Microsoft Publishes Guide for Certificate-Based Authentication in Windows Admin Center
Microsoft has released comprehensive guidance for implementing certificate-based authentication in Windows Admin Center (WAC), providing administrators with enhanced security through smart card integration and Active Directory Certificate Services.
This authentication method significantly strengthens access controls by requiring administrators to present valid certificates before accessing the management gateway, effectively adding a strong second authentication factor beyond traditional passwords.
Certificate-Based Authentication Setup
Windows Admin Center interface showing file explorer and file sharing tools within Azure portal environment
Step 1: Prepare Active Directory and Certificate Services
Ensure your environment meets all prerequisites with Windows Admin Center gateway and administrative workstations joined to an Active Directory domain.
Deploy Active Directory Certificate Services (AD CS) as an enterprise Certification Authority that is trusted by the domain for issuing smart card certificates.
Provide administrators with either physical smart cards and readers or configure TPM-backed virtual smart cards capable of storing logon certificates securely.
Replace WAC’s default self-signed gateway certificate with a proper SSL certificate issued by your CA that matches the gateway’s DNS name.
Confirm that domain controllers have valid Kerberos PKINIT certificates and can access Certificate Revocation List distribution points for certificate validation.
Step 2: Configure AD CS Smart Card Logon Template
Create or duplicate a smart card logon certificate template in the Certificate Templates console by duplicating the built-in Smartcard Logon template.
Configure the new template named “IT Admin Smartcard Logon” with strong cryptographic settings including 2048-bit or higher key length and PIN prompting.
Set the Subject Name to build from Active Directory information using the user principal name (UPN) for proper certificate mapping.
Include Smart Card Logon extended key usage (OID 1.3.6.1.4.1.311.20.2.2) and grant Enroll permissions to the administrator group requiring certificates.
Publish the template on your CA and enroll each administrator’s smart card using certmgr.msc, verifying certificate trust relationships.
Step 3: Enable Authentication Mechanism Assurance
Create a universal security group named “WAC-CertAuth-Required” in Active Directory without adding any direct members for AMA control.
Use ADSI Edit to navigate to the Configuration partition under CN=Public Key Services,CN=Services,CN=Configuration and locate the OID container.
Find the object whose msPKI-Cert-Template-OID attribute matches your certificate template’s OID and note the object identifier.

Set the msDS-OIDToGroupLink attribute of that OID object to the distinguished name of your “WAC-CertAuth-Required” group.
This mapping ensures domain controllers dynamically include the group in users’ Kerberos tokens only when authenticated with the smart card certificate.
Step 4: Configure and Test Windows Admin Center
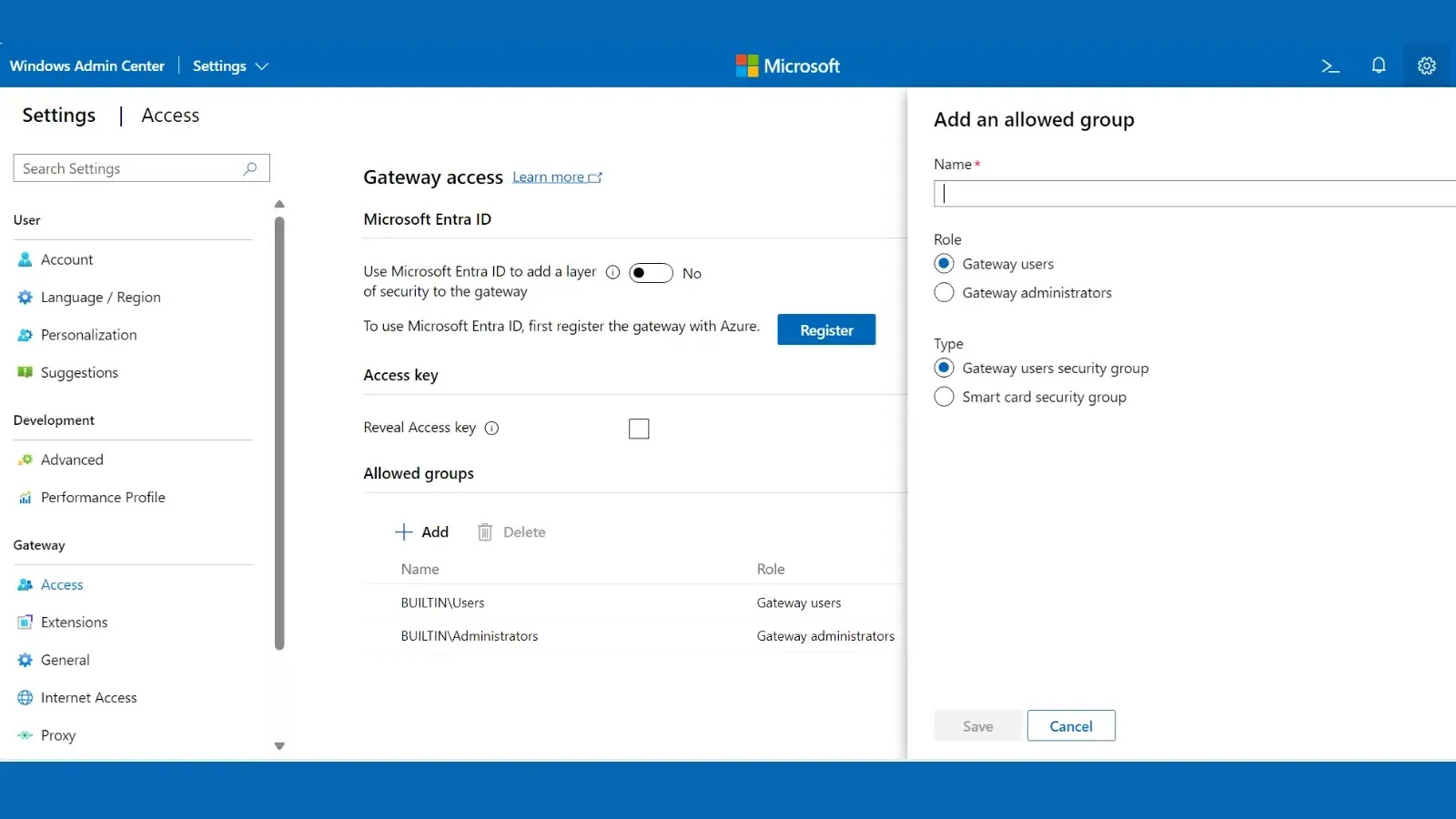
Access the Windows Admin Center Settings panel and configure Active Directory as the identity provider for gateway authentication.
Add your administrative group under User Access to restrict gateway access and specify “WAC-CertAuth-Required” as the smart card-enforced group.
Apply the configuration so WAC requires membership in both the administrative group and the certificate-based authentication group.
Test password-only login attempts which should result in HTTP 401/403 denial, then test smart card certificate login which should grant seamless access.
Validate the setup using whoami /groups to confirm group membership and review WAC event logs for authentication events.
Flowchart illustrating the step-by-step process of certificate-based authentication involving user, certificate authority, keystores, and protected resources
The implementation provides organizations with enterprise-grade security controls for Windows infrastructure management, ensuring that administrative access requires both proper authorization and certificate-based authentication factors.
This comprehensive approach significantly reduces security risks while maintaining administrative efficiency through smart card integration.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.













Post Comment