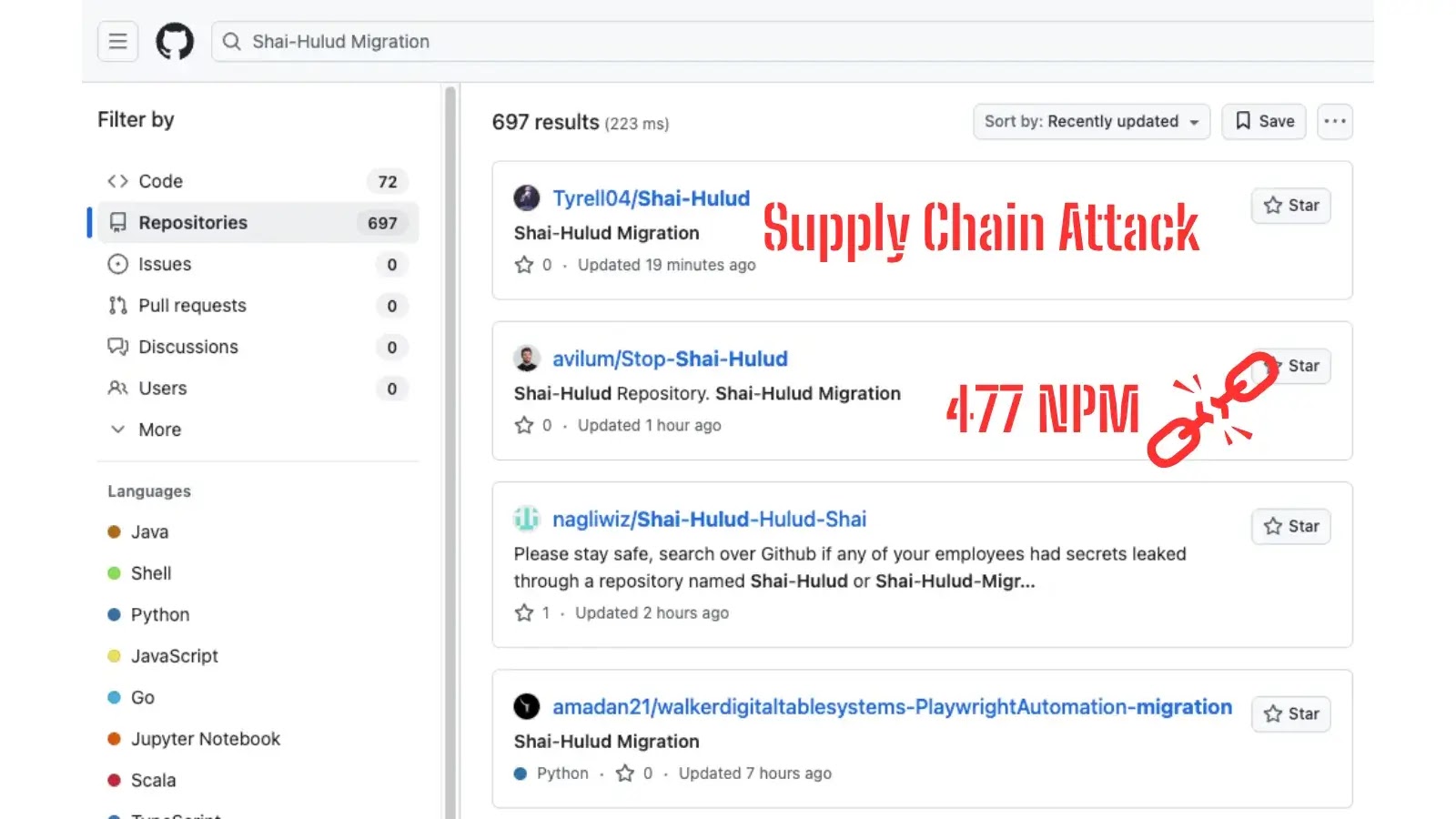
Supply Chain Attack “Shai-Halud” Targets 477 NPM Packages
A major supply chain attack dubbed “Shai-Halud” has impacted the JavaScript ecosystem by targeting over 477 NPM packages, raising serious concerns among developers and organizations relying on software from the Node Package Manager (NPM) registry.
This incident reveals both the scale and sophistication of modern threats to open-source software and highlights the urgent need for improved security measures within the development community.
Attack Details and Targets
The Shai-Halud campaign was first detected by security researchers who identified suspicious activities linked to CrowdStrike-related NPM packages.

The attackers gained unauthorized access to trusted publisher accounts, allowing them to upload malicious code to hundreds of legitimate packages hosted on NPM.

Some of the compromised packages include crowdstrike-sdk, crowdstrike-client, crowdstrike-api, and several others commonly used for integrating CrowdStrike functionality into security and automation solutions.
| Package Name | Affected Version |
| @crowdstrike/commitlint | 8.1.1 |
| @crowdstrike/commitlint | 8.1.2 |
| @crowdstrike/falcon-shoelace | 0.4.1 |
| @crowdstrike/falcon-shoelace | 0.4.2 |
| @crowdstrike/foundry-js | 0.19.1 |
| @crowdstrike/foundry-js | 0.19.2 |
| @crowdstrike/glide-core | 0.34.2 |
| @crowdstrike/glide-core | 0.34.3 |
| @crowdstrike/logscale-dashboard | 1.205.1 |
| @crowdstrike/logscale-dashboard | 1.205.2 |
| @crowdstrike/logscale-file-editor | 1.205.1 |
| @crowdstrike/logscale-file-editor | 1.205.2 |
| @crowdstrike/logscale-parser-edit | 1.205.1 |
| @crowdstrike/logscale-parser-edit | 1.205.2 |
| @crowdstrike/logscale-search | 1.205.1 |
| @crowdstrike/logscale-search | 1.205.2 |
| @crowdstrike/tailwind-toucan-base | 5.0.1 |
| @crowdstrike/tailwind-toucan-base | 5.0.2 |
Researchers found that the attackers leveraged automation tools to rapidly inject rogue packages into the registry, exploiting weak account protection and inadequate oversight.
Evidence suggests that this was a coordinated, large-scale operation that specifically sought out packages referenced in enterprise environments.
Once installed, the infected packages were capable of executing post-installation scripts designed to exfiltrate environment variables and secrets.
By targeting CI/CD pipelines and development environments, the attackers aimed to steal sensitive authentication tokens, cloud credentials, and configuration files.
This approach enabled them to gain persistent access to internal networks, potentially compromising business-critical applications and data.
Security experts have warned that since NPM packages are widely reused and often have a sprawling dependency tree, the ripple effects of supply chain attacks like Shai-Halud can be vast.
If a single package is compromised, every application and library depending on it may become vulnerable.
The NPM registry and security partners rapidly worked to identify and remove the malicious packages after discovery.
Affected publishers were notified, and guidance was provided for auditing and updating dependencies.
Developers using CrowdStrike integrations or similar NPM packages should immediately review their dependency lists, remove any flagged packages, and reset credentials for potentially exposed environments.
This attack serves as a clear warning for the broader software supply chain. Experts recommend enforcing multi-factor authentication for publisher accounts, monitoring package integrity, and using automated scanning tools to detect suspicious activity.
Maintaining vigilance against supply chain manipulation is now a critical responsibility for every organization relying on open-source libraries.
Find this Story Interesting! Follow us on LinkedIn and X to Get More Instant Updates.










Post Comment