APT36 Hackers Target Indian Railways, Oil, and Government Systems Using Malicious PDF Files
The Pakistan-linked threat group APT36, also known as Transparent Tribe, has broadened its cyber operations beyond traditional military targets to encompass Indian railways, oil and gas infrastructure, and the Ministry of External Affairs.
Security researchers have uncovered two sophisticated desktop-based infection chains leveraging .desktop files disguised as PDF documents, which execute malicious scripts to deploy payloads and establish persistence via cron jobs.
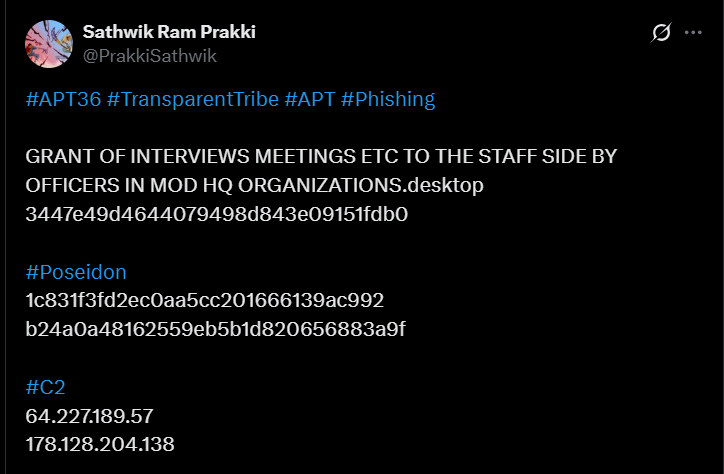
This shift highlights APT36’s adaptation of phishing lures and novel payload strategies, including the deployment of the Mythic-based Poseidon backdoor, to infiltrate broader government and civilian sectors.
The campaign, active since early July 2025, involves over 100 phishing domains impersonating Indian entities, primarily hosted by AlexHost, underscoring a persistent and resilient threat landscape.
Infection Chains
The attack variants exploit .desktop files that mimic legitimate PDFs, such as those themed around government schemes or defense letters, to distract victims while background scripts download malware from remote servers.

In the first variant, a single command-and-control (C2) server at IP 209.38.203.53 facilitates payload retrieval using base64-encoded paths like /dG9nb2pvbW8=/p7zip-full, storing files in hidden directories such as ~/.local/share/ with names blending into system processes (e.g., p7zip-full, tcl-8.7).
According to the Hunt report, persistence is achieved through cron jobs, with decoy content hosted on Google Drive to enhance credibility.
The second variant introduces redundancy with dual C2 servers at 165.232.114.63 and 165.22.251.224, downloading payloads like emacs-bin and crond-98, ensuring operational continuity if one endpoint is disrupted.
Both chains culminate in the Poseidon backdoor, a Go-language implant built on the Mythic C2 framework, enabling cross-platform persistence, system reconnaissance, credential harvesting, and lateral movement.

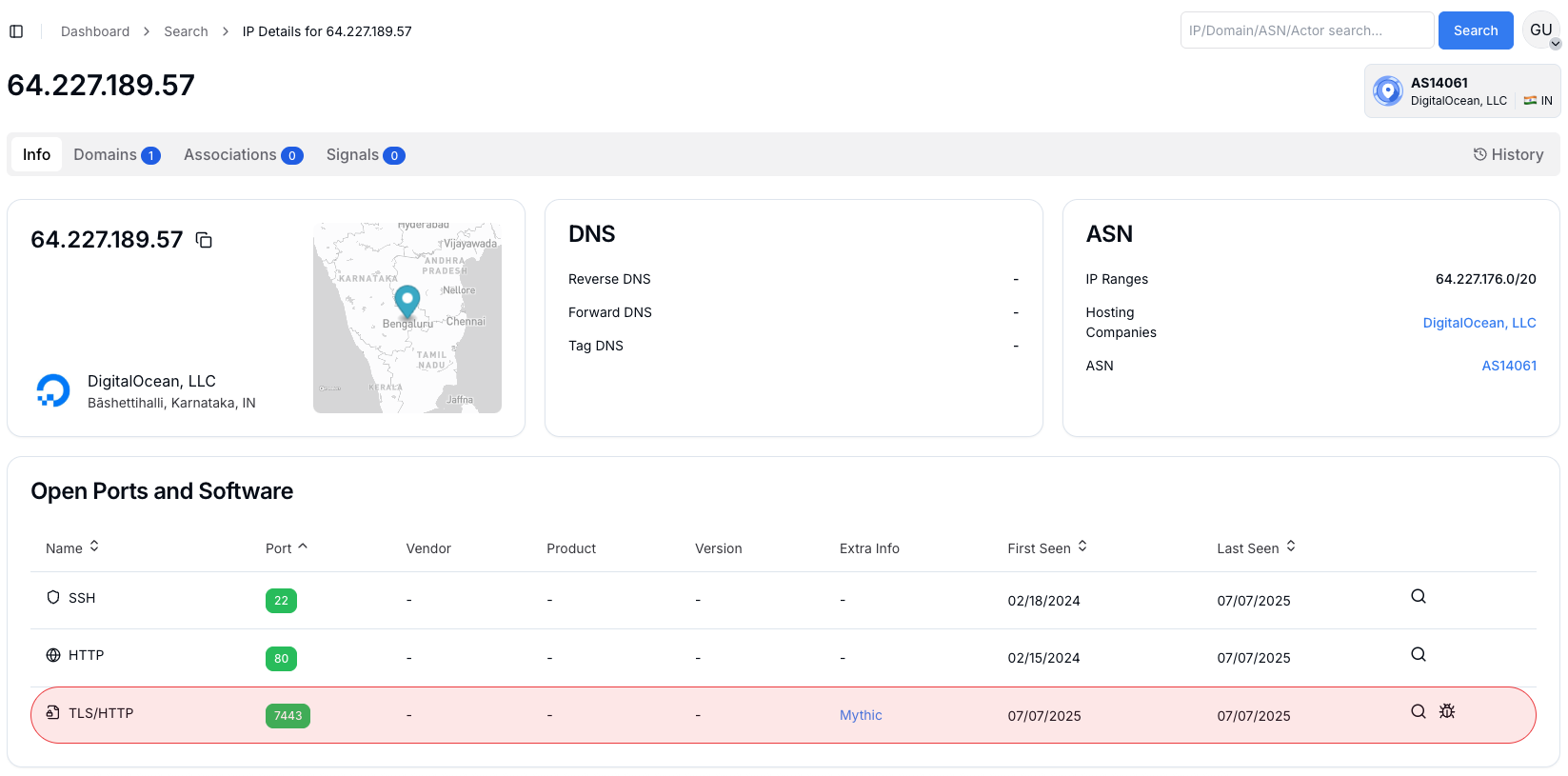
Additional Poseidon C2s at 178.128.204.138 and 64.227.189.57, hosted on DigitalOcean infrastructure in Germany and India, expose port 7443 for Mythic services, confirmed via TLS certificate analysis revealing broader mythic deployments across 352 servers from providers like AWS and ColoCrossing.
Phishing Scale
Complementing malware delivery, APT36’s phishing infrastructure targets credentials through spoofed domains mimicking DRDO, Indian Army, and other entities, often using deceptive subdomains under TLDs like .report or .support, resolving to AlexHost IPs such as 37.221.64.202.
Pivoting from resource hashes has linked over 100 such domains, indicating centralized control and social engineering tailored to Indian public sector users.
This ongoing campaign, first noted in mid-July 2025, combines credential theft with backdoor implantation for sustained access.
Defenders are advised to monitor traffic to identified C2 IPs, detect anomalous .desktop file executions, block AlexHost-resolved spoofed domains, and scan logs for suspicious subdomains.
The evolution of APT36’s tactics from military-focused espionage to critical infrastructure targeting emphasizes the need for enhanced threat hunting, indicator sharing, and proactive blocking to mitigate risks to India’s digital ecosystem.
Indicators of Compromise (IOCs)
| MD5 Hash | Description |
|---|---|
| e354cf4cc4177e019ad236f8b241ba3c | .desktop file used by APT36 to impersonate legitimate documents and deliver payloads; likely initiates persistence and evasion mechanisms. |
| 76e9ff3c325de4f2d52f9881422a88cb | Malicious .desktop file crafted by APT36; contains embedded scripts that delay execution and perform system profiling. |
| 65167974b397493fce320005916a13e9 | APT36 launcher disguised as a document shortcut; designed to run secondary payloads under a legitimate-sounding process name. |
| 6065407484f1e22e814dfa00bd1fae06 | desktop file from APT36; uses long sleeps and debug-environment detection to bypass dynamic analysis. |
| 5c71c683ff55530c73477e0ff47a1899 | APT36 file masquerading as an official form; executes embedded payloads using .desktop execution logic on Linux systems. |
| 8d46a7e4a800d15e31fb0aa86d4d7b7f | Phishing lure dropped by APT36; launches backdoor with anti-analysis and process-masquerading capabilities. |
| 589cf2077569b95178408f364a1aa721 | APT36 .desktop file used for initial compromise; typically includes stealthy execution, sandbox evasion, and optional C2 beaconing. |
| b3f57fe1a541c364a5989046ac2cb9c5 | Malicious shortcut used by APT36 for Linux-based targeting; deploys payloads while evading detection using long sleeps and host checks. |
Find this News Interesting! Follow us on Google News, LinkedIn, and X to Get Instant Updates!














Post Comment