RainyDay, Turian and Naikon Malwares Abuse DLL Search Order to Execute Malicious Loaders
Cisco Talos has uncovered a sophisticated, long-running campaign active since 2022 that leverages DLL search order hijacking to deliver a novel PlugX variant with overlapping characteristics of the RainyDay and Turian backdoors.
This operation, targeting telecommunications and manufacturing organizations across Central and South Asia, demonstrates a remarkable convergence of malware functionality and shared infrastructure that links the activities of the Naikon and BackdoorDiplomacy groups.
During in-depth hunting for RainyDay backdoors, Talos analysts discovered that a new PlugX variant abuses the same legitimate Mobile Popup Application executable to sideload its loader into memory.
This technique mirrors the DLL search order hijacking previously used by both RainyDay and Turian. Investigation revealed that all three families employ the same XOR-RC4-RtlDecompressBuffer decryption algorithm and identical RC4 keys to decrypt payloads, underscoring a shared cryptographic toolkit.
Bitdefender has suggested that Quarian, Turian and Whitebird may be different versions of the same backdoor.

Unusually, this PlugX configuration adopts the RainyDay configuration file structure rather than standard PlugX formatting—strongly suggesting the threat actor has access to PlugX source code and has customized it to align with Naikon’s configuration conventions.
RainyDay, Turian and Naikon Malwares
Talos assesses with medium confidence that the campaign is attributable to Naikon, a Chinese-speaking espionage actor active since at least 2010, known for deploying RainyDay, Nebulae, and Aira-body backdoors against government and telecom targets in Southeast Asia.

Despite lacking direct RainyDay or Turian activity during this specific operation, the consistent use of the XOR-RC4 decryption routine, shared RC4 keys, and identical loader behavior across malware families indicates a common developer or supplier.
Historical overlap in victimology—such as telecom entities in Kazakhstan and Uzbekistan—and shared targeting of South Asian networks further hints at Naikon and BackdoorDiplomacy either being the same group or sourcing tools from a single vendor.
Talos’ diamond model comparison highlights that both Naikon and BackdoorDiplomacy focus on telecom and government sectors, utilize similar C2 protocols, and rely on identical loader techniques.
While conclusive linkage remains elusive, the convergence of loader code, PDB path similarities, and encryption keys point to a connected infrastructure underpinning multiple malware families.
The initial infection chain begins with a malicious document or email lure, followed by execution of a legitimate signed binary vulnerable to DLL search order hijacking.
Once the loader is in place, it reads an encrypted shellcode file—”rdmin.src” for RainyDay, “Mcsitesdvisor.afx” for PlugX, and “winslivation.dat” for Turian—from the same directory.

The loader resolves its own path with GetModuleFileNameA, decrypts the shellcode via XOR, then applies RC4 and LZNT1 decompression to unpack the payload into memory.
RainyDay and PlugX inject directly into the calling process, while Turian launches a fresh process (wabmig.exe or explorer.exe) to host its payload.

PDB paths embedded in loader binaries reveal developer project names and timestamps—for example, “3-2hao-211221” in Turian samples, and “MicrosoftEdge Update” paths in RainyDay and PlugX loaders—suggesting a shared development environment and toolchain.
Notably, Turian loader PDB strings reference a Chinese term meaning “provide web version,” indicating a custom web-based ICMP shell component.
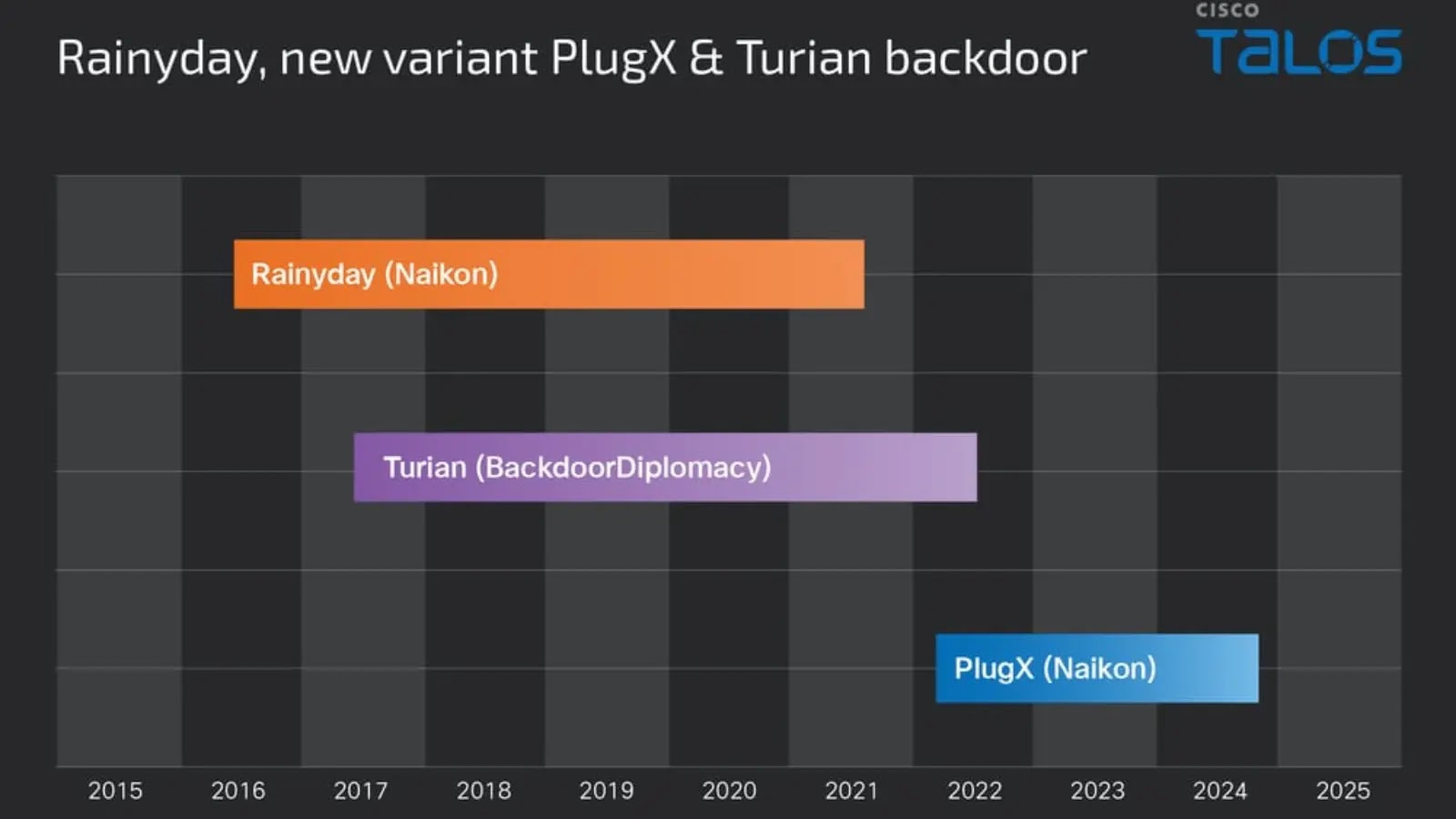
Talos analysts also mapped a timeline of intrusion activity spanning from 2016 through 2024, encompassing older RainyDay variants, the emergence of the PlugX variant in 2022, and Turian activity aligned with BackdoorDiplomacy campaigns. This chronology underscores the persistent evolution and continuous operation of the threat actor.
Mitigations
Organizations in Asia’s telecommunications and manufacturing sectors should prioritize solutions capable of detecting DLL search order hijacking and anomalous loader behaviors.
Cisco Secure Endpoint blocks malicious sideloaded DLLs by verifying digital signatures and monitoring process creation. Secure Email and Secure Firewall appliances can intercept phishing lures and block malicious binaries.
Network analytics tools such as Stealthwatch detect unusual RC4-decompression traffic patterns, while Threat Grid provides sandbox analysis for identifying these specialized loaders.
Implementing strict application whitelisting and enforcing proper DLL search order controls will further mitigate this class of attack. Continuous threat hunting for files named “rdmin.src,” “Mcsitesdvisor.afx,” and “winslivation.dat” can reveal early indicators of compromise.
By understanding the shared infrastructure and cryptographic routines across RainyDay, Turian, and PlugX, defenders can enhance detection signatures and disrupt the supply chain of this versatile threat actor.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.













Post Comment