Hackers Abuse RTL/LTR Text Tricks and Browser Flaws to Mask Malicious Links
Cybersecurity researchers at Varonis Threat Labs have uncovered a persistent vulnerability that has remained unaddressed…
Agentless Access, Sensitive Data Masking, and Smooth Session Playback
Syteca, a global cybersecurity provider, introduced the latest release of its platform, continuing the mission…
New Magecart Attack Injects Malicious JavaScript to Steal Payment Data
A new Magecart-style campaign has emerged that leverages malicious JavaScript injections to skim payment data…
China-Aligned TA415 Exploits Google Sheets & Calendar for C2
China-aligned TA415 hackers have adopted Google Sheets and Google Calendar as covert command-and-control (C2) channels…
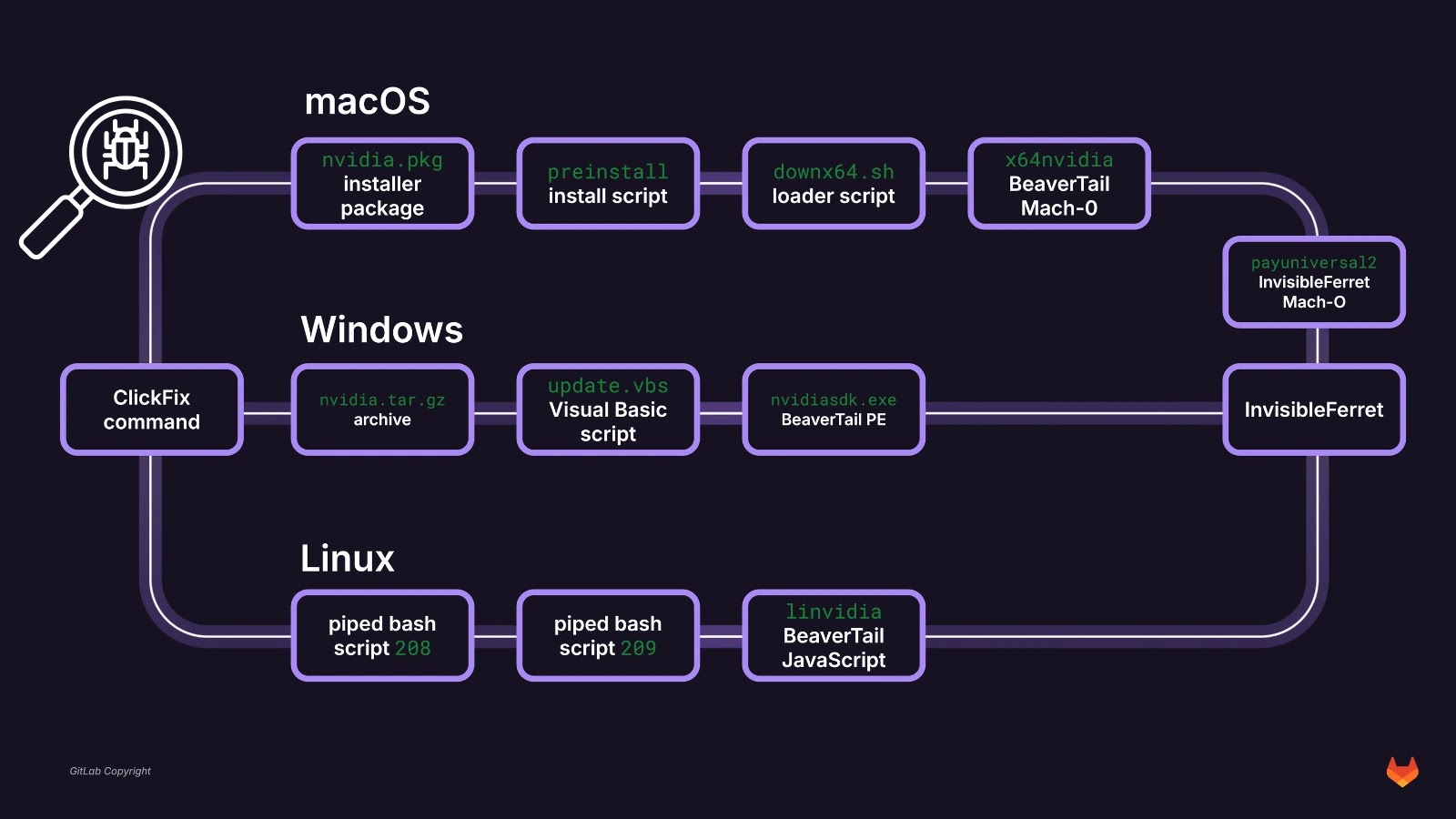
BeaverTail Malware Delivered Through Malicious Repositories Targets Retailers
Tech Note – BeaverTail variant distributed via malicious repositories and ClickFix lure17 September 2025 –…
Microsoft OneDrive Auto-Sync Flaw Leaks Enterprise Secrets from SharePoint Online
A new report from Entro Labs reveals that one in five exposed secrets in large…
MuddyWater Deploys Custom Multi-Stage Malware Hidden Behind Cloudflare
Since early 2025, cybersecurity analysts have witnessed a marked evolution in the tactics and tooling…
Hackers Exploit AdaptixC2, an Emerging Open-Source C2 Tool
In early May 2025, Unit 42 researchers observed that AdaptixC2 was used to infect several…
Chaos Mesh Critical Vulnerabilities Expose Kubernetes Clusters to Takeover
[*] Security Research recently uncovered four new flaws, CVE-2025-59358, CVE-2025-59359, CVE-2025-59360, and CVE-2025-59361, in the…
Apple Patches 0-Day Vulnerabilities in Older iPhones and iPads
Apple has released critical security updates for older iPhone and iPad models, addressing a zero-day…