Attackers Exploit BMC Firmware Vulnerabilities to Bypass Signature Verification
In January 2025, Supermicro released patches addressing critical vulnerabilities in its Baseboard Management Controller (BMC) firmware validation logic. Despite these updates, subsequent research has uncovered bypass techniques that undermine signature verification and even compromise the BMC’s Root of Trust (RoT).
Among these, CVE-2024-10237 stemmed from a logical vulnerability in the validation process, allowing malicious firmware images to bypass signature checks and reflash the BMC SPI chip.
Two companion vulnerabilities—CVE-2024-10238 and CVE-2024-10239—resulted from improper parsing of the firmware’s region map, leading to stack-based buffer overflows exploitable for arbitrary code execution within the BMC context.
On January 5, 2025, Supermicro’s security team published an advisory detailing three vulnerabilities in the BMC firmware image authentication design.
Supermicro issued firmware updates intended to block custom table entries and enforce strict region whitelisting during image validation.
In mid-2025, the Binarly Research Team revealed that Supermicro’s patch for CVE-2024-10237 was insufficient. By injecting a malicious region map at a controlled offset and leveraging the firmware’s signature lookup behavior, attackers could still craft images that passed all offset and attribute checks.
This exploit—assigned CVE-2025-7937—permits arbitrary code execution at boot by replacing the original bootloader region with custom content. Supermicro’s PSIRT acknowledged the issue and updated affected firmware versions with revised validation checks.
BMC Firmware Vulnerabilities
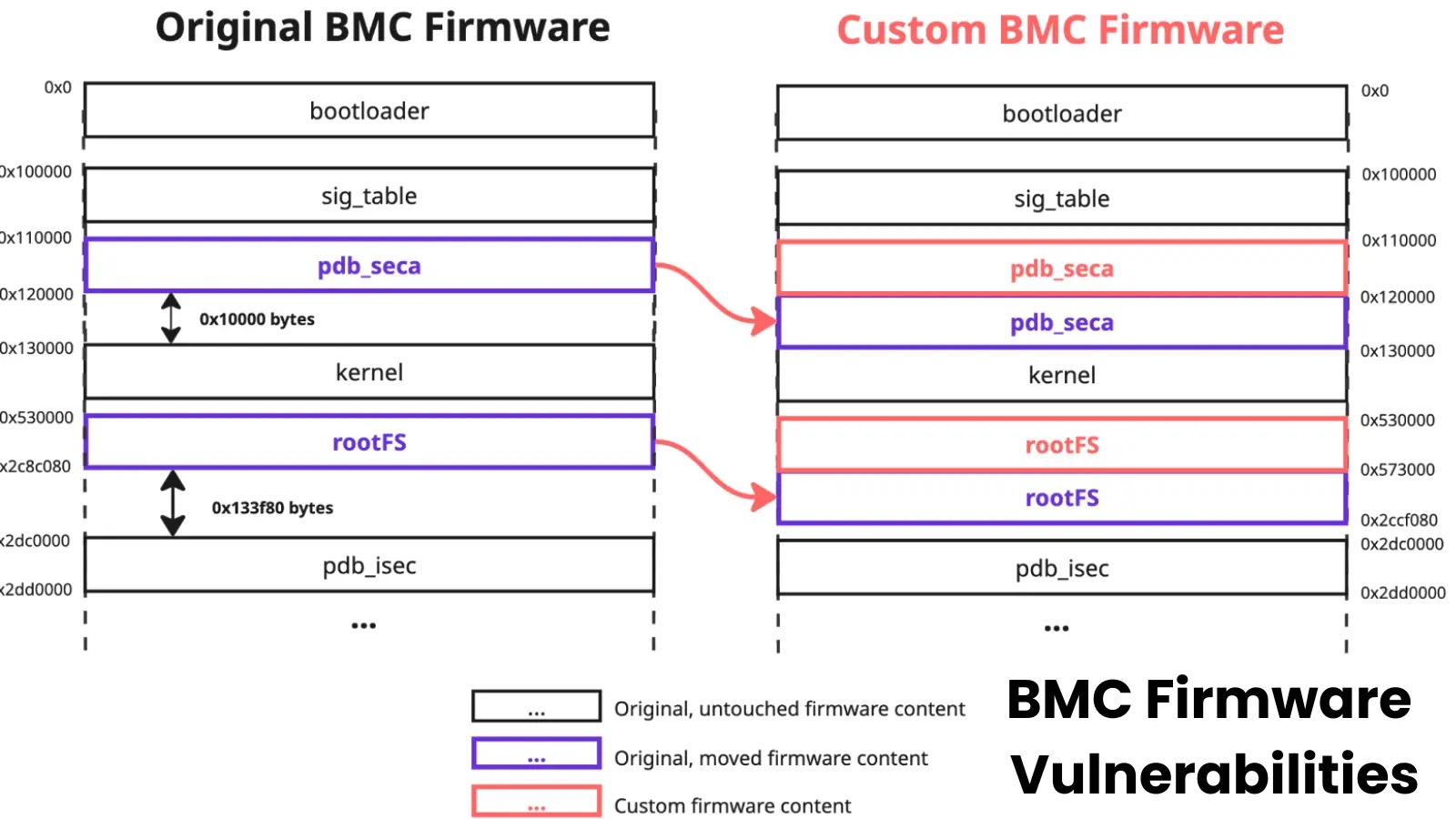
While analyzing different Supermicro motherboards, Binarly researchers discovered a related vulnerability in the X13SEM-F firmware sig_table implementation.

This vulnerability, CVE-2025-6198, arises from the image validation logic running within the OP-TEE secure environment.
By manipulating the sig_table entries, an attacker can move signed regions (such as the kernel) to unused flash areas while inserting malicious code in place of the original data.
Despite RoT measures designed to authenticate firmware during boot, only the initial bootloader is verified; subsequent stages—including the kernel—remain unchecked.
As a result, an attacker with administrative access to the BMC operating system can deploy a specially crafted image that both updates the firmware and bypasses RoT protections. Supermicro confirmed and remediated this vulnerability in its September 2025 firmware release.
Supermicro’s BMC image verification generally follows three steps. First, the public key stored in the SPI flash is retrieved alongside the cryptographic signature embedded in the uploaded image.
The provided fix included the addition of two functions: fwmap_offset_check and fwmap_attr_check.

Next, the firmware’s region table (fwmap or sig_table) is parsed to identify signed areas, and a digest—typically SHA-512—is computed over these regions.
Finally, the digest is verified against the signature using RSA-4096. The bypass techniques exploit the fact that attackers can redefine the region table within the image itself, ensuring that the computed digest matches the original signature despite relocated or tampered content.
Mitigations
Modifications align with all the checks performed: our custom fwmap entry has an allowed name (bootloader), is located at an allowed offset (0x100000) and it is signed.
To defend against these persistent vulnerabilities, administrators should:
Ensure BMC firmware is updated to the latest vendor release, even if previous fixes were incomplete.
Download firmware only from official Supermicro sources and verify file integrity by comparing SHA-256 hashes.
Enable hardware-backed RoT features where supported (e.g., Aspeed AST2600) to strengthen the boot-time trust chain.
Implement continuous monitoring and security audits focused on BMC behavior and firmware integrity.
Binarly’s Transparency Platform provides deep code inspection to detect these low-level threats with high accuracy.
Its integration of Yara rules and proprietary detection engines can identify crafted firmware images before they reach production, offering an additional layer of protection against arbitrary code execution in BMC environments.
Continuous collaboration between researchers, vendors, and users remains essential to safeguard critical infrastructure against evolving firmware-level attacks.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.













Post Comment