Fake Job Offers Used to Deliver Advanced Malware Targeting Job Seekers
Iranian threat actors are exploiting job seekers’ aspirations through sophisticated fake recruitment campaigns designed to deploy advanced malware across Europe’s critical infrastructure sectors.
The attack methodology demonstrates remarkable operational security and state-sponsored tradecraft characteristics.
Nimbus Manticore, also known as UNC1549 or Smoke Sandstorm, constructs elaborate fake recruitment websites that impersonate major aerospace companies including Boeing, Airbus, Rheinmetall, and flydubai.
Check Point Research has identified an alarming expansion of operations by Nimbus Manticore, a mature Iran-nexus advanced persistent threat (APT) group, targeting defense, telecommunications, and aerospace organizations with unprecedented sophistication.
These deceptive portals utilize React templates that dynamically adapt to match the branding of targeted organizations, creating convincing replicas of legitimate career pages.
Diagram of the Advanced Persistent Threat (APT) lifecycle highlighting key stages from preparation to cleanup of cyberattack operations
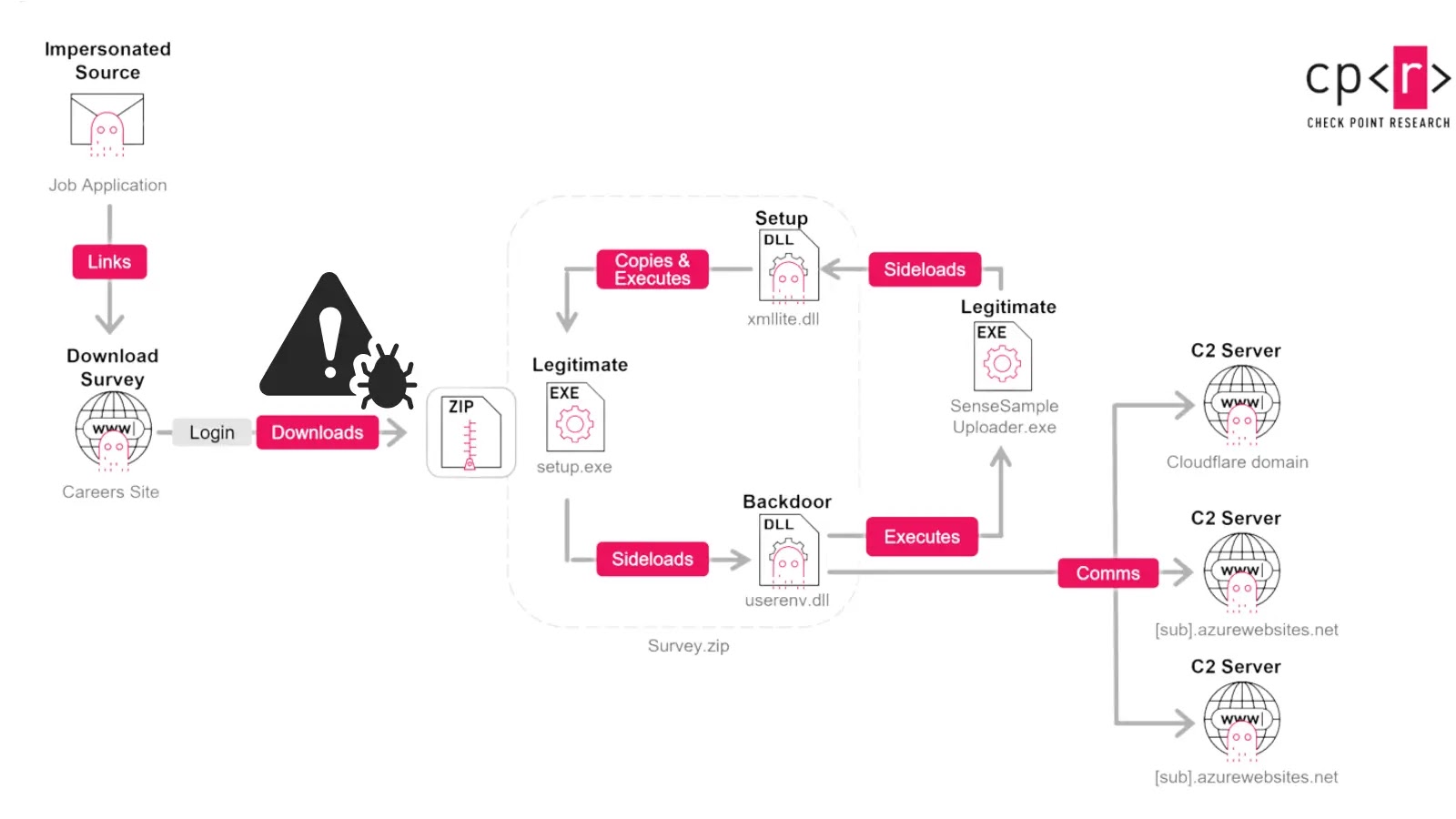
What sets these campaigns apart is their controlled access mechanism. Each potential victim receives unique login credentials in advance through spear-phishing communications.
Only when correct credentials are entered does the malicious site deliver weaponized archives containing advanced malware.
This approach enables attackers to track individual targets while blocking unwanted visitors, demonstrating sophisticated operational awareness typically associated with nation-state actors.
The domain strategy further reinforces the campaign’s credibility, with threat actors registering domains following “career” themes while concealing true hosting infrastructure behind Cloudflare services.

This infrastructure design provides both legitimacy and operational security for sustained espionage activities.
Advanced Malware Arsenal
Nimbus Manticore has significantly evolved its malware capabilities, transitioning from the previously documented Minibike implant to more sophisticated variants including MiniJunk and MiniBrowse.
MiniJunk represents a substantial technical advancement, implementing a previously undocumented technique for loading DLLs from alternate paths by modifying process execution parameters, enabling enhanced evasion of security controls.

Illustration of Iranian cyber threat activities featuring the Iranian flag, binary code, and a keyboard with a hand poised for cyber operations
The malware architecture focuses on dual objectives: long-term persistence and data exfiltration.
MiniJunk maintains covert system access over extended periods, while MiniBrowse specializes in stealing sensitive information without triggering security alerts.
Both tools incorporate continuous updates to evade detection systems and maintain functionality across diverse target environments.
Check Point Research has identified a parallel activity cluster utilizing smaller payloads and simplified techniques while maintaining the same deceptive recruitment strategies.
This secondary campaign demonstrates the threat group’s operational flexibility, adapting technical complexity based on target profiles while preserving core social engineering methodologies.
The campaign represents a significant geographic expansion beyond traditional Middle Eastern targets, with increased focus on Western Europe, particularly Denmark, Sweden, and Portugal.
This expansion aligns with Iranian Revolutionary Guard Corps (IRGC) strategic intelligence collection priorities during periods of heightened geopolitical tension.
Target sector analysis reveals deliberate correlation between fake recruitment portals and intended victims.
Telecommunications-themed portals target satellite providers and communication infrastructure operators, while aerospace-focused sites target defense contractors and aviation companies.
This sector-specific approach maximizes social engineering effectiveness while supporting broader intelligence collection objectives.
Recent campaigns successfully targeted organizations across critical infrastructure sectors, with Check Point Harmony Email & Collaboration blocking attempts against Israeli telecommunications providers, demonstrating the campaign’s active threat landscape presence and wide-ranging targeting scope.
Mitigations
Organizations must implement comprehensive security measures addressing multiple attack vectors simultaneously.
Email security solutions should detect and prevent spear-phishing attempts, fake recruitment portals, and malicious attachments before reaching employees.
Endpoint protection must secure devices against advanced malware deployment, providing defense even when initial email security is bypassed.
Network-level security controls should monitor and block malicious traffic at perimeter boundaries, preventing command-and-control communications and data exfiltration activities.
Employee awareness training focusing on recruitment-themed social engineering attacks becomes crucial given the campaign’s sophisticated impersonation capabilities.
The Nimbus Manticore campaign demonstrates how advanced persistent threat groups adapt and evolve their capabilities to maintain effectiveness against improving defensive measures.
Organizations in defense, telecommunications, and aerospace sectors should implement heightened security postures, recognizing that job-seeking employees represent attractive attack vectors for state-sponsored espionage operations.
This sophisticated campaign underscores the critical importance of treating recruitment communications with appropriate skepticism, particularly when involving requests for credential entry or file downloads.
The intersection of professional networking platforms and cyber espionage creates complex threat landscapes requiring multilayered defensive strategies and continuous threat intelligence awareness.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.













Post Comment