Inboxfuscation Tool Bypasses Exchange Inbox Rules and Evades Detection
Advanced persistent threat actors increasingly target Microsoft Exchange inbox rules to maintain persistence and siphon sensitive data without raising alarms.
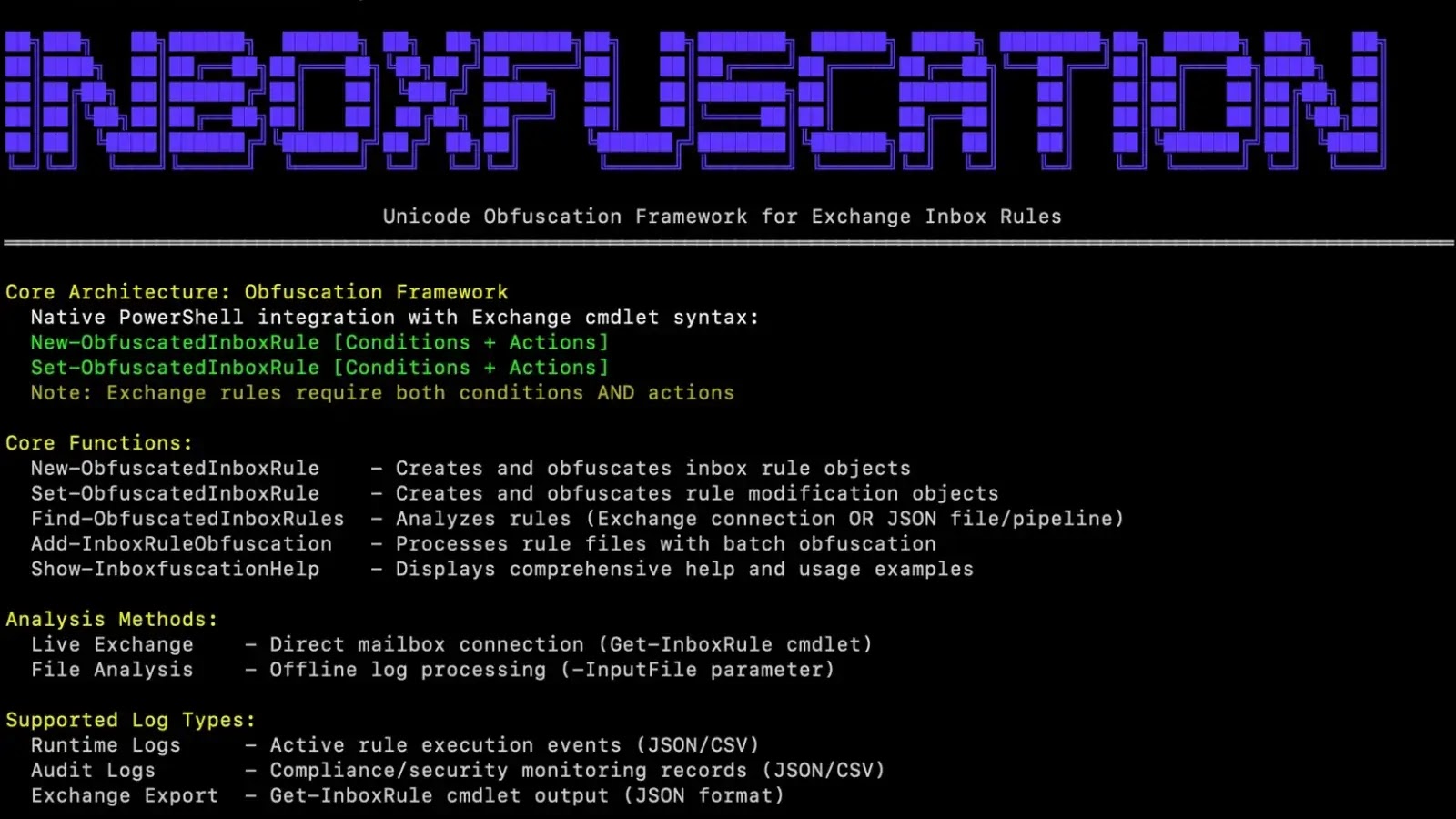
The newly released Inboxfuscation tool delivers a Unicode-based obfuscation framework capable of generating malicious inbox rules that slip past conventional monitoring solutions.
By exploiting Exchange’s handling of diverse Unicode character sets, Inboxfuscation crafts visually deceptive rule definitions and leverages hidden characters and bidirectional controls to cloak malicious behaviors from both human operators and automated scanners.
The Unicode Obfuscation Revolution
Traditional inbox rule attacks rely on clear-text keywords such as “password,” “admin,” or “confidential” to identify and intercept malicious configurations.
However, the vast Unicode character space encompassing over 140,000 distinct code points enables attackers to substitute visually identical symbols, inject zero-width characters, or manipulate text directionality to thwart detection.

Inboxfuscation’s framework categorizes these obfuscation methods into four primary techniques: character substitution using mathematical alphanumeric symbols and enclosed variants; zero-width injection that intersperses invisible code points within keywords; bidirectional text controls that reverse or confuse rendering order; and hybrid combinations of multiple evasion methods.
Each approach transforms rule conditions in a way that appears benign or inscrutable when viewed in standard consoles yet still executes against the intended mailbox content.
Although these techniques have not been observed in active campaigns to date, hypothetical attack models illustrate the potential impact.
In a simulated advanced persistent threat operation targeting executive communications, attackers could deploy a rule named “Executive Communications Archive” with subject filters such as “𝚋𝗈𝒂𝗋𝒹” and “𝖒𝖊𝖊𝗍𝗂𝗇𝗀,” moving messages to the internal Calendar folder and forwarding copies to an attacker-controlled address disguised as a legitimate backup system.

This configuration appears routine to administrators yet effectively exfiltrates and hides sensitive correspondence.
In an anti-forensics scenario, adversaries might create a rule labeled “System Optimization” that silently redirects security alerts to a visually identical “:\Inbox ” folder, leveraging trailing whitespace to evade discovery and halting further rule processing to suppress notifications.
Standard security tools falter against Unicode-based obfuscation due to reliance on ASCII pattern matching and simplistic keyword rules.
Inboxfuscation addresses these blind spots with a multilayered detection methodology. The framework performs character category analysis to flag mathematical alphanumeric symbols, zero-width code points, bidirectional controls, and enclosed alphanumerics.
It processes Exchange export logs, SIEM-integrated audit records, and Graph API events to reconstruct rule creation sequences and compute risk scores.
Immediate response actions include comprehensive mailbox audits using Find-ObfuscatedInboxRules -Mailbox, as well as retrospective analysis of audit logs filtered by elevated risk thresholds.
The tool outputs structured JSON suitable for SIEM ingestion, detailing rule identifiers, mailbox targets, obfuscated keywords, Unicode character counts, and external forwarding flags.
Organizations should integrate Unicode-aware detection pipelines and conduct proactive red-teaming exercises using Inboxfuscation to simulate evasion techniques.
Security teams must update incident response playbooks to account for hidden characters and normalize rule attributes when performing forensic reviews.
While Unicode obfuscation remains a theoretical threat, its technical feasibility underscores the importance of evolving email security postures before adversaries weaponize these methods.
Find this Story Interesting! Follow us on LinkedIn and X to Get More Instant Updates.













Post Comment