Threat Actors Breach Enterprise Infrastructure Within 18 Minutes of Initial Access
Attackers are accelerating their foothold in corporate networks: over the past three months (June 1 to August 31, 2025), the average time from initial breach to lateral movement—called “breakout time”—fell to just 18 minutes.
In one striking incident, “Akira” ransomware operators moved laterally in only six minutes after compromising a SonicWall VPN. This rapid pace underscores the urgent need for organizations to close detection gaps and automate response processes.
Drive-by compromises remained the leading entry point at 34% of incidents, fueled by an active “Oyster” (aka Broomstick) campaign.
Oyster operators leverage SEO poisoning and malvertising to lure victims to trojanized IT-tool download sites such as “puttysystems[.]com.”
Those sites deliver backdoors via malicious DLLs (e.g., twain_96.dll), then execute them using trusted Windows binaries like Rundll32.exe for stealth and persistence.
This section dives into select MITRE tactics and techniques, revealing the latest trends in attacker methods and the driving forces behind their popularity.

While drive-by compromise remains the dominant initial access tactic, USB-based attacks are surging, with incidents linked to “Gamarue” malware on the rise.
SMB Abuse Surges to 29% for Lateral Movement
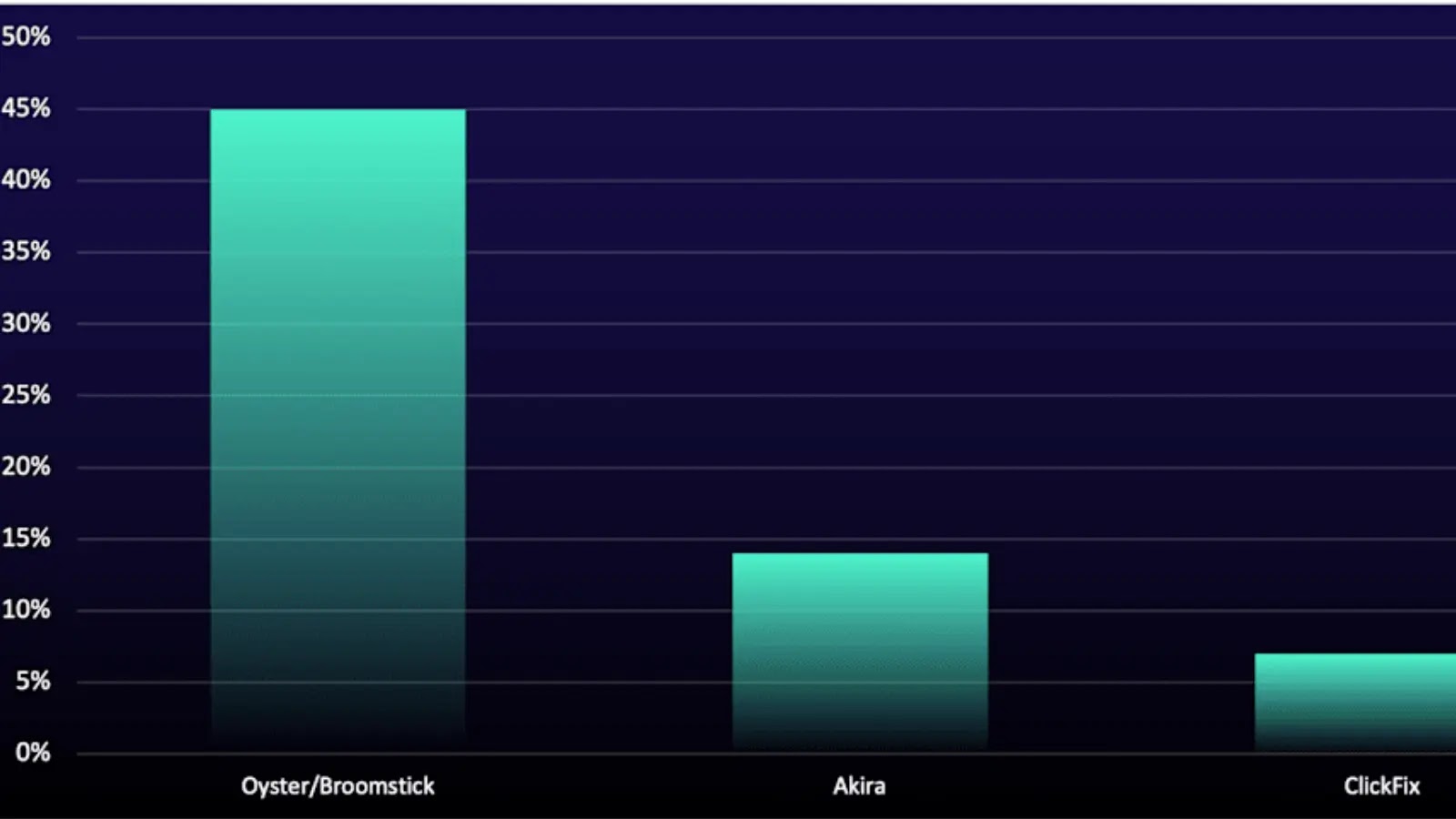
Oyster accounted for 45% of true-positive incidents this period, up sharply from 2.17% last quarter. The campaign’s automated SEO poisoning illustrates how AI and automation enable threat actors to scale and refine attacks with minimal manual effort.

While RDP remains the top lateral-movement technique—used in over 50% of cases—SMB-based ransomware operations nearly tripled from 10% to 29%.
Ransomware families such as Akira exploit compromised credentials to access network file shares and perform remote encryption.
By using SMB, attackers bypass endpoint defenses entirely, quietly encrypting data on file servers.
In one Akira incident, operators noted remote encryption within 19 minutes of initial login. These tactics reveal a critical vulnerability in endpoint-focused security: attacks that bypass endpoints demand network-level protections and continuous monitoring of file-share activity.
Unauthorized keyboard, video, and mouse over IP (IP-KVM) devices surged by 328% this reporting period.
These hardware tools, often deployed in high-security or air-gapped environments, create out-of-band access paths that evade traditional EDR solutions.
Nation-state actors (56.7% of cases) leverage IP-KVMs like TinyPilot to infiltrate networks where endpoint visibility is limited.
Even accidental insiders introduce risks when they use IP-KVMs to bypass corporate controls. One August case saw a JetKVM device mounted twice on a workstation, enabling external attackers to reboot servers, install backdoors, and exfiltrate data—all undetected until hardware-level monitoring kicked in.
Automation and AI are reshaping the threat landscape. GLOBAL ransomware now offers an AI-powered negotiation chatbot and mobile management panel for affiliates, while Oyster’s SEO poisoning is fully automated to spin up convincing fake pages at scale.
Ransomware activity saw a 4.52% decline in overall victims listed on data-leak sites this reporting period. Akira, “SafePay,” and “Play” experienced slower growth, with victim counts falling by 9.42%, 23.14%, and35.54% respectively.

These innovations shorten reaction windows and increase precision, forcing defenders to adopt complementary automation for detection and containment. Organizations using ReliaQuest GreyMatter’s automated containment saw mean time to contain (MTTC) drop from 11.99 hours to 4.49 minutes.
Overlooked Vulnerabilities
Despite novel AI-driven tactics, many successful breaches exploit unpatched or misconfigured systems rather than zero-day vulnerabilities.
Akira exploited a known SonicWall VPN vulnerability (CVE-2024-40766) to achieve a six-minute breakout. Qilin targeted Fortinet FortiGate vulnerabilities (CVE-2024-55591 and CVE-2024-21762) to breach 26 utilities companies this period.
Infostealer activity declined overall due to Lumma’s May takedown, but Lumma rebounded as attackers distributed it via cracked software and “ClickFix” phishing lures.
New stealers—Acreed, Vidar, and Stealc—are diversifying credential-theft methods, emphasizing the need for robust SaaS and cloud controls.
To outpace today’s fastest-moving adversaries, organizations must:
- Harden USB policies by disabling autorun, enforcing device allowlists, and deploying endpoint monitoring to block Gamarue-style infections.
- Enforce MFA and network-level monitoring on RDP and SMB sessions to detect anomalous access and remote-encryption activity.
- Deploy real-time hardware-monitoring solutions (e.g., Armis) and network access control to detect unauthorized IP-KVM devices.
- Restrict software downloads to a company-controlled portal and monitor IT-tool usage to block trojanized binaries signed with stolen certificates.
- Automate detection and response workflows to reduce containment times to minutes, not hours.
In an era when threat actors can pivot from breach to network-wide compromise in under 20 minutes, rapid detection, automated response, and airtight security hygiene are the only ways to stay ahead.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.













Post Comment