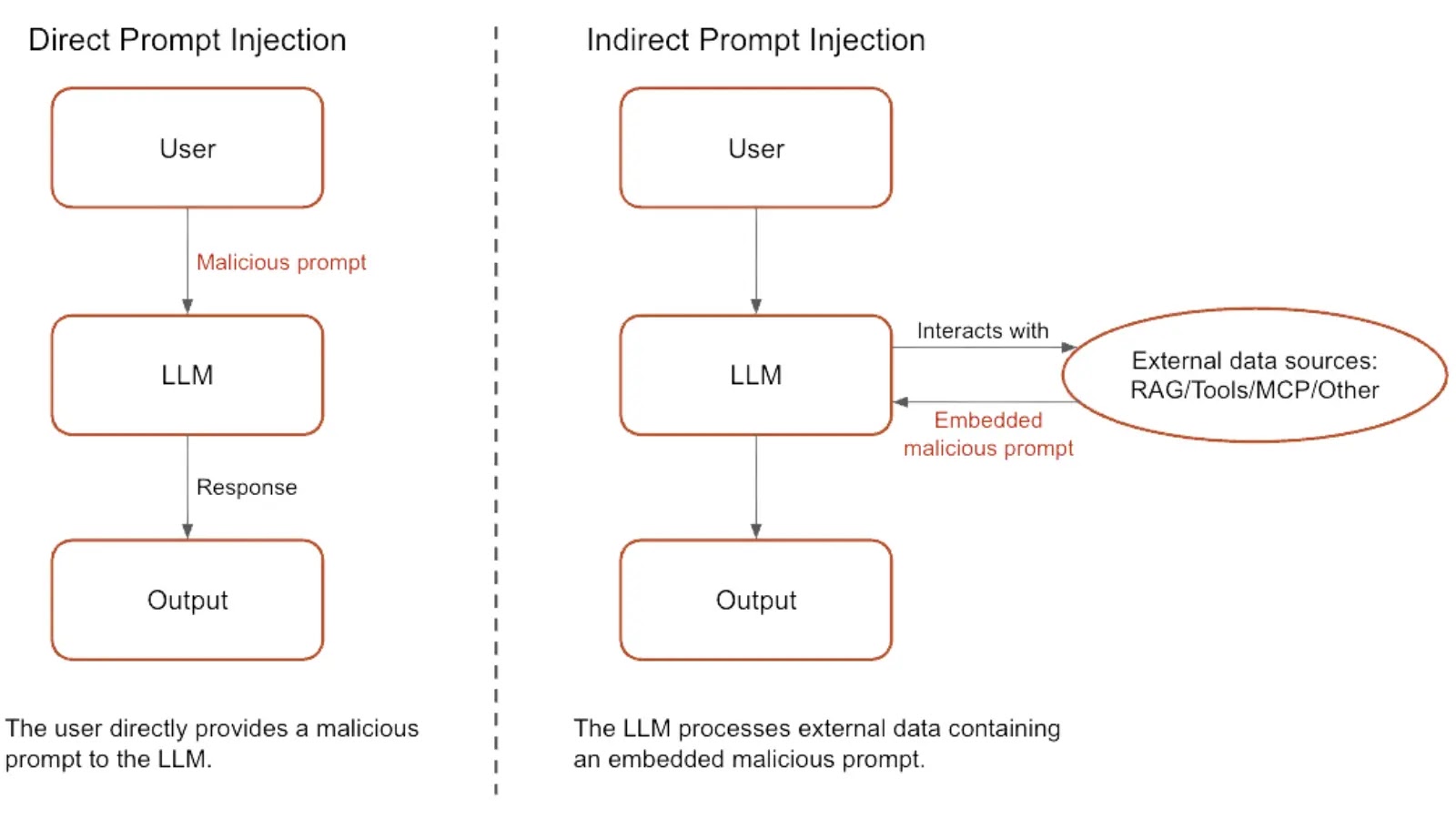
The Hidden Risks of Backdoor Injections
AI code assistants integrated into IDEs, like GitHub Copilot, offer powerful chat, auto-completion, and test-generation…
SmokeLoader Employs Optional Plugins to Steal Data and Launch DoS Attacks
Active since 2011, SmokeLoader (also known as Smoke or Dofoil) has cemented its reputation as…
Threat Actors Exploit MCP Servers to Steal Sensitive Data
Unvetted Model Context Protocol (MCP) servers introduce a stealthy supply chain attack vector, enabling adversaries…
New Persistence Technique Attackers Use to Hide in AWS Cloud Environments
As more companies move their critical systems and data to Amazon Web Services (AWS), attackers…
Top 10 Best MSSP (Managed Security Service Providers) in 2025
In today’s complex digital landscape, the volume and sophistication of cyber threats have outpaced the…
Apple Patches 18 Vulnerabilities in visionOS 26 Allowing Access to Sensitive User Data
Apple has released visionOS 26, addressing eighteen security flaws that could allow unauthorized access to…