New HTTP Smuggling Technique Allows Hackers to Inject Malicious Requests
Cybersecurity researchers have uncovered a sophisticated HTTP request smuggling attack that exploits inconsistent parsing behaviors between front-end proxy servers and back-end application servers.
This newly discovered technique leverages malformed chunk extensions to bypass security controls and inject unauthorized requests into web applications, representing a significant evolution in HTTP smuggling methodologies.
The attack technique was identified through security research focused on inconsistencies in the HTTP/1.1 protocol.
Following responsible disclosure protocols, security patches have been implemented and deployed across affected systems.
Organizations maintaining current software versions are now protected against this specific attack vector, though the discovery highlights ongoing vulnerabilities in distributed web architectures.
Technical Mechanism Behind the Attack
The exploitation centers on HTTP/1.1’s chunked transfer encoding feature, which allows message bodies to be sent in segments.
According to RFC 9112, each chunk includes a size header in hexadecimal format, potentially followed by optional extensions prefixed with semicolons.
The vulnerability emerges when attackers send malformed chunk extensions containing bare semicolons without proper extension names.
This creates a critical parsing discrepancy between front-end and back-end systems. The front-end parser typically ignores the malformed extension and processes the entire sequence as a single request.
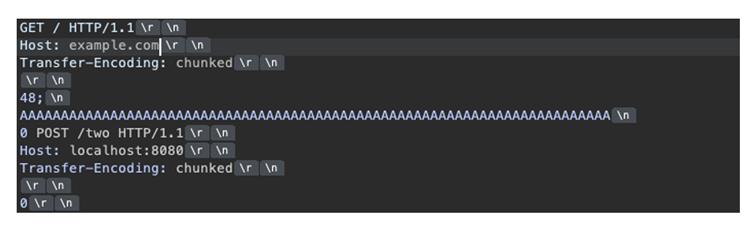
Meanwhile, the back-end parser interprets the newline following the bare semicolon as the end of the chunk header, creating an opportunity for request injection.
The attack follows a precise sequence where attackers craft requests containing chunk size lines ending with semicolons but lacking extension names.
This malformation causes front-end systems to treat subsequent content as part of the original request. However, back-end servers process this content as a separate HTTP request, effectively smuggling unauthorized commands past security controls.
The technique allows attackers to embed secondary requests after fabricated request terminations, potentially accessing restricted endpoints or bypassing authentication mechanisms.
This represents a particularly dangerous form of request smuggling because it can circumvent web application firewalls and other front-end security measures.
This discovery underscores the persistent challenges in HTTP/1.1 implementation consistency across different server technologies.
The protocol’s flexibility in message boundary definition, combined with varying interpretations of RFC specifications, creates opportunities for sophisticated attacks.
Features like chunk extensions, rarely used in practice, often receive inadequate attention during server development, leading to loose or non-compliant implementations.
The vulnerability emphasizes the critical importance of rigorous HTTP request validation and consistent parsing logic across distributed web architectures.
Organizations should prioritize updating affected systems and implementing comprehensive request validation mechanisms to prevent similar attack vectors.
This development represents another reminder that legacy protocol features, particularly those infrequently utilized, can harbor significant security risks when not properly implemented according to established standards.
Find this News Interesting! Follow us on Google News, LinkedIn, and X to Get Instant Updates!














Post Comment