How HR Representatives Can Engage Employees to Steal Login Credentials
Subtle Snail, an Iran-linked espionage group also tracked as UNC1549 under the Unyielding Wasp (Tortoiseshell) umbrella of the Charming Kitten network, has shifted its focus to European telecom, aerospace, and defense firms since June 2022.
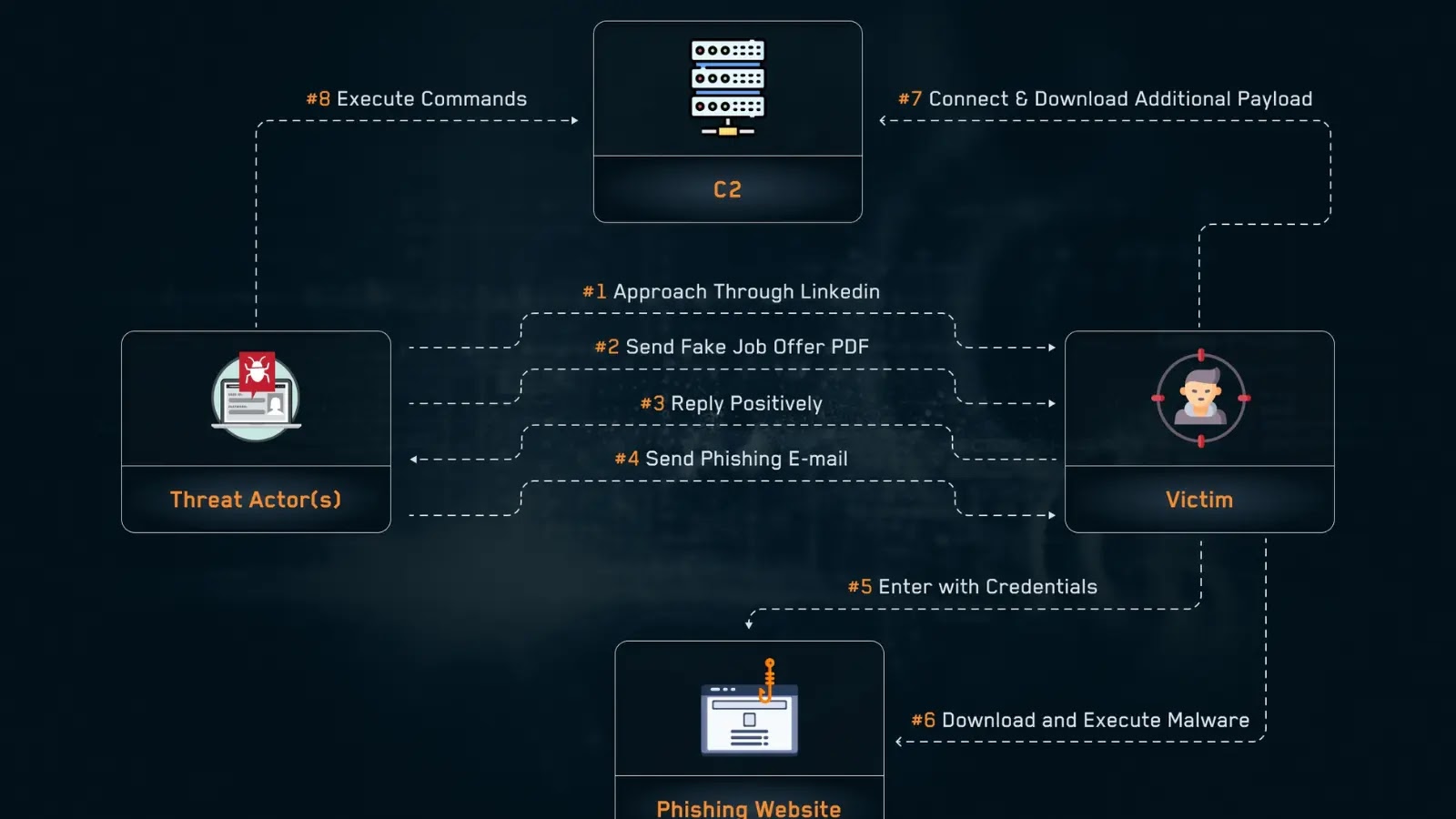
In a recent wave of attacks, the group compromised 34 devices across 11 organizations by masquerading as human resources representatives on LinkedIn.
Victims were lured into fake recruitment processes, downloaded a customized MINIBIKE backdoor payload, and unwittingly granted the attackers persistent, stealthy access to corporate networks.
The operation underscores a rising trend of tailored social engineering exploits that bypass traditional security controls by blending espionage tradecraft with legitimate cloud services.
Subtle Snail’s campaign begins with extensive reconnaissance of target organizations. Attackers map out corporate hierarchies and identify employees in IT, development, or research roles through public platforms like LinkedIn.
Their primary goal is long-term intelligence gathering in telecommunications, with side interests in aerospace and defense.

Profiles are created to resemble real HR professionals at respected companies, complete with authentic-looking domains such as telespazio-careers.com and safrangroup-careers.com. Once a match is identified, prospects receive LinkedIn messages inviting them to apply for bespoke job openings.

These messages include a tailored PDF job advertisement and a link to a faux applicant portal. When candidates submit their credentials on these impersonated login pages, the credentials are harvested directly by the group’s C2 infrastructure, proxied through Azure services to blend malicious queries with legitimate cloud traffic.
Delivery and Execution of MINIBIKE
After credential capture, the victim is prompted to download an archive—commonly named Application.zip or TimeScheduler.zip—which contains a digitally signed setup.exe and a malicious DLL.
The victim then closes the document and clicks on the malicious website to begin the application process, where they fill out all of their information.

According to Report, Subtle Snail procures valid code-signing certificates through SSL.com and Insight Digital B.V., allowing the payload to evade antivirus detection.
When the victim executes the setup file, Windows’ DLL search-order hijacking loads the side-loaded MINIBIKE DLL instead of the legitimate library.
This primary backdoor variant decrypts critical strings at runtime via XOR-based routines, collects system identifiers, and establishes an HTTP-based C2 channel using Azure-hosted domains that mirror legitimate web services.
Once inside the network, Subtle Snail deploys a suite of victim-specific modules for keylogging, browser credential theft, screenshot capture, and Outlook/Winlogon credential prompts.
Each module is packaged as a uniquely tailored DLL and executed via DLL sideloading, ensuring seamless operation under trusted processes like DataExchangeHost.exe or BioIso.exe.
Keystrokes and browser-stored credentials from Chrome, Edge, and Brave are encrypted and staged in local log files, then exfiltrated in 1–5 MB chunks via the same Azure-proxied C2 channels.
Persistence is maintained through Registry Run Keys and the abuse of Background Intelligent Transfer Service for file staging.
Custom tools such as AddMachineAccount.exe facilitate Active Directory manipulation, while runtime.dll gathers network details for ongoing lateral movement.
Stealth Techniques and Strategic ObjectiveTo evade analysis, the group employs control-flow flattening, dynamic API resolution, anti-sandbox checks, and timing-based anti-debugging.
Malicious binaries verify their loader process names to avoid execution in generic environments and delete logs after operations via C2 commands.
This high level of operational security enables Subtle Snail to remain undetected for extended periods, consolidating footholds within target environments.
Their primary goal is long-term intelligence gathering in telecommunications, with side interests in aerospace and defense.
By harvesting VPN configurations, project files, and executive communications, the group aims to build a comprehensive dossier for strategic espionage.
As enterprises bolster cloud-based defenses and adopt administrator protection features in Windows 11, Subtle Snail’s reliance on LinkedIn-driven social engineering and legitimate cloud proxies highlights the need for comprehensive user-education programs and advanced threat hunting capabilities.
Organizations should validate all recruitment communications, enforce multi-factor authentication on external portals, and monitor anomalous Azure service usage to guard against these sophisticated espionage campaigns.
Find this Story Interesting! Follow us on LinkedIn and X to Get More Instant Updates.













Post Comment